Source: thehackernews.com – Author: . Jun 13, 2023Ravie LakshmananCyber Crime / Cryptocurrency The U.S. Department of Justice (DoJ) has charged two Russian nationals in connection with...
Month: June 2023
Critical FortiOS and FortiProxy Vulnerability Likely Exploited – Patch Now! – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 13, 2023Ravie LakshmananNetwork Security / Vulnerability Fortinet on Monday disclosed that a newly patched critical flaw impacting FortiOS and FortiProxy...
Expel Lays Off 10% of Workers 8 Months After Hauling in $31M – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Managed Detection & Response (MDR) , Security Operations 60 Staffers Axed Months After Expel Slowed Hiring to Reduce Likelihood of Layoffs...
Another Healthcare Vendor Reports Big Forta GoAnywhere Hack – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 3rd Party Risk Management , Governance & Risk Management , Healthcare Debt Collection Software Firm Intellihartx Says Nearly 490,000 Affected by...
OnDemand Webinar: Start Gathering Your Own Threat Intelligence – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development , Ransomware See how deception technology offers clear signals in all...
New OnDemand Webinar: Taking Insider Risk Management to the Next Level – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development , Social Engineering June 12, 2023 Insider threats can...
Fortinet: New FortiOS RCE bug “may have been exploited” in attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Fortinet says a critical FortiOS SSL VPN vulnerability that was patched last week “may have been exploited” in attacks impacting...
Have I Been Pwned warns of new Zacks data breach impacting 8 million – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Zacks Investment Research (Zacks) has reportedly suffered an older, previously undisclosed data breach impacting 8.8 million customers, with the database...
Microsoft: Azure Portal outage was caused by traffic “spike” – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft revealed in an update to the Azure status page that the preliminary root cause behind an outage that impacted...
Exploit released for MOVEit RCE bug used in data theft attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Horizon3 security researchers have released proof-of-concept (PoC) exploit code for a remote code execution (RCE) bug in the MOVEit Transfer...
Swiss government warns of ongoing DDoS attacks, data leak – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Swiss government has disclosed that a recent ransomware attack on an IT supplier might have impacted its data, while...
Business email compromise scams take new dimension with multi-stage attacks – Source: www.csoonline.com
Source: www.csoonline.com – Author: A new attack group leverages trusted relationships between partner organizations to bypass multifactor authentication. In a campaign that exploits the relationships between...
To solve the cybersecurity worker gap, forget the job title and search for the skills you need – Source: www.csoonline.com
Source: www.csoonline.com – Author: CISOs who focus on identifying job candidates with the skills they need are finding talent from other fields and functions to help...
Cycode’s free CI/CD monitoring tool offers new DevOps visibility – Source: www.csoonline.com
Source: www.csoonline.com – Author: An eBPF-based tool for code monitoring provides new visibility into the software pipeline, aiming to forestall further SolarWinds- or Codecov-style attacks. Anterovium...
Threat intelligence programs poised for growth – Source: www.csoonline.com
Source: www.csoonline.com – Author: Enterprise organizations will increase spending, investing in areas like threat intelligence distribution, digital risk management, and security technology integration. Flamingo Images /...
BrandPost: Closing coverage gaps: exploring three cloud-centric security approaches – Source: www.csoonline.com
Source: www.csoonline.com – Author: About | When you have comprehensive security, the future is yours to build. Learn about the strategies and solutions to secure your...
AI-Generated Steganography – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier New research suggests that AIs can produce perfectly secure steganographic images: Abstract: Steganography is the practice of encoding secret information...
Intellihartx data breach exposed the personal and health info of 490,000 individuals – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Intellihartx is notifying about 490,000 individuals that their personal information was compromised in the GoAnywhere zero-day attack in January. The...
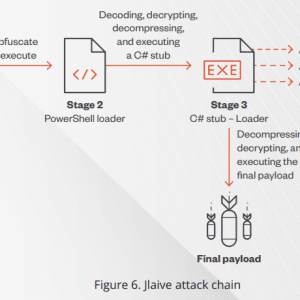
FUD Malware obfuscation engine BatCloak continues to evolve – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers detailed a fully undetectable (FUD) malware obfuscation engine named BatCloak that is used by threat actors. Researchers from Trend Micro have...
Fortinet urges to patch a critical RCE flaw in Fortigate firewalls – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Fortinet released security updates to fix a critical security flaw in its FortiGate firewalls that lead to remote code execution....
Xplain data breach also impacted the national Swiss railway FSS – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The Play ransomware attack suffered by the IT services provider Xplain also impacted the national railway company of Switzerland (FSS)...
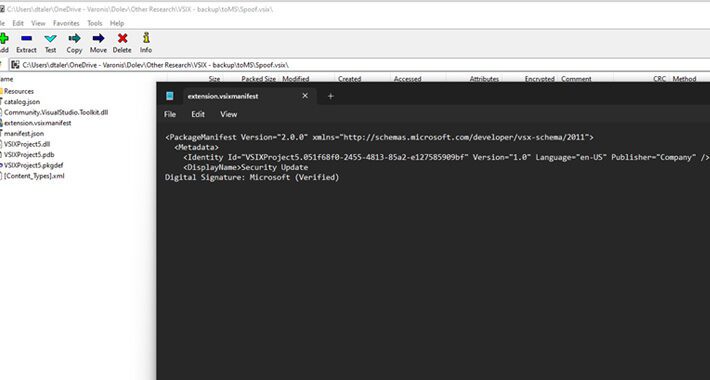
Researchers Uncover Publisher Spoofing Bug in Microsoft Visual Studio Installer – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 12, 2023Ravie LakshmananVulnerability / Software Security researchers have warned about an “easily exploitable” flaw in the Microsoft Visual Studio installer...
Use of Multifactor Authentication (MFA) Nearly Doubles Since 2020, Okta Secure Sign-in Trends Reports Finds – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 SAN FRANCISCO, June 12, 2023 – Okta, Inc. (NASDAQ: OKTA), the leading independent identity partner, today announced the release of its international Secure Sign-In...
RomCom Threat Actor Targets Ukrainian Politicians, US Healthcare – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer, Dark Reading The threat actor known as RomCom has returned to the scene, targeting Ukrainian politicians and a...
10 Important Security Tasks You Shouldn’t Skip – Source: www.darkreading.com
Source: www.darkreading.com – Author: Joshua Goldfarb, Security and Fraud Architect, F5 Most of us have benefited from the mistakes of others. While this may sound like...
‘Stealth Soldier’ Attacks Target Libyan Government Entities With Surveillance Malware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading A wave of advanced persistent threat (APT) attacks aimed at Libyans has been detected, using malware that...
Supply Chain Attack Defense Demands Mature Threat Hunting – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading The headlines have become a steady occurrence … Kaseya, SolarWinds, 3CX, MOVEit, and there are sure to...
Doing Less With Less: Focusing on Value – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ben Johnson, Co-Founder and CTO, Obsidian Security The first half of this two-part article is here: “Cyber Essentialism & ‘Doing Less With...
US Government Provides Guidance on Software Security Guarantee Requirements – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The US Office of Management and Budget (OMB) has issued new guidance on when and how federal agencies should collect...
US Charges Russians With Hacking Cryptocurrency Exchange – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Two Russian nationals have been charged in the US with hacking the now-defunct cryptocurrency exchange Mt. Gox and conspiring to...