Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Privacy , Standards, Regulations & Compliance Case Is FTC’s 2nd Enforcement of Health Data Breach Notification...
Month: May 2023
Live Webinar | Safeguarding Australia’s Business Continuity from the Uncertain Threat Landscape – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Data Loss Prevention (DLP) , Endpoint Security , Fraud Management & Cybercrime Presented by Zscaler 60 Ransomware...
LIVE Webinar | It’s Not the Data, It’s the People: Cybercrime’s Human Impact – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Steven Stone Head of Rubrik Zero Labs, Rubrik Steven Stone leads Rubrik’s new data threat research unit to uncover real-world intrusions...
4 State AGs Punch EyeMed With $2.5 M Fine for 2020 Breach – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Legislation & Litigation , Security Operations NJ, Pennsylvania, Oregon, Florida Settlements Follow Earlier Fines by NY Regulators Marianne...
Data443 Buys Cyren Assets Out of Bankruptcy for Up to $3.5M – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Email Security & Protection , Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development Acquisitive Startup Buys Cyren’s Threat Intel,...
Industrial Secure Remote Access Is Essential, but Firms Concerned About Risks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Secure remote access is essential for industrial organizations, but many employees who took part in a recent survey expressed concerns...
Triple Threat: Insecure Economy, Cybercrime Recruitment and Insider Threats – Source: www.securityweek.com
Source: www.securityweek.com – Author: Derek Manky So far in 2023, layoffs have resulted in tens of thousands of tech workers losing their jobs. And that’s just...
Quantum Decryption Brought Closer by Topological Qubits – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Quantinuum has demonstrated the controlled creation and manipulation of non-Abelian anyons – or, put more simply, brought the arrival of...
New SBOM Hub Helps All Stakeholders in Software Distribution Chain – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Lineaje has launched SBOM360 Hub, a platform for software producers, sellers, and consumers to publish, share and use software bills...
Google Announces New Rating System for Android and Device Vulnerability Reports – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Google on Wednesday announced that it’s updating the Android and Google Devices Vulnerability Reward Program (VRP) with a new system...
PoC Tool Exploits Unpatched KeePass Vulnerability to Retrieve Master Passwords – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A researcher has published a proof-of-concept (PoC) tool that exploits an unpatched KeePass vulnerability to retrieve the master password from...
Cisco Says PoC Exploits Available for Newly Patched Enterprise Switch Vulnerabilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Cisco this week announced patches for critical-severity vulnerabilities in multiple small business switches and warned that proof-of-concept (PoC) code that...
Millions of Smartphones Distributed Worldwide With Preinstalled ‘Guerrilla’ Malware – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A threat actor has control over millions of smartphones distributed worldwide thanks to a piece of malware that has been...
State-Sponsored Cybercrime Group`s Infrastructure Revealed – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Marian Researchers have uncovered previously unknown attack infrastructure used by Pakistani and Chinese entities operated by the state-sponsored group SideWinder. In a...
EDR vs. Antivirus: Choose the Best Security Solution for Your Endpoints – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac Nowadays your business and your data need a carefully thought protection suit for at least two reasons. First, cybersecurity threats...
Ransomware in the Name of Charity: MalasLocker Targets Zimbra – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Marian A new ransomware operation has been observed hacking Zimbra servers to steal emails and encrypt files. Instead of demanding a ransom payment,...
Why are we still talking about email security? – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau By Deryck Mitchelson, Field CISO EMEA, Check Point Software Technologies. Email security compromises are among the costliest in cyber. Last year, organizations...
RSAC Fireside Chat: Deploying Hollywood-tested content protection to improve mobile app security – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido Your go-to mobile apps aren’t nearly has hackproof as you might like to believe. Related: Fallout of...
BianLian Skips Encryption on Way to Extortion – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Ransomware BianLian Is Not Double Trouble Anymore, Says US CISA Prajeet Nair (@prajeetspeaks) • May 17,...
FTC Fines Fertility App Vendor, Bars It From Data Sharing – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , Privacy , Standards, Regulations & Compliance Case Is FTC’s 2nd Enforcement of Health Data Breach Notification...
The State of Data Security: The Human Impact of Cybercrime – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Steven Stone Head of Rubrik Zero Labs, Rubrik Steven Stone leads Rubrik’s new data threat research unit to uncover real-world intrusions...
Live Webinar | Safeguarding Australia’s Business Continuity from the Uncertain Threat Landscape – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Data Loss Prevention (DLP) , Endpoint Security , Fraud Management & Cybercrime Presented by Zscaler 60 Ransomware...
4 State AGs Punch EyeMed With $2.5 M Fine for 2020 Breach – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Breach Notification , Legislation & Litigation , Security Operations NJ, Pennsylvania, Oregon, Florida Settlements Follow Earlier Fines by NY Regulators Marianne...
Data443 Buys Cyren Assets Out of Bankruptcy for Up to $3.5M – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Email Security & Protection , Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development Acquisitive Startup Buys Cyren’s Threat Intel,...
Aviatrix is transforming cloud network security with distributed firewalling – Source: www.csoonline.com
Source: www.csoonline.com – Author: The new distributed cloud firewall offering distributes both inspection and policy enforcement into the original path of application traffic, eliminating the need...
Russian national indicted for ransomware attacks against the US – Source: www.csoonline.com
Source: www.csoonline.com – Author: Mikhail Pavlovich Matveev is charged with conspiring to transmit ransom demands, conspiring to damage protected computers, and intentionally damaging protected computers. Metamorworks...
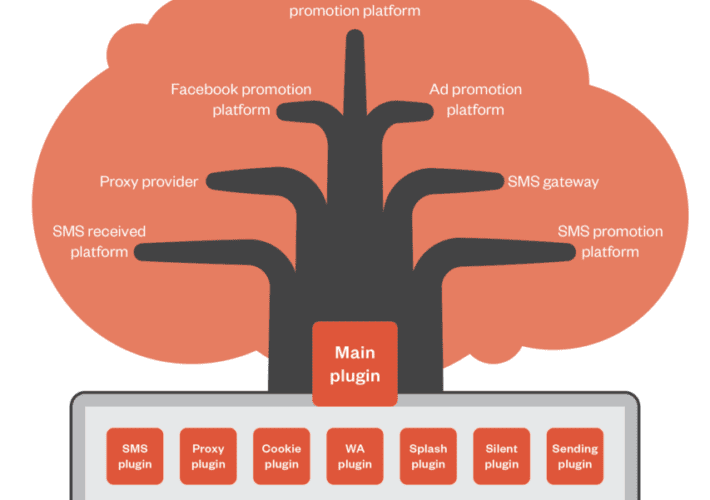
Lemon Group Uses Millions of Pre-Infected Android Phones to Enable Cybercrime Enterprise – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading Millions of Android phone users around the world are contributing daily to the financial wellbeing of...
5 Ways Security Testing Can Aid Incident Response – Source: www.darkreading.com
Source: www.darkreading.com – Author: David Dunn, Senior Managing Director and Head of EMEA Cybersecurity, FTI Consulting The importance for organizations to understand who their adversaries are...
BianLian Cybercrime Group Changes Up Extortion Methods, Warns CISA – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading In an advisory this week, the US Cybersecurity and Infrastructure Security Agency (CISA) alongside the Federal Bureau...
Houthi-Backed Spyware Effort Targets Yemen Aid Workers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading An ongoing spyware campaign is targeting attendees of Saudi government-led negotiations on Yemen, along with humanitarian and...