Source: www.schneier.com – Author: Bruce Schneier Artificial intelligence will bring great benefits to all of humanity. But do we really want to entrust this revolutionary technology...
Day: June 15, 2023
Microsoft’s June Patch Tuesday Covers Very Exploitable Bugs – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , Patch Management SharePoint, Multicasting and Exchange Figure Prominently This Month Prajeet Nair (@prajeetspeaks) • June 14,...
Microsoft Links 2022 WhisperGate Kyiv Attacks to Russia – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Computing Giant Identifies New Russian GRU Threat Actor: Cadet Blizzard David Perera...
CTO vs CISO Panel: Network Access, Data Loss & Attack Surface – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Brad Moldenhauer CISO, Zscaler Brad is an accomplished cybersecurity leader with over 20 years of experience aligning security strategy and delivering...
Bill for Rural Hospital Cyber Skills Passes Senate Committee – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Healthcare , Industry Specific , Training & Security Leadership Cyber Legislation Advances Just as a Rural Hospital in Illinois Closes Marianne...
Patch Tuesday June 2023 – 78 Flaws and 38 RCE Bugs Fixed – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu As per usual, Microsoft rolled out its monthly updates on the second Tuesday of the month. 78 flaws, including 38...
Fake Security Researchers Deliver Malicious Zero-Day Exploits – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac Cybercriminals use fake accounts on Twitter and GitHub to spread fake proof-of-concept (PoC) exploits for zero-day vulnerabilities. They impersonate cybersecurity...
DNS Security 101: The Essentials You Need to Know to Keep Your Organization Safe – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Alina Georgiana Petcu The Domain Name System (DNS), which supports the Internet presence of your company, is a centralized network run by...
Cyber insurance: What is it and does my company need it? – Source: www.welivesecurity.com
Source: www.welivesecurity.com – Author: Phil Muncaster While not a ‘get out of jail free card’ for your business, cyber insurance can help insulate it from the...
Network-Security Testing Standard Nears Prime Time – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer, Dark Reading Despite slow progress, NetSecOpen — a group of network-security companies and hardware testing organizations — aims...
Russian APT ‘Cadet Blizzard’ Behind Ukraine Wiper Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading A threat actor that played a key role in the leadup to the Russian invasion of...
Illinois Hospital Closure Showcases Ransomware’s Existential Threat – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading An Illinois hospital’s decision to cease operations later this week at least partly because of a...
XSS Vulnerabilities Found in Microsoft Azure Cloud Services – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Two cloud security vulnerabilities — in Azure Bastion and Azure Container Registry — were found in Microsoft Azure’s...
Why Your SEG Could Be Your Email Security Achilles’ Heel – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Email has always been an attractive target for cybercriminals in search of a money grab. Over the years, we’ve seen email...
Fortinet: Patched Critical Flaw May Have Been Exploited – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading Attackers may have exploited a flaw in Fortinet’s FortiOS SSL-VPN in “a limited number of cases” that...
Insights Into Nation-State Tactics: Lessons From Russia’s Hybrid War In Ukraine – Source: www.darkreading.com
Source: www.darkreading.com – Author: Microsoft Security, Microsoft As the war in Ukraine extends into its second year, Russian threat actors have expanded the scope of their...
How Popular Messaging Tools Instill a False Sense of Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tobias Pischl, Head of Product, Information, and Email Security, Symantec Enterprise Division, Broadcom Today, an increasing number of large enterprises, from financial...
Microsoft links Cadet Blizzard APT to Russia’s military intelligence GRU – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Microsoft linked a series of wiping attacks to a Russia-linked APT group, tracked as Cadet Blizzard, that is under the control...
Critical flaw found in WooCommerce Stripe Gateway Plugin used by +900K sites – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Hundreds of thousands of online stores are potentially exposed to hacking due to a critical vulnerability in the WooCommerce Stripe...
Unveiling the Balada injector: a malware epidemic in WordPress – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Learn the shocking truth behind the Balada Injector campaign and find out how to protect your organization from this relentless...
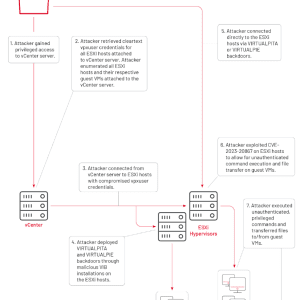
China-linked APT UNC3886 used VMware ESXi Zero-Day – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A China-linked APT group tracked as UNC3886 has been spotted exploiting a VMware ESXi zero-day vulnerability. Mandiant researchers observed a...
LLM meets Malware: Starting the Era of Autonomous Threat – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Malware researchers analyzed the application of Large Language Models (LLM) to malware automation investigating future abuse in autonomous threats. In...
Smashing Security podcast #326: Right Royal security threats and MOVEit mayhem – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley There are shocking revelations about a US Government data suck-up, historic security breaches at Windsor Castle, and the MOVEit hack...
Talking cybersecurity on “Learning Curve” – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Earlier this year I had the honour of being invited by Vodafone to appear on an episode of “Learning Curve”,...
BrandPost: Microsoft special report: Iran’s adoption of cyber-enabled influence operations – Source: www.csoonline.com
Source: www.csoonline.com – Author: About | When you have comprehensive security, the future is yours to build. Learn about the strategies and solutions to secure your...
Attackers set up rogue GitHub repos with malware posing as zero-day exploits – Source: www.csoonline.com
Source: www.csoonline.com – Author: The threat actor created fake personas on Twitter for researchers at a non-existent security firm. In an unusual attack campaign, a hacker...
Microsoft Office 365 AitM phishing reveals signs of much larger BEC campaign – Source: www.csoonline.com
Source: www.csoonline.com – Author: This newly discovered, global campaign indicates growing popularity for multi-stage adversary-in-the-middle tactics among threat actors.
Rezilion releases agentless runtime software vulnerability management solution – Source: www.csoonline.com
Source: www.csoonline.com – Author: Software supply chain security vendor claims to have discovered that true, non-agent-based runtime vulnerability analysis is possible by harnessing cloud APIs. Roman...
Cyber liability insurance vs. data breach insurance: What’s the difference? – Source: www.csoonline.com
Source: www.csoonline.com – Author: Cyber insurance is increasingly becoming a compulsory element in business relationships. Knowing what coverage meets a company’s specific needs can provide better...
Chinese Hackers Exploit VMware Zero-Day to Backdoor Windows and Linux Systems – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 14, 2023Ravie LakshmananZero-Day / Network Security The Chinese state-sponsored group known as UNC3886 has been found to exploit a zero-day...