Source: www.databreachtoday.com – Author: 1 Doug Browne Director for SaaS Security (SSE, Duo and Cloud Security), APJC at Cisco Systems Doug Browne has over 24 years’...
Month: June 2023
Gozi Host ‘Virus’ Sentenced to 3 Years in US Prison – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Mihai Ionut Paunescu Provided ‘Bulletproof Hosting’ for Trojans Rashmi Ramesh (rashmiramesh_) • June 13, 2023 A Romanian national who...
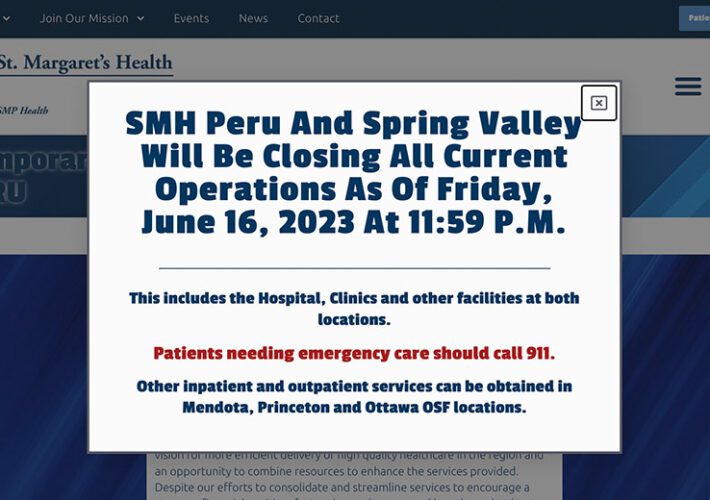
Rural Healthcare Provider Closing Due in Part to Attack Woes – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Healthcare , Industry Specific St. Margaret’s Health Is Permanently Shutting Hospitals and Clinics Marianne Kolbasuk McGee...
New Golang-based Skuld Malware Stealing Discord and Browser Data from Windows PCs – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 14, 2023Ravie LakshmananCyber Threat / Malware A new Golang-based information stealer called Skuld has compromised Windows systems across Europe, Southeast...
Where from, Where to — The Evolution of Network Security – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 14, 2023The Hacker NewsThreat Intel / Network Security For the better part of the 90s and early aughts, the sysadmin...
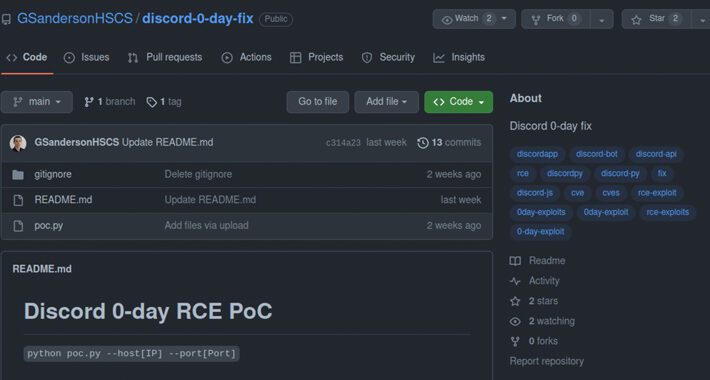
Fake Researcher Profiles Spread Malware through GitHub Repositories as PoC Exploits – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 14, 2023Ravie LakshmananMalware / Zero-Day At least half of dozen GitHub accounts from fake researchers associated with a fraudulent cybersecurity...
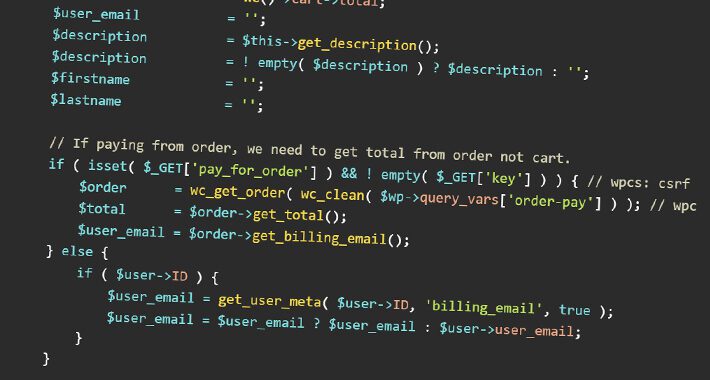
Critical Security Vulnerability Discovered in WooCommerce Stripe Gateway Plugin – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 14, 2023Ravie LakshmananWebsite Security / Hacking A security flaw has been uncovered in the WooCommerce Stripe Gateway WordPress plugin that...
