Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Industry leaders have warned that some of the AI technology that’s under development may one day pose an existential...
Day: June 30, 2023
FIRESIDE CHAT: Outrageous phone bills stun businesses targeted for ‘SMS toll fraud’ – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido SMS toll fraud is spiking. I learned all about the nuances of deploying – and defending –...
News Alert: NetWitness announces supports for AWS AppFabric, improves SaaS apps security – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido San Francisco, Calif., June 29, 2023 — NetWitness, a globally trusted provider of threat detection, investigation, and response technology and incident response services,...
New Alert: Quantexa, Carahsoft partner to modernize investigative services for federal agencies – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido New York and Reston, Virg., June 27, 2023 — Quantexa, a global leader in Decision Intelligence (DI) solutions for the public and...
News Alert: Jscrambler launches free tool for new PCI DSS anti-skimming requirements – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Porto, Portugal, June 27th 2023– Jscrambler, a leading solution for JavaScript protection and real-time webpage monitoring, today announces the launch and immediate availability...
News Alert: DerSecur rercognized in Forrester’s Static Application Security Testing (SAST) report – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Haifa, Israel, June 26, 2023 — DerSecur, which has developed DerScanner a comprehensive application security platform, has become one of the...
Breach Roundup: Russians Sanctioned for Election Influence – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Cybercrime as-a-service , Cyberwarfare / Nation-State Attacks Also, CISA orders Federal Agencies to Patch Vulnerabilities before 13 July...
New Ransomware Actor 8Base Rivals LockBit in Extortion – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development Group Listed Nearly 40 Victims on its Dark Web...
Live EMEA Webinar | Where Did the Hackers Go? They Ran(somware): Insights into Ransomware Recovery – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Kev Johnson Technical Marketing Architect, Rubrik Kev is a Technical Marketing Architect at Rubrik, where he builds content like technical white...
Trauma, Terrorist Victim Data Breached in University Attack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Governance & Risk Management NHS Patient Data, Student, Alumni Records Compromised at University of...
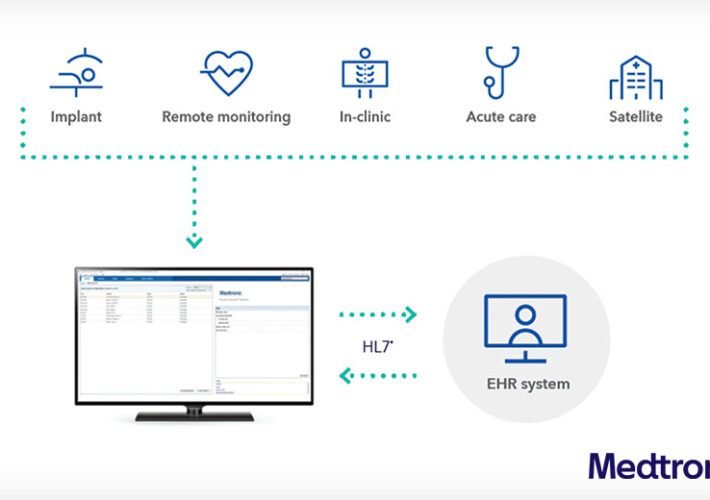
Feds, Medtronic Warn of Flaw in Cardiac Device Data Tool – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Internet of Things Security , Standards, Regulations & Compliance Denial of Service Attack, Remote Code Execution Could Affect...
3 Reasons SaaS Security is the Imperative First Step to Ensuring Secure AI Usage – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 30, 2023The Hacker NewsSaaS Security / Artificial Intelligence, In today’s fast-paced digital landscape, the widespread adoption of AI (Artificial Intelligence)...
