Twitter’s ditching of free text-message authentication doesn’t mean that you should forgo using 2FA. Instead, switch to another – and, indeed, better – 2FA option. Starting...
Month: April 2023
Banking turmoil opens opportunities for fraud – Week in security with Tony Anscombe
Scammers are looking to cash in on the chaos that has set in following the startling meltdowns of Silicon Valley Bank and Signature Bank and the...
SVB’s collapse is a scammer’s dream: Don’t get caught out
How cybercriminals can exploit Silicon Valley Bank’s downfall for their own ends – and at your expense Big news events and major crises usually trigger an...
Not‑so‑private messaging: Trojanized WhatsApp and Telegram apps go after cryptocurrency wallets
ESET researchers analyzed Android and Windows clippers that can tamper with instant messages and use OCR to steal cryptocurrency funds ESET researchers have discovered dozens of...
The slow Tick‑ing time bomb: Tick APT group compromise of a DLP software developer in East Asia
ESET Research uncovered a campaign by APT group Tick against a data-loss prevention company in East Asia and found a previously unreported tool used by the...
5 signs you’ve fallen for a scam – and what to do next
Here’s how to know you have fallen victim to a scam – and what to do in order to undo or mitigate the damage. Online fraud...
APT hackers set a honeytrap to ensnare victims – Week in security with Tony Anscombe
A request to move an online conversation to a supposedly more secure platform may not be as well-meaning as it sounds Have you ever been asked...
Common WhatsApp scams and how to avoid them
Here’s a roundup of some of the most common tricks that fraudsters use to dupe their victims on WhatsApp – and what you can do to...
‘A woman from Mars’: Life in the pursuit of space exploration
An astrobiologist, analog astronaut, author and speaker, Dr. Michaela Musilova shares her experience as a woman at the forefront of space exploration and from her quest...
Love scam or espionage? Transparent Tribe lures Indian and Pakistani officials
ESET researchers analyze a cyberespionage campaign that distributes CapraRAT backdoors through trojanized and supposedly secure Android messaging apps – but also exfiltrates sensitive information ESET researchers...
What does $5,000 buy you on a hacking forum? – Week in security with Tony Anscombe
A bootkit that ESET researchers have discovered in the wild is the BlackLotus UEFI bootkit that is being peddled on hacking forums For a mere $5,000,...
MQsTTang: Mustang Panda’s latest backdoor treads new ground with Qt and MQTT
ESET researchers tease apart MQsTTang, a new backdoor used by Mustang Panda, which communicates via the MQTT protocol ESET researchers have analyzed MQsTTang, a new custom...
Avoiding data backup failures – Week in security with Tony Anscombe
Today is World Backup Day, but maybe we also need a “did you test your backups” day? When did you last attempt to restore your data?...
IOTW: Latitude Financial data breach affects 14 million people
Australian financial services company, Latitude Financial, has suffered a large-scale data break that exposed the personal information for more than 14 million customers. The breach was...
Twitter source code leaked via GitHub
Part of the source code for social media site Twitter has been leaked via source code repository GitHub, according to a DMCA takedown request. The DMCA...
IOTW: BreachForums shuts down after FBI arrests its top admin
Notorious dark web hacking forum BreachForums is reportedly shutting down following the arrest of one of its top administrators by the United States’ Federal Bureau of...
Top seven hacks and cyber security threats in APAC
In 2022, 59 percent of business in the Asia-Pacific region reported being the victim of a cyber attack, 32 percent reported being the victim of multiple...
What is phishing?
Phishing is a social engineering tactic that sees hackers attempt to gain access to personal or confidential information by posing as a legitimate company. In this...
IOTW: Ransomware gang allegedly hacks Ring doorbells
Russia-linked ransomware gang ALPHV has claimed to have launched a cyber attack against Amazon-owned domestic security company, Ring. Ring, which makes doorbells with video and sound...
What are DDoS attacks?
Distributed denial of service attacks, or DDoS attacks, see malicious actors attempt to disrupt a site by overwhelming its infrastructure with a large amount of internet...
IOTW: US Marshals Service suffers ransomware attack
The US Marshals Service (USMS), a federal law enforcement agency within the US Department of Justice (DoJ) has announced that it was the victim of a...
IOTW: Russian hackers target NATO sites with DDoS attack
The North Atlantic Treaty Organization (NATO) has been the victim of a series of distributed denial of service (DDoS) attacks, causing temporary disruption to some of...
Why healthcare providers are focusing on cyber resilience
The healthcare industry, especially within the Asia-Pacific region, has been the victim of a number of cyber attacks and data breaches within the last six months...
How Covid-19 impacted cyber security challenges, focus and spends
Survey methodology and respondent profiles The results in this report are from the Cyber Security Hub survey which we fielded to subscribers from May and June...
German airports hit with DDoS attack
Seven German airports have had their websites targeted by a suspected distributed denial of service (DDoS) attack. The attack, which took place on February 16, saw...
Microsoft Fixes New Azure AD Vulnerability Impacting Bing Search and Major Apps
Microsoft Fixes New Azure AD Vulnerability Impacting Bing Search and Major AppsMicrosoft has patched a misconfiguration issue impacting the Azure Active Directory (AAD) identity and access...
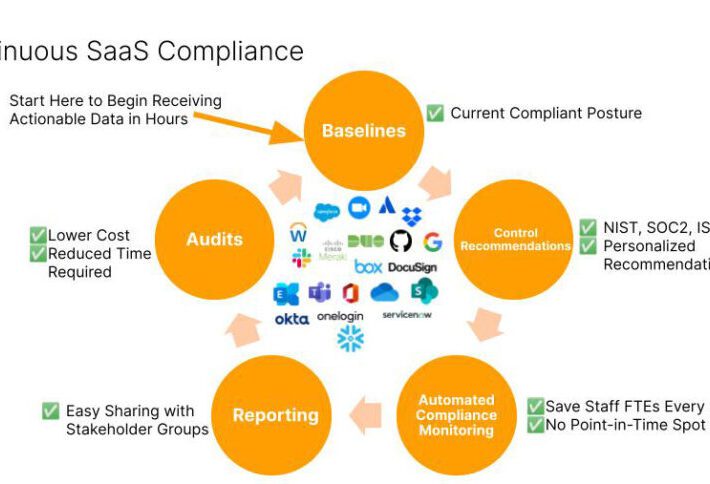
Reducing Risks and Threats with Continuous SaaS Compliance
Reducing Risks and Threats with Continuous SaaS ComplianceCISOs and GRC officers are quickly recognizing the growing threats posed by misconfigured SaaS applications and integrations between SaaS...
3CX Supply Chain Attack Campaign
3CX Supply Chain Attack CampaignOn March 29th 2023, CrowdStrike published a blog outlining a supply chain attack leveraging the 3CXDesktopApp - a softphone application from 3CX....
What is the impact of AI on cyber security awareness?
What is the impact of AI on cyber security awareness?The post What is the impact of AI on cyber security awareness? appeared first on Click Armor....
Avoiding data backup failures – Week in security with Tony Anscombe
Avoiding data backup failures – Week in security with Tony AnscombeToday is World Backup Day, but maybe we also need a "did you test your backups"...