Source: www.securityweek.com – Author: Ionut Arghire Japanese pharmaceutical giant Eisai this week announced that it has fallen victim to a ransomware attack that forced it to...
Day: June 8, 2023
Vulnerabilities in Honda eCommerce Platform Exposed Customer, Dealer Data – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A researcher has disclosed the details of serious vulnerabilities discovered in a Honda ecommerce platform used for equipment sales. Exploitation...
North Korean Hackers Blamed for $35 Million Atomic Wallet Crypto Theft – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Blockchain analytics firm Elliptic believes that the North Korean advanced persistent threat (APT) actor known as Lazarus Group is responsible...
Cisco Patches Critical Vulnerability in Enterprise Collaboration Solutions – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Cisco on Wednesday announced patches for a critical vulnerability in its Expressway series and TelePresence Video Communication Server (VCS) enterprise...
Barracuda Urges Customers to Replace Hacked Email Security Appliances – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Barracuda Networks is telling customers to immediately replace hacked Email Security Gateway (ESG) appliances, even if they have installed all...
BBC, British Airways, Novia Scotia Among First Big-Name Victims in Global Supply-Chain Hack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press U.S. and British cybersecurity officials warned Wednesday that a Russian cyber-extortion gang’s hack of a file-transfer program popular with corporations...
Experts detail a new Kimsuky social engineering campaign – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini North Korea-linked APT Kimsuky has been linked to a social engineering campaign aimed at experts in North Korean affairs. SentinelLabs researchers uncovered...
German recruiter Pflegia leaks sensitive job seeker info – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Pflegia, a German healthcare recruitment platform, has exposed hundreds of thousands of files with sensitive user data such as names,...
Cisco fixes privilege escalation bug in Cisco Secure Client – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Cisco addressed a high-severity flaw in Cisco Secure Client that can allow attackers to escalate privileges to the SYSTEM account....
Barracuda ESG appliances impacted by CVE-2023-2868 must be immediately replaced – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Barracuda warns customers to immediately replace Email Security Gateway (ESG) appliances impacted by the flaw CVE-2023-2868. At the end of...
VMware fixes a command injection flaw CVE-2023-20887 in VMware Aria Operations for Networks – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Virtualization giant VMware addressed critical and high-severity vulnerabilities in VMware Aria Operations for Networks. Virtualization technology giant VMware released security...
BSidesSF 2023 – Justin Wynn – Red Team Tales – 7 Years of Physical Penetration Testing – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
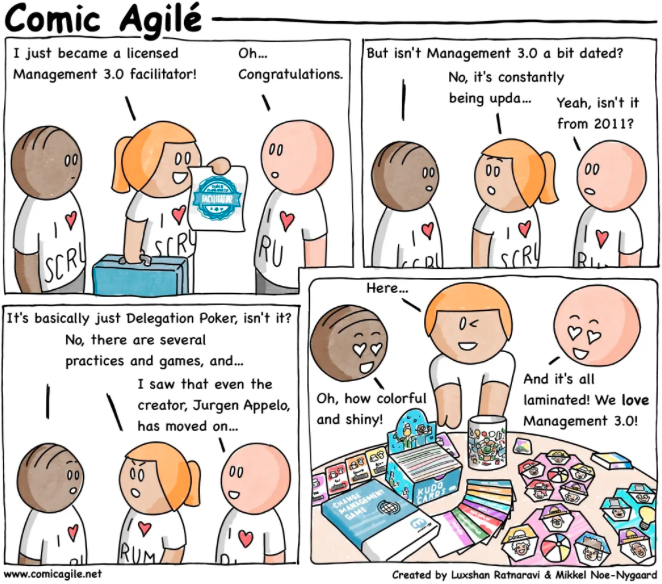
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnarav – #245 — Management 3.0 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Hot Topics Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnarav – #245 — Management 3.0 RTO vs. RPO: Understanding Their Differences...
RTO vs. RPO: Understanding Their Differences and Importance – Source: securityboulevard.com
Source: securityboulevard.com – Author: Spanning Cloud Apps Disasters, such as cyberthreats, data loss and downtime, are inevitable in business. How your organization handles them can be...
Fraud Prevention Strategies – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jenn Jeffers Fraud is a major concern for businesses of all sizes and industries. With the increasing reliance on technology, it has...
Pics AND it Didn’t Happen: Sex Deepfake FBI Alert – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Sextortionists stealing your innocent pictures to make AI nudes. The Federal Bureau of Investigation is warning of an uptick in...
Detection Engineering vs Threat Hunting: Distinguishing the Differences – Source: securityboulevard.com
Source: securityboulevard.com – Author: Cyborg Security In the expansive realm of cybersecurity, the nuanced yet intertwined practices of Detection Engineering and Threat Hunting are two pivotal...
BSidesSF 2023 – Alex Chantavy – Container Vuln Management With (Hopefully) Minimal Burnout – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Ways to Ensure a Secure Data Supply Chain | Eureka Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Eureka Security Today’s cloud-based environments are complex and consist of various components and moving parts that form your organizational ecosystems. These ecosystems...
A Data Security Platform Leader: What KuppingerCole has to Say About comforte – Source: securityboulevard.com
Source: securityboulevard.com – Author: Thomas Stoesser Tech innovation moves pretty fast. But as the landscape continues to evolve and expand, it becomes increasingly difficult for IT...
Cybercrime Predictions from an Industry Veteran: Dr. Chase Cunningham – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lauren Yacono Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Hear no evil: Ultrasound attacks on voice assistants – Source: www.welivesecurity.com
Source: www.welivesecurity.com – Author: Márk Szabó How your voice assistant could do the bidding of a hacker – without you ever hearing a thing Regular WeLiveSecurity...
US DOJ Indicts 6 for $6M Business Email Compromise Scam – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Business Email Compromise (BEC) , Fraud Management & Cybercrime Alleged Conspirators Each Face Up to 40 Years in Prison Rashmi Ramesh...
Cybersecurity Challenges and Opportunities With AI Chatbots – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development ‘Preparedness Pays,’ European AI and Cybersecurity Experts Say at ENISA...
A CISO’s View: How to Handle an Insider Threat – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Insider Threat , Leadership & Executive Communication Security Director Ian Keller on Enabling Responsible Disclosure Within...
Hacking Group Seen Mixing Cybercrime and Cyberespionage – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Suspected Belarusian Hacking Group Has Targeted Ukraine; Crime Crossover ‘Unusual’ Mathew J. Schwartz (euroinfosec) • June 8, 2023 Researchers...
Dragos Lays Off 9% of Workers as OT Security Spending Slows – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Operational Technology (OT) , Vulnerability Assessment & Penetration Testing (VA/PT) 50 Staffers Axed as Dragos Sees...
Suspected Nation-State Actors Target US Aerospace Industry – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Endpoint Security , Fraud Management & Cybercrime PowerDrop Malware Is Simple But Sophisticated Prajeet Nair (@prajeetspeaks)...
Google Cloud launches Cryptomining Protection Program – Source: www.csoonline.com
Source: www.csoonline.com – Author: Google Cloud Cryptomining Protection Program is part of the Security Command Center Premium service to help users detect cryptomining attacks. By Samira...
BrandPost: The 4 inexcusable failures of legacy backup tools – Source: www.csoonline.com
Source: www.csoonline.com – Author: About | Achieve data resilience, de-risk your AWS migration, and unify data protection with a modern backup tool. If you’re relying on...