Microsoft Releases Updates to Patch Critical Flaws in Windows and Other Software – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 14, 2023Ravie LakshmananPatch Tuesday / Vulnerability Microsoft has rolled out fixes for its Windows operating system and other software components...
Agencies Are Compelled to Secure All Internet-exposed Equipment by CISA Orders – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac The American Cybersecurity & Infrastructure Security Agency (CISA) issued on June 13, 2023, a binding operational directive (BOD) requiring federal...
British watchdog Ofcom latest victim of MOVEit attack
British television watchdog Ofcom is the latest victim of a supply chain attack against document transfer service MOVEit. The cyber attack against MOVEit saw Russian ransomware...
Cycode Launches CI/CD Pipeline Monitoring Solution (Cimon) to Prevent Supply Chain Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 SAN FRANCISCO, June 12, 2023 – Cycode, the leading application security platform, today announced the launch of Cimon, a seamless solution that enhances the...
Analysis: Social Engineering Drives BEC Losses to $50B Globally – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading Business email compromise (BEC) continues to evolve on the back of sophisticated targeting and social engineering, costing...
Chinese Threat Actor Abused ESXi Zero-Day to Pilfer Files From Guest VMs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading A Chinese cyber-espionage group that researchers previously have spotted targeting VMware ESXi hosts has quietly been...
Popular Apparel, Clothing Brands Being Used in Massive Phishing Scam – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Threat actors have been impersonating more than 100 apparel, clothing, and footwear brands such as Nike, New...
Harness the Power of PKI to Battle Data Breaches – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Identity is the key to unlocking zero-trust environments, but it is also the key to a lucrative payday for cybercriminals selling...
How Security Leaders Should Approach Cybersecurity Startups – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ross Haleliuk , Product Leader and Head of Product, LimaCharlie Security leaders are tired of aggressive sales tactics, and cybersecurity companies must...
Spotify Fined 5 Million Euros for GDPR Violations – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 General Data Protection Regulation (GDPR) , Standards, Regulations & Compliance Online Music Streamer Will Appeal Decision From Swedish Data Protection Authority...
Thales to Buy Tesserent for $119.1M to Aid Australian Growth – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , Managed Security Service Provider (MSSP) , Security Awareness Programs & Computer-Based Training Tesserent’s $125.1M Business Will...
Gozi Host ‘Virus’ Sentenced to 3 Years in US Prison – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Mihai Ionut Paunescu Provided ‘Bulletproof Hosting’ for Trojans Rashmi Ramesh (rashmiramesh_) • June 13, 2023 A Romanian national who...
Rural Healthcare Provider Closing Due in Part to Attack Woes – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Healthcare , Industry Specific St. Margaret’s Health Is Permanently Shutting Hospitals and Clinics Marianne Kolbasuk McGee...
Identifying the Idaho Killer – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier The New York Times has a long article on the investigative techniques used to identify the person who stabbed and...
Top five APAC government hacks of 2023 (so far) – Source: www.cshub.com
Source: www.cshub.com – Author: Jerome Smail Local and national governments in the Asia-Pacific region have been high on the target list for hacking groups in 2023...
Pirated Windows 10 ISOs install clipper malware via EFI partitions – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Hackers are distributing Windows 10 using torrents that hide cryptocurrency hijackers in the EFI (Extensible Firmware Interface) partition to evade...
Microsoft: Windows 10 21H2 has reached end of servicing – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Multiple editions of Windows 10 21H2 have reached their end of service (EOS) in this month’s Patch Tuesday, as Microsoft...
Microsoft fixes Windows 11 issue causing copying, saving failures – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has addressed a known issue causing intermittent failures when saving and copying files on Windows 11 22H2 devices (especially...
Windows 11 KB5027231 cumulative update released with 34 changes – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Microsoft has released the Windows 11 22H2 KB5027231 cumulative update to fix security vulnerabilities and introduce 34 changes, improvements, and bug fixes....
Windows 10 KB5026435 and KB5027215 updates released – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Microsoft has released the Windows 10 KB5027215 and KB5026435 cumulative updates for versions 22H2, version 21H2, version 21H1, and 1809 to...
CISA orders federal agencies to secure Internet-exposed network devices – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan CISA issued this year’s first binding operational directive (BOD) ordering federal civilian agencies to secure misconfigured or Internet-exposed networking equipment...
Microsoft June 2023 Patch Tuesday fixes 78 flaws, 38 RCE bugs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Today is Microsoft’s June 2023 Patch Tuesday, with security updates for 78 flaws, including 38 remote code execution vulnerabilities. While...
Chinese hackers used VMware ESXi zero-day to backdoor VMs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan VMware patched today a VMware ESXi zero-day vulnerability exploited by a Chinese-sponsored hacking group to backdoor Windows and Linux virtual...