Source: www.govinfosecurity.com – Author: 1 Delay Comes Amid Criticism of Rule Requiring 4-Day Disclosure of Material Incidents Michael Novinson (MichaelNovinson) • June 20, 2023 ...
Month: June 2023
Strategies for staying ahead of modern cyber warfare – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau By Hadar Sherer, GCO Communications Project Specialist In today’s digital age, nations are no longer solely reliant on traditional military might...
MOVEit customers prompted to patch third vulnerability – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: In May of this year, Progress Software Corporation (formerly Ipswitch) disclosed a vulnerability in MOVEit Transfer and MOVEit Cloud...
News Alert: Budget pressures drive prioritizing of OT cybersecurity projects, says Radiflow – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Tel Aviv, Israel, June 19, 2023– Radiflow, creators of the leading OT network cybersecurity platform CIARA, continue to see budgetary pressure...
News Alert: ThriveDX’s Cyber Academy for Enterprise meets talent shortage, promotes inclusion – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Miami, Fla. – June 20, 2023 – ThriveDX, the leader in cybersecurity and digital skills training, today announced the official launch of...
Researchers Expose New Severe Flaws in Wago and Schneider Electric OT Products – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 20, 2023Ravie LakshmananOperational Technology Three security vulnerabilities have been disclosed in operational technology (OT) products from Wago and Schneider Electric....
Zyxel Releases Urgent Security Updates for Critical Vulnerability in NAS Devices – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 20, 2023Ravie LakshmananVulnerability / Data Security Zyxel has rolled out security updates to address a critical security flaw in its...
Okta moves passkeys to cloud, allowing multi-device authentication – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Okta’s formula for multi-device identity authentication for a hybrid workforce: extract passwords, add ease of passkeys across devices. Amid an...
Microsoft Repeatedly Burned in ‘Layer 7’ DDoS – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Time and again this month, “Russian” hackers bring down Microsoft clouds. Microsoft confirms that a group pretending to be hacktivists...
SMS Toll Fraud Brace for the Bill – Source: securityboulevard.com
Source: securityboulevard.com – Author: Abhimanyu Maheswari SMS Fraud: Brace for the Bill Many businesses today underestimate the security risks associated with their telephone systems, even though...
A “cewl” way for API discovery – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dana Epp Imagine this. You’ve been working on a target for some time now, investing to map out all the API endpoints....
Building an Alert System Using Snowflake – Source: securityboulevard.com
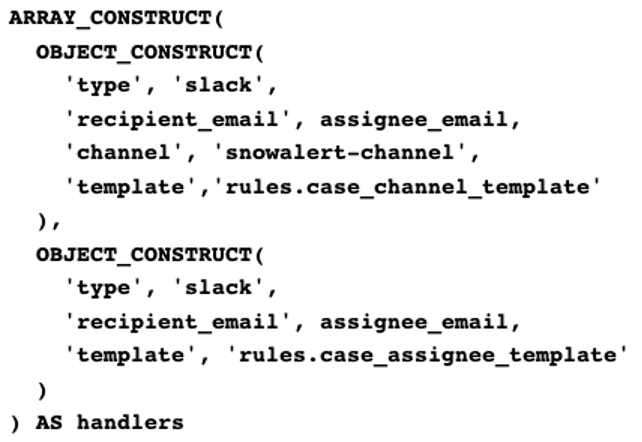
Source: securityboulevard.com – Author: Yiftach Keshet During my time here at Silverfort, I was tasked with building an alert system to send messages from our Snowflake...
BSidesSF 2023 – Michael Bargury – Sure, Let Business Users Build Their Own. What Could Go Wrong? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
The Future of Email Security: Why Technology Alone Isn’t Enough – Source: securityboulevard.com
Source: securityboulevard.com – Author: Cofense Over the past year, the Cofense Intelligence team saw a whopping 569% increase in malicious phishing emails bypassing standard email security...
WCEU 2023: A Melapress recap – Source: securityboulevard.com
Source: securityboulevard.com – Author: Joel Barbara In early June, the team met in Athens, Greece, for WordCamp Europe. As an event sponsor and a fully remote...
The Comprehensive Guide to File Integrity Monitoring – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mark Allers In order to understand Next-Gen File Integrity Monitoring (NGFIM), we must take a quick peek at the history and origin...
How to Securely Introduce Explicit AUTHORITY-CHECKS into Custom RFC-Enabled Function Modules – Source: securityboulevard.com
Source: securityboulevard.com – Author: ltabo How to Securely Introduce Explicit AUTHORITY-CHECKS into Custom RFC-Enabled Function Modules Compliance Aspects Every SAP application provides business-related authorization objects that...
Understanding Identity Access and Management (IAM) Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Grip Security Blog A crucial component of protecting your organization, identity access and management (IAM) security has become a trusted cybersecurity best...
#InfosecurityEurope: Certifications Are No Guarantee of Security – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Over reliance on security certifications can lead to a less diverse and less innovative workforce, and processes designed to satisfy auditors...
Smart Pet Feeders Expose Personal Data – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Two security flaws have been discovered in popular smart pet feeders that could lead to data theft and privacy invasion. According...
#InfosecurityEurope: Digital Dependence Means Government and Industry Must Bolster Collaboration – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Businesses need to and move away from the “impossible” goal of total security, and towards cyber resilience, UK government adviser Saj...
Majority of Users Neglect Best Password Practices: Keeper Security – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The latest Password Management Report by Keeper Security has shed light on the concerning state of password security practices. In particular,...
Over 100,000 ChatGPT Accounts Found in Dark Web Marketplaces – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 More than 100,000 compromised accounts of the OpenAI language model ChatGPT have been found on illicit dark web marketplaces. The discovery...
#InfosecurityEurope: CISOs Must Be Better Marketers and Negotiators – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Enterprise cybersecurity leaders are still underselling themselves to the board and the value they can offer the business, making it harder...
#InfosecurityEurope: How to Weather the Coming Cybersecurity Storm – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Resilience, collaboration and engagement will become vital for organizations hoping to weather a catastrophic cybersecurity “storm” already encircling the world, experts...
#InfosecurityEurope: ThriveDX Launches Cyber Academy for Enterprise to Address Skills Shortages – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 ThriveDX has launched its new Cyber Academy for Enterprise as part of its Human Factor Security suite. The Academy looks to...
#InfosecurityEurope: Michael Johnson Reminds Security Pros Where Success Comes From – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Getting the basics right and understanding yourself are critical foundations to performing consistently well under pressure, Olympic champion Michael Johnson emphasised in...
#InfosecurityEurope: Ironscales Launches GPT-Powered Chat Assistant for Self-Service Threat Reporting – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Following the emergence of large language model-based (LLM) chatbots for the consumer market, organizations increasingly incorporate similar tools for business purposes....
#InfosecurityEurope: Netskope Sets Out to Help Enterprises Safely Use ChatGPT – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity experts are grappling with how to secure use of ChatGPT and other generative AI tools such as Google Bard and...
A bowl full of security problems: Examining the vulnerabilities of smart pet feeders – Source: securelist.com
Source: securelist.com – Author: Roland Sako Introduction In today’s interconnected world, more and more devices are being connected to the internet, including everyday household items like...