DISH slapped with multiple lawsuits after ransomware cyber attackDish Network has been slapped with multiple class action lawsuits after it suffered a ransomware incident that was behind...
Month: April 2023
Fake ransomware gang targets U.S. orgs with empty data leak threats
Fake ransomware gang targets U.S. orgs with empty data leak threatsFake extortionists are piggybacking on data breaches and ransomware incidents, threatening U.S. companies with publishing or...
3CX Supply Chain Attack — Here’s What We Know So Far
3CX Supply Chain Attack — Here's What We Know So FarEnterprise communications software maker 3CX on Thursday confirmed that multiple versions of its desktop app for...
Deep Dive Into 6 Key Steps to Accelerate Your Incident Response
Deep Dive Into 6 Key Steps to Accelerate Your Incident ResponseOrganizations rely on Incident response to ensure they are immediately aware of security incidents, allowing for quick action...
Cyber Police of Ukraine Busted Phishing Gang Responsible for $4.33 Million Scam
Cyber Police of Ukraine Busted Phishing Gang Responsible for $4.33 Million ScamThe Cyber Police of Ukraine, in collaboration with law enforcement officials from Czechia, has arrested...
Winter Vivern APT Targets European Government Entities with Zimbra Vulnerability
Winter Vivern APT Targets European Government Entities with Zimbra VulnerabilityThe advanced persistent threat (APT) actor known as Winter Vivern is now targeting officials in Europe and...
Hackers Exploiting WordPress Elementor Pro Vulnerability: Millions of Sites at Risk!
Hackers Exploiting WordPress Elementor Pro Vulnerability: Millions of Sites at Risk!Unknown threat actors are actively exploiting a recently patched security vulnerability in the Elementor Pro website...
Cacti, Realtek, and IBM Aspera Faspex Vulnerabilities Under Active Exploitation
Cacti, Realtek, and IBM Aspera Faspex Vulnerabilities Under Active ExploitationCritical security flaws in Cacti, Realtek, and IBM Aspera Faspex are being exploited by various threat actors...
World Backup Day is here again – 5 tips to keep your precious data safe
World Backup Day is here again – 5 tips to keep your precious data safeThe only backup you will ever regret is the one you didn't...
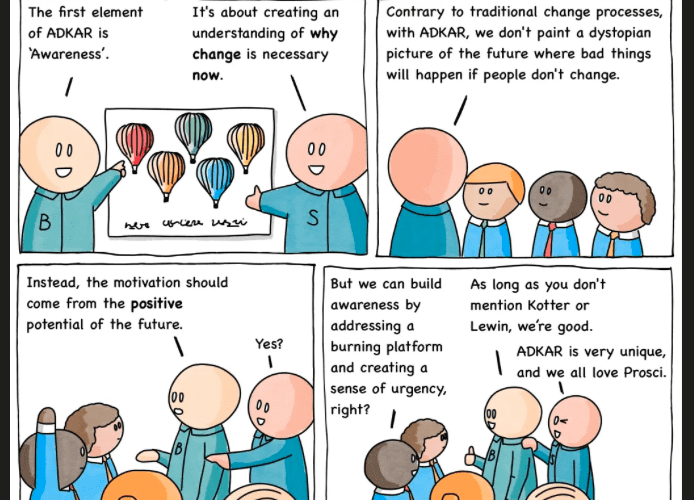
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnarav – #233 — Burning Platform
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnarav – #233 — Burning Platform via the respected Software Engineering expertise of Mikkel Noe-Nygaard as well as the lauded...
Post-Conference Tech Spec: Why Building Your Ship (Application) with Raw Materials is a Bad Idea
Post-Conference Tech Spec: Why Building Your Ship (Application) with Raw Materials is a Bad Idea The post Post-Conference Tech Spec: Why Building Your Ship (Application)...
Challenges of Securing the Modern Workforce
Challenges of Securing the Modern WorkforceAs the world continues to evolve and adopt new technologies, the modern workforce has changed significantly, and so have the opportunities...
German Police Raid DDoS-Friendly Host ‘FlyHosting’
German Police Raid DDoS-Friendly Host ‘FlyHosting’Authorities in Germany this week seized Internet servers that powered FlyHosting, a dark web service that catered to cybercriminals operating DDoS-for-hire...
