Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading CrowdStrike is jumping on the generative AI bandwagon, as the company tests out its own generative AI...
Day: June 1, 2023
Salesforce ‘Ghost Sites’ Expose Sensitive Corporate Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading Salesforce customers are abandoning their sites without deactivating them, leaving sensitive corporate, vendor, and user data...
8 best practices for securing your Mac from hackers in 2023 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cory Bohon Best practices for securing your Mac against potential hacks and security vulnerabilities include enabling the firewall, using strong passwords and...
BlackCat claims the hack of the Casepoint legal technology platform used by US agencies – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The BlackCat ransomware gang claims to have hacked the Casepoint legal technology platform used US agencies, including SEC and FBI....
Widespread exploitation by botnet operators of Zyxel firewall flaw – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Threat actors are actively exploiting a command injection flaw, tracked as CVE-2023-28771, in Zyxel firewalls to install malware. Threat actors...
Experts warn of backdoor-like behavior within Gigabyte systems – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers discovered a suspected backdoor-like behavior within Gigabyte systems that exposes devices to compromise. Researchers from firmware security firm Eclypsium...
Threat actors are exploiting Barracuda Email Security Gateway bug since October 2022 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Recently disclosed zero-day flaw in Barracusa Email Security Gateway (ESG) appliances had been actively exploited by attackers since October 2022....
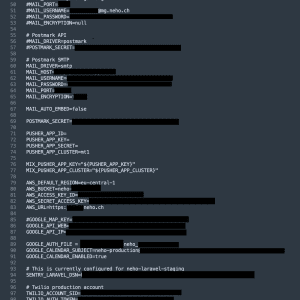
Swiss real estate agency Neho fails to put a password on its systems – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A misconfiguration of Swiss real estate agency Neho’s systems exposed sensitive credentials to the public. Neho, a Switzerland-based real estate...
Malicious PyPI Packages Using Compiled Python Code to Bypass Detection – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 01, 2023Ravie LakshmananProgramming / Supply Chain Researchers have discovered a novel attack on the Python Package Index (PyPI) repository that...
How Wazuh Improves IT Hygiene for Cyber Security Resilience – Source:thehackernews.com
Source: thehackernews.com – Author: . IT hygiene is a security best practice that ensures that digital assets in an organization’s environment are secure and running properly....
Improved BlackCat Ransomware Strikes with Lightning Speed and Stealthy Tactics – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 01, 2023Ravie LakshmananEndpoint Security / Encryption The threat actors behind BlackCat ransomware have come up with an improved variant that...
N. Korean ScarCruft Hackers Exploit LNK Files to Spread RokRAT – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 01, 2023Ravie LakshmananCyber Threat / Malware Cybersecurity researchers have offered a closer look at the RokRAT remote access trojan that’s...
Active Mirai Botnet Variant Exploiting Zyxel Devices for DDoS Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 01, 2023Ravie LakshmananNetwork Security / Exploit The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a recently patched critical...
Urgent WordPress Update Fixes Critical Flaw in Jetpack Plugin on Million of Sites – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 01, 2023Ravie LakshmananWebsite Security / WordPress WordPress has issued an automatic update to address a critical flaw in the Jetpack...
HMRC in New Tax Credits Scam Warning – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The UK’s tax office has warned of a new set of scams designed to trick customers claiming tax credits into handing over...
Amazon to Pay $31m After FTC’s Security and Privacy Allegations – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Amazon will pay close to $31m to the Federal Trade Commission (FTC) to settle allegations relating to Alexa and its Ring...
Zyxel Customers Urged to Patch Exploited Bug – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The security community is urging Zyxel networking device users to update their firewalls and VPNs after reports that hackers are actively...
Exploit released for RCE flaw in popular ReportLab PDF library – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A researcher has published a working exploit for a remote code execution (RCE) flaw impacting ReportLab Toolkit, a popular Python...
Amazon faces $30 million fine over Ring, Alexa privacy violations – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Amazon will pay $30 million in fines to settle allegations of privacy violations related to the operation of its Ring...
Kali Linux 2023.2 released with 13 new tools, pre-built HyperV image – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Kali Linux 2023.2, the second version of 2023, is now available with a pre-built Hyper-V image and thirteen new tools,...
Terminator antivirus killer is a vulnerable Windows driver in disguise – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan A threat actor known as Spyboy is promoting a tool called “Terminator” on a Russian-speaking hacking forum that can allegedly...
Hackers exploit critical Zyxel firewall flaw in ongoing attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Hackers are performing widespread exploitation of a critical-severity command injection flaw in Zyxel networking devices, tracked as CVE-2023-28771, to install...
Stealthy SeroXen RAT malware increasingly used to target gamers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A stealthy remote access trojan (RAT) named ‘SeroXen’ has recently gained popularity as cybercriminals begin using it for its low...
Toyota finds more misconfigured servers leaking customer info – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Toyota Motor Corporation has discovered two additional misconfigured cloud services that leaked car owners’ personal information for over seven years....
7 Stages of Application Testing: How to Automate for Continuous Security – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Outpost24 With cyber-attacks becoming more sophisticated, organizations are becoming increasingly aware of the importance of safeguarding their web applications against...
Dark Pink hackers continue to target govt and military organizations – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Dark Pink APT hacking group continues to be very active in 2023, observed targeting government, military, and education organizations...
BrandPost: Cybercriminals are abusing security tools—here’s how we’re stopping them – Source: www.csoonline.com
Source: www.csoonline.com – Author: About | When you have comprehensive security, the future is yours to build. Learn about the strategies and solutions to secure your...
Gigabyte firmware component can be abused as a backdoor – Source: www.csoonline.com
Source: www.csoonline.com – Author: Attackers can abuse the UEFI firmware to inject executable malware code into the Windows kernel, compromising systems. Researchers warn that the UEFI...
Inactive, unmaintained Salesforce sites vulnerable to threat actors – Source: www.csoonline.com
Source: www.csoonline.com – Author: Research highlights the risks posed by inactive Salesforce sites that continue to pull sensitive business data and can be easily exploited by...
Trellix, Netskope announce new Amazon Security Lake support to enhance threat detection, remediation – Source: www.csoonline.com
Source: www.csoonline.com – Author: Trellix expands XDR support for Amazon Security Lake while Netskope integrates its SSE platform with AWS’ centralized security data service. Cybersecurity vendors...