Source: www.securityweek.com – Author: Kevin Townsend Ask any three people to define cyberwar and you will get three different answers. But as global geopolitics worsen and...
Day: June 29, 2023
Invary Raises $1.85 Million in Pre-Seed Funding for Runtime Integrity Solution – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Operating system runtime validation and security firm Invary today announced it has raised $1.85 million in a pre-seed funding round...
Astrix Raises $25 Million to Help Enterprises Secure App-to-App Connections – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Astrix Security, an Israel-based company that specializes in securing app-to-app connections, announced on Wednesday that is has raised $25 million...
Submarine Cables at Risk of Nation-State Sabotage, Spying: Report – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Submarine cables, the backbone of the global economy and telecommunications, are operating in an increasingly risky environment and are prone...
Reminder: CFP for ICS Cybersecurity Conference Closes June 30th – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News The official Call for Presentations (CFP) for SecurityWeek’s 2023 Industrial Control Systems (ICS) Cybersecurity Conference, being held October 23-26, 2023...
Sensitive Information Stolen in LetMeSpy Stalkerware Hack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Radeal, the Polish developer of Android stalkerware ‘LetMeSpy’, is informing users that their personal information and collected data was stolen...
Siemens Energy, Schneider Electric Targeted by Ransomware Group in MOVEit Attack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Energy giants Schneider Electric and Siemens Energy have confirmed being targeted by a ransomware group in the recent campaign exploiting...
Anatsa Banking Trojan Delivered via Google Play Targets Android Users in US, Europe – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Android users in at least five countries have been targeted with the Anatsa banking trojan via malicious droppers uploaded to...
Microsoft Sysmon now detects when executables files are created – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Microsoft has released Sysmon 15, converting it into a protected process and adding the new ‘FileExecutableDetected’ option to log when...
Exploit released for new Arcserve UDP auth bypass vulnerability – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Data protection vendor Arcserve has addressed a high-severity security flaw in its Unified Data Protection (UDP) backup software that can...
Linux version of Akira ransomware targets VMware ESXi servers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Akira ransomware operation uses a Linux encryptor to encrypt VMware ESXi virtual machines in double-extortion attacks against companies worldwide....
Microsoft fixes Windows bug causing File Explorer freezes – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has addressed a known issue causing File Explorer on Windows 11 and Windows Server systems after viewing a file’s...
Brave Browser boosts privacy with new local resources restrictions – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Brave team has announced that the privacy-centric browser will soon introduce new restriction controls allowing users to specify how...
NPM ecosystem at risk from “Manifest Confusion” attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The NPM (Node Package Manager) registry suffers from a security lapse called “manifest confusion,” which undermines the trustworthiness of packages...
The Current State of Business Email Compromise Attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Specops Software Business Email Compromise (BEC) poses a growing threat to businesses of all sizes. As BEC attacks have almost...
Microsoft Teams outage blocks access to web and desktop clients – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft is investigating an ongoing outage blocking customers from accessing and using the Microsoft Teams communication platform via web and...
8Base ransomware gang escalates double extortion attacks in June – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A 8Base ransomware gang is targeting organizations worldwide in double-extortion attacks, with a steady stream of new victims since the...
Busted ‘secure’ EncroChat messaging service leads to over 6,500 arrests by police – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Back in 2020, law enforcement agents across Europe had a major breakthrough in their fight against organised crime. They managed...
Alert: New Electromagnetic Attacks on Drones Could Let Attackers Take Control – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 28, 2023Ravie LakshmananFirmware Security / Tech Drones that don’t have any known security weaknesses could be the target of electromagnetic...
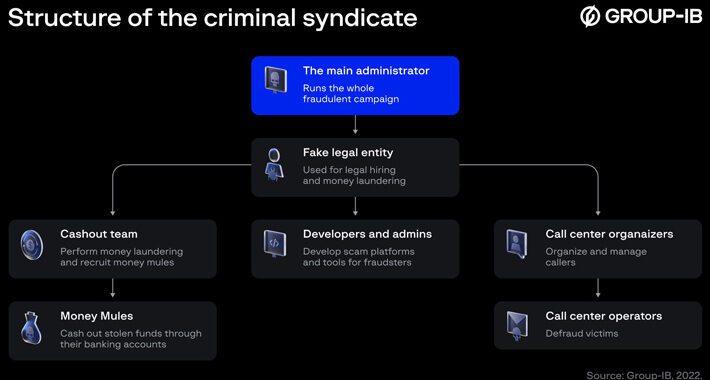
CryptosLabs Scam Ring Targets French-Speaking Investors, Rakes in €480 Million – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 28, 2023Ravie LakshmananCyber Crime / Cryptocurrency Cybersecurity researchers have exposed the workings of a scam ring called CryptosLabs that’s estimated...