Source: www.troyhunt.com – Author: Troy Hunt I want to try something new here – bear with me here: Data breach processing is hard and the hardest...
Day: April 19, 2023
Iranian Nation-State Actor “Mint Sandstorm” Weaponizes N-day Flaws
A threat actor associated with Iranian nation-state hackers has been weaponizing N-day vulnerabilities, as well as deploying new techniques to access environments of interest. The threat...
#CYBERUK23: Threat Posed by ‘Irresponsible’ Use of Commercial Hacking Tools Increasing, NCSC Warns
Spyware, hackers for hire and access to other cyber capabilities such as hacking-as-a-service kits are expected to be in growing demand globally, the UK’s National Cyber...
Raspberry Robin Adopts Unique Evasion Techniques
Threat actors relying on the Raspberry Robin malware have been observed adopting unique evasion techniques to avoid detection. Security researchers at Check Point Research (CPR) published...
Nurse Call Systems, Infusion Pumps Riskiest Connected Medical Devices
Nurse call systems and infusion pumps have been found to be the riskiest connected medical devices, suggests a new report by asset visibility and security company...
US Company CommScope Hit by Ransomware
Following a ransomware attack back in March, sensitive employee data was compromised at CommScope, a major US telecommunications and IT infrastructure company. The Vice Society ransom gang...
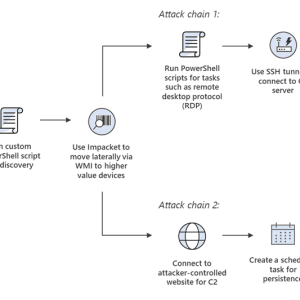
APT28 Russian Hackers Inject Routers with Jaguar Tooth Custom Malware
Researchers in US and UK warn that Russian state sponsored APT28 hackers deploy ”Jaguar Tooth” custom malware on routers in order to obtain unauthorized access. The...
Discarded, not destroyed: Old routers reveal corporate secrets – Source: www.welivesecurity.com
Source: www.welivesecurity.com – Author: Cameron Camp. When decommissioning their old hardware, many companies ‘throw the baby out with the bathwater’ Taking a defunct router out of...
US and UK agencies warn of Russia-linked APT28 exploiting Cisco router flaws – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. UK and US agencies are warning of Russia-linked APT28 group exploiting vulnerabilities in Cisco networking equipment. Russia-linked APT28 group accesses unpatched Cisco...
Iran-linked Mint Sandstorm APT targeted US critical infrastructure – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. An Iran-linked APT group tracked as Mint Sandstorm is behind a string of attacks aimed at US critical infrastructure between late 2021...
PWNYOURHOME, FINDMYPWN, LATENTIMAGE: 3 iOS Zero-Click exploits used by NSO Group in 2022 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. Citizen Lab reported that Israeli surveillance firm NSO Group used at least three iOS zero-click exploits in 2022. A new...
Experts temporarily disrupted the RedLine Stealer operations – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. Security experts from ESET, have temporarily disrupted the operations of the RedLine Stealer with the help of GitHub. ESET researchers...
Hackers actively exploit critical RCE bug in PaperCut servers
Print management software developer PaperCut is warning customers to update their software immediately, as hackers are actively exploiting flaws to gain access to vulnerable servers. PaperCut...
Google patches another actively exploited Chrome zero-day
Google has released a security update for the Chrome web browser to fix the second zero-day vulnerability found to be exploited in attacks this year. “Google...
Play ransomware gang uses custom Shadow Volume Copy data-theft tool
The Play ransomware group has developed two custom tools in .NET, namely Grixba and VSS Copying Tool, which it uses to improve the effectiveness of its...
March 2023 broke ransomware attack records with 459 incidents
March 2023 was the most prolific month recorded by cybersecurity analysts in recent years, measuring 459 attacks, an increase of 91% from the previous month and...
Google Search outage prevents some from seeing search results
Update 4/18/23: The outage appears to be resolved, with fewer people reporting issues. Google Search is currently suffering a partial outage that prevents the search engine...
US, UK warn of govt hackers using custom malware on Cisco routers
The US, UK, and Cisco are warning of Russian state-sponsored APT28 hackers deploying a custom malware named ‘Jaguar Tooth’ on Cisco IOS routers, allowing unauthenticated access...
ANZ Webinar | What You Don’t Know Can Hurt You: Open Source License Compliance and M&A Activity – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1. Sam Quakenbush Senior Director – Field Innovation & Strategy, Mend Sam Quakenbush has spent the past 10 years working for cyber...
Why FDA’s New Cyber Device Regs Are a ‘Watershed Moment’ – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1. Endpoint Security , Events , Healthcare Kevin Fu of Northeastern University on How the Regulations Will Ensure Uniformity Marianne Kolbasuk McGee...
Considerations for Building Successful Security Governance – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1. Governance & Risk Management , Identity Governance & Administration , IT Risk Management Kaiser Permanente’s Eric Liederman and Steven Frank on...
Ukraine Facing Phishing Attacks, Information Operations – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1. Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Russia’s Invasion Tactics Include Creating Fake Hacktivist Groups, Researchers Find Mathew J....
WhatsApp, Signal Preview UK Exit Over Threat to Encryption – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1. Encryption & Key Management , Geo Focus: The United Kingdom , Geo-Specific UK’s Online Safety Bill Criticized for Infringing on Private...
Threat Report Reveals Hope Despite Active Threat Landscape – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1. Using a Layered Protection Strategy Is the Best Defense Against Cybercrime Grayson Milbourne • April 12, 2023 Companies have...
RSAC Fireside Chat: ‘Protective DNS’ directs smart audits, automated remediation to IP addresses
By Byron V. Acohido Domain Name Service. DNS. It’s the phone directory of the Internet. Related: DNS — the good, bad and ugly Without DNS the...
Cyberattacks Can Cost Enterprises Up to 30% of Operating Income According to ThreatConnect
ARLINGTON, Va. – April 18, 2023 – ThreatConnect, Inc, maker of leading threat intelligence operations (TI Ops) and risk quantification solutions, announced today the release of the...
Report: Over Half of North American Consumers Are Open to Passwordless
TORONTO, April 18, 2023 /PRNewswire/ — 1Password, the leader in human-centric security and privacy, today released its Preparing for a Passwordless Future report. The report revealed a strong consumer appetite for...
Netwrix Annual Security Survey: 68% of Organizations Experienced a Cyberattack Within the Last 12 Months
FRISCO, Texas, April 18, 2023 – Netwrix, a cybersecurity vendor that makes data security easy, today announced the release of its annual global 2023 Hybrid Security Trends Report. It...
KnowBe4 Phishing Test Results Reveal IT and Online Services Emails Drive Dangerous Attack Trend
Tampa Bay, FL (April 18, 2023) – KnowBe4, the provider of the world’s largest security awareness training and simulated phishing platform, today announced the results of...
Marlinspike Adds Charles Carmakal to its Advisory Board
ANNAPOLIS, Md., April 18, 2023 /PRNewswire/ — Marlinspike Partners, a venture capital investment firm focusing on disruptive dual-use technology companies advancing national security and commercial interests of the United...