An employee from the US Consumer Financial Protection Bureau (CFPB) has reportedly forwarded confidential records of roughly 256,000 consumers and confidential supervisory information of approximately 50...
Day: April 21, 2023
Evil Extractor Targets Windows Devices to Steal Sensitive Data
The attack tool known as Evil Extractor and developed by a company called Kodex as an “educational tool,” has been used by threat actors to target...
Trojanized Installers Used to Distribute Bumblebee Malware
Popular software tools such as Zoom, Cisco AnyConnect, ChatGPT and Citrix Workspace have been trojanized to distribute the malware known as Bumblebee. Secureworks’ Counter Threat Unit...
Did you mistakenly sell your network access? – Week in security with Tony Anscombe – Source: www.welivesecurity.com
Source: www.welivesecurity.com – Author: Editor. Many routers that are offered for resale contain sensitive corporate information and allow third-party connections to corporate networks Did you mistakenly...
Linux malware strengthens links between Lazarus and the 3CX supply‑chain attack – Source: www.welivesecurity.com
Source: www.welivesecurity.com – Author: Peter Kálnai. Similarities with newly discovered Linux malware used in Operation DreamJob corroborate the theory that the infamous North Korea-aligned group is...
North Korea’s Kimsuky APT Keeps Growing, Despite Public Outing
Globally, interest has surged around North Korea’s Kimsuky advanced persistent threat group (a.k.a. APT43) and its hallmarks. Still, the group is showing no signs of slowing...
Hacking Pickleball
Hacking Pickleball My latest book, A Hacker’s Mind, has a lot of sports stories. Sports are filled with hacks, as players look for every possible advantage...
Using the iPhone Recovery Key to Lock Owners Out of Their iPhones
This a good example of a security feature that can sometimes harm security: Apple introduced the optional recovery key in 2020 to protect users from online...
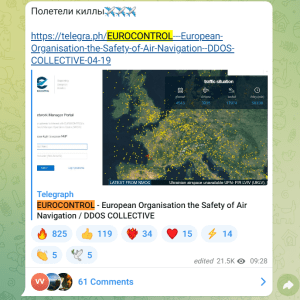
Pro-Russia hackers launched a massive attack against the EUROCONTROL agency – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. Pro-Russia hackers KillNet launched a massive DDoS attack against Europe’s air-traffic agency EUROCONTROL. Europe’s air-traffic control agency EUROCONTROL announced that...
Cisco fixed critical flaws in the Industrial Network Director and Modeling Labs solutions – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. Cisco released security updates to address critical security flaws in its Industrial Network Director and Modeling Labs solutions. Cisco released...
Intro to phishing: simulating attacks to build resiliency – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. Phishing attacks are a major threat to organizations, they remain a perennial choice of cybercriminals when it comes to hacking...
Multinational ICICI Bank leaks passports and credit card numbers – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. ICICI Bank leaked millions of records with sensitive data, including financial information and personal documents of the bank’s clients. ICICI...
VMware fixed a critical flaw in vRealize that allows executing arbitrary code as root – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. VMware fixed two severe flaws, tracked as CVE-2023-20864 and CVE-2023-20865, impacting the VMware Aria Operations for Logs product. The virtualization...
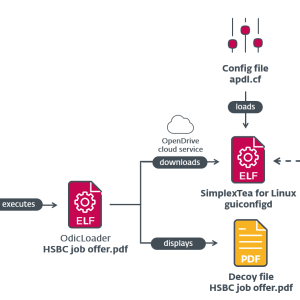
Lazarus APT group employed Linux Malware in recent attacks and was linked to 3CX supply chain attack – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. North Korea-linked APT group Lazarus employed new Linux malware in attacks that are part of Operation Dream Job. North Korea-linked APT...
Introduction to Tabletop Exercises (TTX) – A practical Guidebook for Organizations by Capgemini for GFCE – Global Forum on Cyber Expertise
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Navigating the Pandora’s Box that is ChatGPT: Insights from a Global CISO
Jonathan Fischbein is the Chief Information Security Officer for cyber security vendor Check Point Software. He has more than 25 years’ experience in high-tech security markets,...
Why cyber security should be treated as an ESG issue
EXECUTIVE SUMMARY: The World Economic Forum describes cyber security as one of the top five global risks, highlighting the need for organizations to integrate cyber security...
RSAC Fireside Chat: Cybersixgill crawls the Dark Web to uncover earliest signs of companies at risk
By Byron V. Acohido Adopting personas and rubbing elbows with criminal hackers and fraudsters is a tried-and-true way to glean intel in the Dark Web. Related:...
Breach Roundup: US CFPB, NCR and Rheinmetall – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1. Fraud Management & Cybercrime , Incident & Breach Response , Ransomware Also in Focus: Philippines Law Enforcement Agencies, RentoMojo and Point...
HIPAA Considerations for AI Tool Use in Healthcare Research – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1. The potential use cases for generative AI technology in healthcare appear limitless, but they’re weighted with an array of potential privacy,...
Cyber Experts Predict More Harmful Cyberattacks in Ukraine – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1. Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Ransomware Report Was Commissioned by the UK National Cyber Security Center...
Panel Discussion | The FTC Cha-Cha: Dancing to The Beat of Regulations – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1. Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Fortra Hacker Installed Tools on Victim Machines – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1. 3rd Party Risk Management , Fraud Management & Cybercrime , Governance & Risk Management Fortra Reveals Findings From GoAnywhere MFT Attack...
US Medical Service Data Breach Impacts 2.3M People
Shields Health Care Group (SHCG), a medical service provider in the United States, announced a data breach that compromised the personal information of more than 2.3...
Stay Ahead of Cyberthreats with Proactive Threat Hunting
In today’s digital age, cyber threats are an ever-present danger to organizations of all sizes. From ransomware attacks to data breaches, the consequences of a successful...
Cybercriminals Abusing an Abandoned WordPress Plugin for Malicious Code Injection
Threat actors found a new method to inject malicious code into websites. They are now using an abandoned WordPress plugin, Eval PHP. The plugin is still...
Millions of Records With Sensitive Data Leaked by ICICI Bank
ICICI Bank, an Indian multinational valued at more than $76 billion, with over 5,000 branches operating across India and 15 other countries worldwide has leaked millions...
SECURITY ALERT: Heimdal® Detects Massive MitID Smishing Campaign Targeting Nordea Bank Customers
On the 20th of April, Heimdal®’s SOC team has discovered that an unknown APT has been launching smishing attacks against Nordea Bank customers. The data analyzed...
3CX Breach Was a Double Supply Chain Compromise
We learned some remarkable new details this week about the recent supply-chain attack on VoIP software provider 3CX. The lengthy, complex intrusion has all the makings of...
VMware Patches Pre-Auth Code Execution Flaw in Logging Product – Source: www.securityweek.com – Author: Ryan Naraine –
Source: www.securityweek.com – Author: Ryan Naraine. Category & Tags: Application Security,Vulnerabilities,CVE-2023-20864,CVE-2023-20865 – Application Security,Vulnerabilities,CVE-2023-20864,CVE-2023-20865 Virtualization technology powerhouse VMware continues to encounter major security problems in its...