Source: www.bleepingcomputer.com – Author: Bill Toulas A suspected pro-China hacker group tracked by Mandiant as UNC4841 has been linked to data-theft attacks on Barracuda ESG (Email...
Month: June 2023
Russian hackers use PowerShell USB malware to drop backdoors – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Russian state-sponsored hacking group Gamaredon (aka Armageddon or Shuckworm) continues to target critical organizations in Ukraine’s military and security intelligence...
WannaCry ransomware impersonator targets Russian “Enlisted” FPS players – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A ransomware operation targets Russian players of the Enlisted multiplayer first-person shooter, using a fake website to spread trojanized versions...
CISA Order Highlights Persistent Risk at Network Edge – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The U.S. government agency in charge of improving the nation’s cybersecurity posture is ordering all federal civilian agencies to take new...
Have I Been Pwned Domain Searches: The Big 5 Announcements! – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt There are presently 201k people monitoring domains in Have I Been Pwned (HIBP). That’s massive! That’s 201k people that have...
Understanding Malware-as-a-Service – Source: securelist.com
Source: securelist.com – Author: Kaspersky Security Services, Alexander Zabrovsky Money is the root of all evil, including cybercrime. Thus, it was inevitable that malware creators would...
Microsoft’s June Patch Tuesday Covers Very Exploitable Bugs – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Patch Management SharePoint, Multicasting and Exchange Figure Prominently This Month Prajeet Nair (@prajeetspeaks) • June 14,...
Microsoft Links 2022 WhisperGate Kyiv Attacks to Russia – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Computing Giant Identifies New Russian GRU Threat Actor: Cadet Blizzard David Perera...
CTO vs CISO Panel: Network Access, Data Loss & Attack Surface – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Brad Moldenhauer CISO, Zscaler Brad is an accomplished cybersecurity leader with over 20 years of experience aligning security strategy and delivering...
Bill for Rural Hospital Cyber Skills Passes Senate Committee – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Healthcare , Industry Specific , Training & Security Leadership Cyber Legislation Advances Just as a Rural Hospital in Illinois Closes Marianne...
New Research: 6% of Employees Paste Sensitive Data into GenAI tools as ChatGPT – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 15, 2023The Hacker NewsBrowser Security / Data Security The revolutionary technology of GenAI tools, such as ChatGPT, has brought significant...
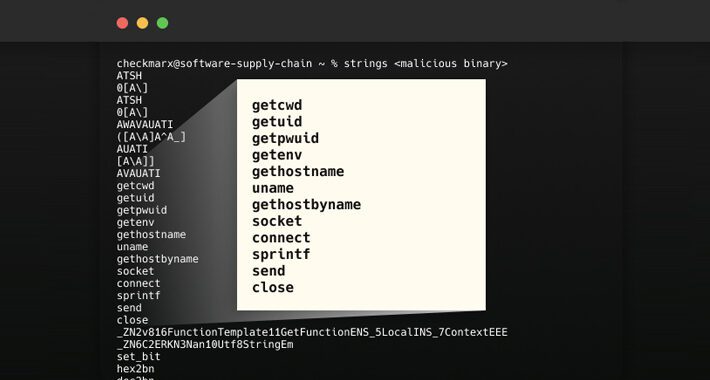
New Supply Chain Attack Exploits Abandoned S3 Buckets to Distribute Malicious Binaries – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 15, 2023Ravie LakshmananSoftware Supply Chain In what’s a new kind of software supply chain attack aimed at open source projects,...
New Report Reveals Shuckworm’s Long-Running Intrusions on Ukrainian Organizations – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 15, 2023Ravie LakshmananCyber War / Threat Intel The Russian threat actor known as Shuckworm has continued its cyber assault spree...
Microsoft Warns of New Russian State-Sponsored Hacker Group with Destructive Intent – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 15, 2023Ravie Lakshmanan Microsoft on Wednesday took the lid off a “novel and distinct Russian threat actor,” which it said...
LockBit Ransomware Extorts $91 Million from U.S. Companies – Source:thehackernews.com
Source: thehackernews.com – Author: . The threat actors behind the LockBit ransomware-as-a-service (RaaS) scheme have extorted $91 million following hundreds of attacks against numerous U.S. organizations...
On the Need for an AI Public Option – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Artificial intelligence will bring great benefits to all of humanity. But do we really want to entrust this revolutionary technology...
Microsoft’s June Patch Tuesday Covers Very Exploitable Bugs – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , Patch Management SharePoint, Multicasting and Exchange Figure Prominently This Month Prajeet Nair (@prajeetspeaks) • June 14,...
Microsoft Links 2022 WhisperGate Kyiv Attacks to Russia – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Computing Giant Identifies New Russian GRU Threat Actor: Cadet Blizzard David Perera...
CTO vs CISO Panel: Network Access, Data Loss & Attack Surface – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Brad Moldenhauer CISO, Zscaler Brad is an accomplished cybersecurity leader with over 20 years of experience aligning security strategy and delivering...
Bill for Rural Hospital Cyber Skills Passes Senate Committee – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Healthcare , Industry Specific , Training & Security Leadership Cyber Legislation Advances Just as a Rural Hospital in Illinois Closes Marianne...
Patch Tuesday June 2023 – 78 Flaws and 38 RCE Bugs Fixed – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu As per usual, Microsoft rolled out its monthly updates on the second Tuesday of the month. 78 flaws, including 38...
Fake Security Researchers Deliver Malicious Zero-Day Exploits – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac Cybercriminals use fake accounts on Twitter and GitHub to spread fake proof-of-concept (PoC) exploits for zero-day vulnerabilities. They impersonate cybersecurity...
DNS Security 101: The Essentials You Need to Know to Keep Your Organization Safe – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Alina Georgiana Petcu The Domain Name System (DNS), which supports the Internet presence of your company, is a centralized network run by...
Cyber insurance: What is it and does my company need it? – Source: www.welivesecurity.com
Source: www.welivesecurity.com – Author: Phil Muncaster While not a ‘get out of jail free card’ for your business, cyber insurance can help insulate it from the...
Network-Security Testing Standard Nears Prime Time – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer, Dark Reading Despite slow progress, NetSecOpen — a group of network-security companies and hardware testing organizations — aims...
Russian APT ‘Cadet Blizzard’ Behind Ukraine Wiper Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading A threat actor that played a key role in the leadup to the Russian invasion of...
Illinois Hospital Closure Showcases Ransomware’s Existential Threat – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading An Illinois hospital’s decision to cease operations later this week at least partly because of a...
XSS Vulnerabilities Found in Microsoft Azure Cloud Services – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Two cloud security vulnerabilities — in Azure Bastion and Azure Container Registry — were found in Microsoft Azure’s...
Why Your SEG Could Be Your Email Security Achilles’ Heel – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Email has always been an attractive target for cybercriminals in search of a money grab. Over the years, we’ve seen email...
Fortinet: Patched Critical Flaw May Have Been Exploited – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading Attackers may have exploited a flaw in Fortinet’s FortiOS SSL-VPN in “a limited number of cases” that...