For the past seven years, a malware-based proxy service known as “Faceless” has sold anonymity to countless cybercriminals. For less than a dollar per day, Faceless...
Day: April 18, 2023
New ”Domino” Malware Strain Targets Corporate Networks
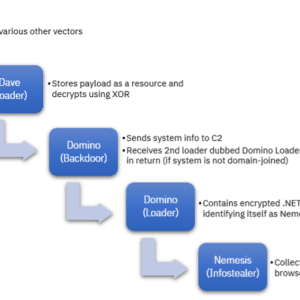
Researchers recently discovered a new malware family named “Domino”, allegedly created by ITG14, also known as the FIN7 threat group. Reportedly, ex-Conti hackers have been using...
Rheinmetall Suffers Another Cyberattack – Company Operations Still Functional
Rheinmetall, a leading German armaments and technology company, was targeted by a cyberattack over the weekend. The attack, however, did not affect company operations, according to officials....
Microsoft: Iranian hackers behind retaliatory cyberattacks on US orgs
Microsoft has discovered that an Iranian hacking group known as ‘Mint Sandstorm’ is conducting cyberattacks on US critical infrastructure in what is believed to be retaliation...
Australians lost a record $3.1 billion to scams last year
The Australian Competition & Consumer Commission (ACCC) says Australians lost a record $3.1 billion to scams in 2022, an 80% increase over the total losses recorded...
New sandbox escape PoC exploit available for VM2 library, patch now
A security researcher has released, yet another sandbox escape proof of concept (PoC) exploit that makes it possible to execute unsafe code on a host running...
The Attacks that can Target your Windows Active Directory
Active Directory is at the center of many attacks as it is still the predominant source of identity and access management in the enterprise. Hackers commonly...
Goldoson Malware Found in Dozens of Google Play Store Apps
Security researchers have discovered a new malicious software library capable of collecting lists of installed applications, a history of Wi-Fi and Bluetooth device information as well...
MuddyWater Uses SimpleHelp to Target Critical Infrastructure Firms
The Iranian government-sponsored threat actor known as MuddyWater has been observed using the legitimate SimpleHelp remote support software tool to achieve persistence on victim devices. According...
NSO Group’s Pegasus Spyware Found on High-Risk iPhones
Users in multiple countries have been impacted by spyware previously linked with NSO Group’s Pegasus malware over the past six months. The findings by Jamf Threat...
Researchers Discover First Ever Major Ransomware Targeting macOS
The infamous LockBit ransomware gang has developed a version of their malware for macOS devices — the first ever foray into Apple’s territory by a major...
Where There’s No Code, There’s No SDLC
We’ve come to rely heavily on the software development lifecycle (SDLC) as the go-to method to get security ingrained into development processes. In fact, the assumption...
APT41 Taps Google Red Teaming Tool in Targeted Info-Stealing Attacks
The advanced persistent threat known as APT41 has pressed into service an open source, red-teaming tool, Google Command and Control (GC2), for use in cyber espionage...
Why Your Anti-Fraud, Identity & Cybersecurity Efforts Should Be Merged
Across early-stage startups and mature public companies alike, we’re seeing a convergence of fraud prevention, identity and access management (IAM), and cybersecurity. It’s time for businesses...
‘Goldoson’ Malware Sneaks into Google Play Apps, Racks Up 100M Downloads
Malware that can steal data and commit click fraud has hitched a ride into 60 mobile apps, via an infected third-party library. The infected apps have logged more...
Beyond CVEs: The Key to Mitigating High-Risk Security Exposures
In 2022, the National Institute of Standards and Technology reported more than 23,000 new vulnerabilities, the largest spike ever recorded within one calendar year. Alarmingly, this...
Recycled Core Routers Expose Sensitive Corporate Network Info
Cameron Camp had purchased a Juniper SRX240H router last year on eBay, to use in a honeypot network he was building to study remote desktop protocol...
As Consumer Privacy Evolves, Here’s How You Can Stay Ahead of Regulations
Proposition 24, also known as the California Privacy Rights Act (CPRA), went into effect in January. Passed by California voters in November 2020, the CPRA increases...
ZeroFox Acquires LookingGlass
On Monday, ZeroFox announced plans to acquire LookingGlass, a threat intelligence and attack surface management company, for roughly $26 million. ZeroFox provides protection against phishing and...
Global Automotive Cybersecurity Report 2022 – Automotive Cyber Threat Landscape in Light of New Regulations by Upstream
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CISA adds bugs in Chrome and macOS to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. US Cybersecurity and Infrastructure Security Agency (CISA) added Chrome and macOS vulnerabilities to its Known Exploited Vulnerabilities catalog. U.S. Cybersecurity...
The intricate relationships between the FIN7 group and members of the Conti ransomware gang – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. A new malware, dubbed Domino, developed by the FIN7 cybercrime group has been used by the now-defunct Conti ransomware gang....
Israeli surveillance firm QuaDream is shutting down amidst spyware accusations – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. The Israeli surveillance firm QuaDream is allegedly shutting down its operations after Citizen Lab and Microsoft uncovered their spyware. Last week...
New QBot campaign delivered hijacking business correspondence – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. Kaspersky researchers warn of a new QBot campaign leveraging hijacked business emails to deliver malware. In early April, Kaspersky experts...
CISA: Why Healthcare Is No Longer Off-Limits for Attackers – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1. Healthcare entities of all types and sizes could be the next targets of major cybersecurity attacks, said Nitin Natarajan, deputy director...
How New Federal Cyber Resources Can Help Healthcare Entities – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1. Healthcare , Industry Specific , Information Sharing CISO Erik Decker Shares New HHS Advisory Group Resources at HIMSS Conference Marianne Kolbasuk...
APAC Panel | Level Up Your Security Stack: EDR vs Endpoint Privilege Management – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1. Sean Boulter Solution Architect, Salt Security Sean Boulter is a technical leader with Salt Security where he helps his customers protect...
US Charges Chinese Officials With Running Troll Farm – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1. Fraud Management & Cybercrime , Social Media Also: Conspiracy to Transmit Interstate Threats and Commit Interstate Harassment David Perera (@daveperera) •...
7 tips for tackling cyber security technical debt
EXECUTIVE SUMMARY: The cyber risk landscape is evolving. Novel attack types are appearing at an unprecedented rate. Cyber criminals are constantly seeking new ways to infiltrate...
Twitter no longer exists, it’s just X Corp. now
EXECUTIVE SUMMARY: In a move sparking intense speculation, Twitter technically “no longer exists” after a merge with X Corp., according to a document submitted to a...