Source: www.securityweek.com – Author: Joshua Goldfarb A few months ago, I found myself perusing a more than ample hotel breakfast buffet in search of a tasty...
Day: June 7, 2023
VMware Plugs Critical Flaws in Network Monitoring Product – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Virtualization technology giant VMware on Wednesday shipped urgent patches to cover security defects in the Aria Operations for Networks product,...
BA, Boots and BBC cyber-attack: who is behind it and what happens next? – Source: www.theguardian.com
Source: www.theguardian.com – Author: Dan Milmo and Alex Hern British Airways, Boots and the BBC have been hit with an ultimatum to begin ransom negotiations from...
Hackers Issue ‘Ultimatum’ Over Payroll Data Breach – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP A cybercrime gang reportedly based in Russia has issued “an ultimatum” to British and other companies targeted in a recentlarge-scale hack...
US, Israel Provide Guidance on Securing Remote Access Software – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire US and Israeli government agencies have published a new guide to help organizations secure remote access software against malicious attacks....
OWASP’s 2023 API Security Top 10 Refines View of API Risks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend OWASP’s ranking for the major API security risks in 2023 has been published. The list includes many parallels with the...
Android’s June 2023 Security Update Patches Exploited Arm GPU Vulnerability – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Security updates announced this week by Google for the Android operating system resolve over 50 vulnerabilities, including an Arm Mali...
ChatGPT Hallucinations Can Be Exploited to Distribute Malicious Code Packages – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs It’s possible for threat actors to manipulate artificial intelligence chatbots such as ChatGPT to help them distribute malicious code packages...
Blumira Raises $15 Million for SMB-Tailored XDR Platform – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Cybersecurity startup Blumira today announced the launch of its extended detection and response (XDR) platform for small and medium-sized businesses...
Microsoft Will Pay $20M to Settle US Charges of Illegally Collecting Children’s Data – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press Microsoft will pay a fine of $20 million to settle Federal Trade Commission charges that it illegally collected and retained...
Clop ransomware gang claims the hack of hundreds of victims exploiting MOVEit Transfer bug – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Clop ransomware group claims to have hacked hundreds of companies globally by exploiting MOVEit Transfer vulnerability. The Clop ransomware group...
June 2023 Security Update for Android fixed Arm Mali GPU bug used by spyware – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini June 2023 security update for Android released by Google fixes about fifty flaws, including an Arm Mali GPU bug exploited...
New PowerDrop malware targets U.S. aerospace defense industry – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A previously unknown threat actor has been observed targeting the U.S. aerospace defense sector with a new PowerShell malware dubbed...
+60,000 Android apps spotted hiding adware for past six months – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Bitdefender researchers have discovered 60,000 different Android apps secretly installing adware in the past six months. Bitdefender announced the discovery...
NASA website flaw jeopardizes astrobiology fans – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A flaw in NASA website dedicated to astrobiology could have tricked users into visiting malicious websites by disguising a dangerous...
Hackers stole around $35 million in Atomic Wallet security breach – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Threat actors have stolen more than $35 million from the decentralized cryptocurrency wallet platform Atomic Wallet. Atomic Wallet is a...
Cisco fixes AnyConnect bug giving Windows SYSTEM privileges – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Cisco has fixed a high-severity vulnerability found in Cisco Secure Client (formerly AnyConnect Secure Mobility Client) software that can let...
Lazarus hackers linked to the $35 million Atomic Wallet heist – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The notorious North Korean hacking group known as Lazarus has been linked to the recent Atomic Wallet hack, resulting in...
New Fractureiser malware used CurseForge Minecraft mods to infect Windows, Linux – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Hackers used the popular Minecraft modding platforms Bukkit and CurseForge to distribute a new ‘Fractureiser’ information-stealing malware through uploaded modifications...
VMware fixes critical vulnerability in vRealize network analytics tool – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan VMware issued multiple security patches today to address critical and high-severity vulnerabilities in VMware Aria Operations for Networks, allowing attackers...
CEO guilty of selling counterfeit Cisco devices to military, govt orgs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A Florida man has pleaded guilty to importing and selling counterfeit Cisco networking equipment to various organizations, including education, government...
EC-Council’s Certified CISO Hall of Fame Report 2023 shows Cloud Security as Top Concern – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by EC-Council A survey of global cybersecurity leaders through the 2023 Certified CISO Hall of Fame Report commissioned by EC-Council identified...
Android security update fixes Mali GPU bug exploited as zero-day – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Google has released the monthly security update for the Android platform, adding fixes for 56 vulnerabilities, five of them with...
Vulnerability Alert! Two New Exploited Flaws Discovered on Zyxel Firewalls – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși CISA included CVE-2023-33009 and CVE-2023-33010 Zyxel Firewalls flaws in its Known Exploited Vulnerabilities (KEV) catalog. The new CVEs could lead...
New PowerDrop Malware Discovered Targeting U.S. Aerospace Industry – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși Researchers announced finding a sample of the new PowerDrop malware in the network of a defense contractor in the U.S....
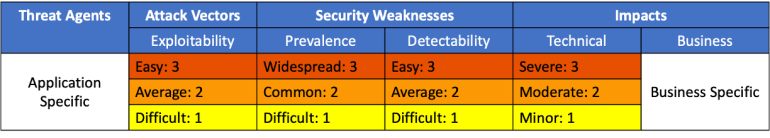
OWASP API Security Top-10 for 2023 Risk Ratings – Source: securityboulevard.com
Source: securityboulevard.com – Author: wlrmblog As you know by now, the final version of the OWASP API Security Top-10 2023 has been released. At first blush,...
Healthcare M&A Means Acquiring Legacy Threats – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mike Spinney Northern Maine Medical Center. Fort Kent, Maine. Fort Kent is a town of just over 4,000 residents abutting the Canadian...
Easy as PyPI Pie – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kell van Daal Recently PyPI suspended new user sign-ups as well as new project registration, citing the volume of malicious users and...
How SIEM Helps With Cyber Insurance – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kelsey Gast To gain proper coverage, organizations have to evaluate their needs, and demonstrate appropriate levels of security monitoring to obtain a...
How to choose a CAASM vendor – Source: securityboulevard.com
Source: securityboulevard.com – Author: Cavelo Blog Business operations increasingly rely on cloud applications and connected systems and so the need for modern security measures has never...