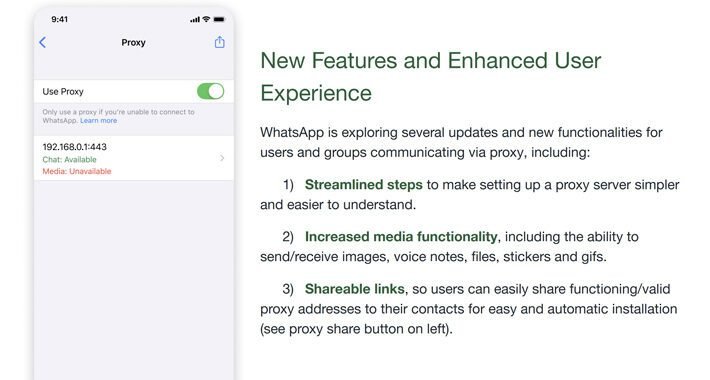
WhatsApp Upgrades Proxy Feature Against Internet Shutdowns – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 30, 2023Ravie LakshmananPrivacy / Tech Meta’s WhatsApp has rolled out updates to its proxy feature, allowing more flexibility in the...
Cybercriminals Hijacking Vulnerable SSH Servers in New Proxyjacking Campaign – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 30, 2023Ravie LakshmananServer Security / Cyber Threat An active financially motivated campaign is targeting vulnerable SSH servers to covertly ensnare...
MITRE Unveils Top 25 Most Dangerous Software Weaknesses of 2023: Are You at Risk? – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 30, 2023Ravie LakshmananVulnerability / Software Security MITRE has released its annual list of the Top 25 “most dangerous software weaknesses”...
LockBit Claims TSMC Hack, Demands $70m Ransom – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 National Hazard Agency, a sub-group of the LockBit ransomware gang, posted the name of Taiwan Semiconductor Manufacturing Company (TSMC), the world’s...
MITRE Announces Most Dangerous Software Weaknesses – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The US government has published a list of the most “common and impactful” software weaknesses of the past two years. The...
GCHQ Reveals Details of State-Backed Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Britain’s signals intelligence agency suffered a cyber-espionage breach at the hands of a state actor two decades ago, the National Cyber...
Amazon Issues Lawsuits Targeting Fake Review Brokers – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Amazon has filed a flurry of lawsuits aimed at tackling the persistent problem of fraudulent customer reviews on its platform. The...
Employee monitoring: is ‘bossware’ right for your company? – Source: www.welivesecurity.com
Source: www.welivesecurity.com – Author: Phil Muncaster While employee monitoring software may boost productivity, it may also be a potential privacy minefield and it can affect your...
NSA and CISA Release Guidelines to Secure CI/CD Environments – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The US National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) have published a comprehensive set of guidelines...
MIT Publishes Framework to Evaluate Cybersecurity Methods – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Researchers from the Massachusetts Institute of Technology (MIT) have published a new framework called Metior, designed to evaluate the effectiveness of...
Charming Kitten’s PowerStar Malware Evolves with Advanced Techniques – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Charming Kitten, a threat actor believed to operate from Iran, has been found to be evolving its PowerStar backdoor malware alongside...
LockBit Dominates Ransomware World, New Report Finds – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The LockBit ransomware gang was found to be the most active in terms of total number of victims from January to...
VPN and RDP Exploitation the Most Common Attack Technique – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Exploitation of remote services like VPNs and RDP was the most commonly seen attack technique last year, according to a new...
Cyware Snags $30M for Threat Intel Infrastructure Tech – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Threat intelligence infrastructure startup Cyware on Thursday announced it had secured $30 million in new financing alongside plans to take...
Rapid7: Japan Threat Landscape Takes on Global Significance – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Japan is the world’s third largest economy. It attracts both criminal and nation-state cyberattacks. The effects of these attacks can...
IP Fabric Raises $25 Million in Series B Funding – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Network assurance company IP Fabric on Thursday announced that it had secured $25 million in a Series B funding round...
Details Disclosed for Critical SAP Vulnerabilities, Including Wormable Exploit Chain – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A cybersecurity firm has disclosed the details of critical SAP vulnerabilities, including a wormable exploit chain, that can expose organizations...
Serious Vulnerability Exposes Admin Interface of Arcserve UDP Backup Solution – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Proof-of-concept (PoC) code targeting a high-severity authentication bypass vulnerability in the Arcserve Unified Data Protection (UDP) backup software was published...