Source: securityboulevard.com – Author: Dariel Marlow In today’s data-driven world, businesses are faced with the challenge of efficiently integrating and transforming vast amounts of data. With...
Day: June 15, 2023
Passkeys Can Make Passwords a Thing of the Past – Source: securityboulevard.com
Source: securityboulevard.com – Author: Phil Dunkleberger We all seem to have a love/hate relationship with passwords. Over time, we have learned to live with them–even when,...
Content Moderation Tech Startup Trust Lab Snags $15M Investment – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Trust Lab, a Silicon Valley startup founded by Google’s former head of Trust and Safety, has bagged $15 million in...
OT Security Firm Shift5 Adds $33 Million in Funding – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Arlington, VA-based OT security firm Shift5 has raised an additional $33 million in its Series B financing. $50 million was...
XSS Vulnerabilities in Azure Led to Unauthorized Access to User Sessions – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Two cross-site scripting (XSS) vulnerabilities in Azure Bastion and Azure Container Registry (ACR) could have led to unauthorized access to...
Barracuda Zero-Day Attacks Attributed to Chinese Cyberespionage Group – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The recent attacks exploiting a zero-day vulnerability in a Barracuda Networks email security appliance have been attributed by Mandiant to...
SquareX Launches Bug Bounty Program for Browser Security Product – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Hot on the heels of a $6 million seed funding round, cybersecurity startup SquareX today announced a six-week bug bounty...
Fake Security Researcher Accounts Pushing Malware Disguised as Zero-Day Exploits – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Exploit and vulnerability intelligence provider VulnCheck has issued a warning over fake security researcher accounts distributing malware disguised as zero-day...
Four Things to Consider as You Mature Your Threat Intel Program – Source: www.securityweek.com
Source: www.securityweek.com – Author: Marc Solomon When ESG recently asked security professionals to identify the attributes of a mature threat intelligence program, the top response was...
US Organizations Paid $91 Million to LockBit Ransomware Gang – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The LockBit ransomware gang has launched roughly 1,700 attacks in the United States and received approximately $91 million in ransom...
How Europe is Leading the World in the Push to Regulate AI – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press Lawmakers in Europe signed off Wednesday on the world’s first set of comprehensive rules for artificial intelligence, clearing a key...
Microsoft Outs New Russian APT Linked to Wiper Attacks in Ukraine – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Security researchers at Microsoft are publicly outing a new APT group linked to Russia’s General Staff Main Intelligence Directorate (GRU),...
Android GravityRAT malware now steals your WhatsApp backups – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A new Android malware campaign spreading the latest version of GravityRAT has been underway since August 2022, infecting mobile devices...
Clop ransomware gang starts extorting MOVEit data-theft victims – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams The Clop ransomware gang has started extorting companies impacted by the MOVEit data theft attacks, first listing the company’s names on...
Traditional Pen Testing vs. PTaaS with Web Application Security – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Outpost24 While traditional penetration testing (pen testing) has long been the go-to method for identifying security gaps in a organization’s network...
Barracuda ESG zero-day attacks linked to suspected Chinese hackers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A suspected pro-China hacker group tracked by Mandiant as UNC4841 has been linked to data-theft attacks on Barracuda ESG (Email...
Russian hackers use PowerShell USB malware to drop backdoors – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Russian state-sponsored hacking group Gamaredon (aka Armageddon or Shuckworm) continues to target critical organizations in Ukraine’s military and security intelligence...
WannaCry ransomware impersonator targets Russian “Enlisted” FPS players – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A ransomware operation targets Russian players of the Enlisted multiplayer first-person shooter, using a fake website to spread trojanized versions...
CISA Order Highlights Persistent Risk at Network Edge – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The U.S. government agency in charge of improving the nation’s cybersecurity posture is ordering all federal civilian agencies to take new...
Have I Been Pwned Domain Searches: The Big 5 Announcements! – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt There are presently 201k people monitoring domains in Have I Been Pwned (HIBP). That’s massive! That’s 201k people that have...
Understanding Malware-as-a-Service – Source: securelist.com
Source: securelist.com – Author: Kaspersky Security Services, Alexander Zabrovsky Money is the root of all evil, including cybercrime. Thus, it was inevitable that malware creators would...
Microsoft’s June Patch Tuesday Covers Very Exploitable Bugs – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Patch Management SharePoint, Multicasting and Exchange Figure Prominently This Month Prajeet Nair (@prajeetspeaks) • June 14,...
Microsoft Links 2022 WhisperGate Kyiv Attacks to Russia – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Computing Giant Identifies New Russian GRU Threat Actor: Cadet Blizzard David Perera...
CTO vs CISO Panel: Network Access, Data Loss & Attack Surface – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Brad Moldenhauer CISO, Zscaler Brad is an accomplished cybersecurity leader with over 20 years of experience aligning security strategy and delivering...
Bill for Rural Hospital Cyber Skills Passes Senate Committee – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Healthcare , Industry Specific , Training & Security Leadership Cyber Legislation Advances Just as a Rural Hospital in Illinois Closes Marianne...
New Research: 6% of Employees Paste Sensitive Data into GenAI tools as ChatGPT – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 15, 2023The Hacker NewsBrowser Security / Data Security The revolutionary technology of GenAI tools, such as ChatGPT, has brought significant...
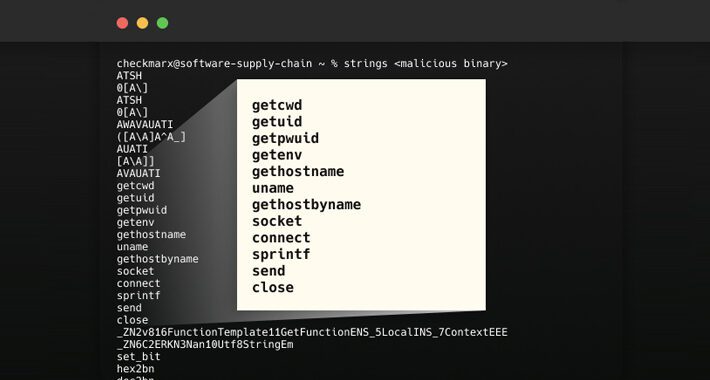
New Supply Chain Attack Exploits Abandoned S3 Buckets to Distribute Malicious Binaries – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 15, 2023Ravie LakshmananSoftware Supply Chain In what’s a new kind of software supply chain attack aimed at open source projects,...
New Report Reveals Shuckworm’s Long-Running Intrusions on Ukrainian Organizations – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 15, 2023Ravie LakshmananCyber War / Threat Intel The Russian threat actor known as Shuckworm has continued its cyber assault spree...
Microsoft Warns of New Russian State-Sponsored Hacker Group with Destructive Intent – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 15, 2023Ravie Lakshmanan Microsoft on Wednesday took the lid off a “novel and distinct Russian threat actor,” which it said...
LockBit Ransomware Extorts $91 Million from U.S. Companies – Source:thehackernews.com
Source: thehackernews.com – Author: . The threat actors behind the LockBit ransomware-as-a-service (RaaS) scheme have extorted $91 million following hundreds of attacks against numerous U.S. organizations...