Noname Security Extends Reach of API Security Platform
Noname Security Extends Reach of API Security Platform Noname Security this week extended the reach of its platform for securing application programming interfaces (APIs) to make...
USENIX Security ’22 – Andreas Kogler, Jonas Juffinger, Salman Qazi, Yoongu Kim, Moritz Lipp, Nicolas Boichat, Eric Shiu, Mattias Nissler, Daniel Gruss – ‘Half-Double: Hammering From The Next Row Over’
USENIX Security ’22 – Andreas Kogler, Jonas Juffinger, Salman Qazi, Yoongu Kim, Moritz Lipp, Nicolas Boichat, Eric Shiu, Mattias Nissler, Daniel Gruss – ‘Half-Double: Hammering From...
3 Ways Balbix can help operationalize CISA BOD 23-01
3 Ways Balbix can help operationalize CISA BOD 23-01What is CISA Directive BOD 23-01? In October 2022, the US Cybersecurity and Infrastructure Security Agency (CISA), which...
Women’s History Month at RiskLens: More Voices – Aliscia Warren
Women’s History Month at RiskLens: More Voices – Aliscia Warren For Women’s History Month, we are asking RiskLens staff members for their thoughts on the current...
The Future of XDR in Security Operations
The Future of XDR in Security OperationsIn this blog we talk about the future of XDR in Security Operations. What does... The post The Future of...
FusionAuth announces Pass-wordle™
FusionAuth announces Pass-wordle™FusionAuth is proud to announce the next big thing in end user authentication. Passwords suck Standards body, such as NIST, no longer recommend using...
Hackers are actively exploiting a flaw in the Elementor Pro WordPress plugin
Hackers are actively exploiting a flaw in the Elementor Pro WordPress pluginThreat actors are actively exploiting a high-severity flaw in the Elementor Pro WordPress plugin used...
Treading Water: The Struggle Against Third-Party Vulnerabilities and How True Automation Can Help.
Treading Water: The Struggle Against Third-Party Vulnerabilities and How True Automation Can Help.By Dan Richings – Senior Vice President, Global Presales, Solutions Engineering, and Support –...
Friday Squid Blogging: Giant Squid vs. Blue Marlin
Friday Squid Blogging: Giant Squid vs. Blue MarlinEpic matchup. As usual, you can also use this squid post to talk about the security stories in the...
German Police Raid DDoS-Friendly Host ‘FlyHosting’
German Police Raid DDoS-Friendly Host ‘FlyHosting’Authorities in Germany this week seized Internet servers that powered FlyHosting, a dark web offering that catered to cybercriminals operating DDoS-for-hire...
From Workshops to Leader Panels: A Recap of Women’s History Month at McAfee
From Workshops to Leader Panels: A Recap of Women’s History Month at McAfee From Workshops to Leader Panels: A Recap of Women’s History Month at McAfee...
Preventing and Detecting Attacks Involving 3CX Desktop App
Preventing and Detecting Attacks Involving 3CX Desktop AppIn this blog entry, we provide technical details and analysis on the 3CX attacks as they happen. We also...
S4x23 Review Part 4: Cybersecurity for Industrial IoT
S4x23 Review Part 4: Cybersecurity for Industrial IoTIn this fourth article, I introduce the discussion related to Industrial IoT, that is involved challenges to adopt cybersecurity...
Study: Women in cybersecurity feel excluded, disrespected
Study: Women in cybersecurity feel excluded, disrespectedFeelings of exclusion and being disrespected impacts hiring opportunities and retention for women, according to a new report. The post...
15 million public-facing services vulnerable to CISA KEV flaws
15 million public-facing services vulnerable to CISA KEV flawsOver 15 million publicly facing services are susceptible to at least one of the 896 vulnerabilities listed in...
Twitter open-sources recommendation algorithm code
Twitter open-sources recommendation algorithm codeTwitter announced on Friday that it's open-sourcing the code behind the recommendation algorithm the platform uses to select the contents of the...
Artificial intelligence: A double-edged sword for technology & ethics
Artificial intelligence: A double-edged sword for technology & ethicsPål (Paul) has more than 30 years of experience from the IT industry and has worked with both...