Or I’m No Fool with Weaponized AI By Guy Rosefelt, Chief Product Officer, Sangfor Technologies Okay, I admit the title is clickbait to get you to...
Day: April 15, 2023
2023: What Awaits Us?
By Ashley Stephenson, CTO, Corero Network Security When it comes to cyber security, one thing that 2022 and just about any recent year will be remembered...
Siemens Metaverse exposes sensitive corporate data
Siemens Metaverse, a virtual space built to mirror real machines, factories, and other highly complex systems, has exposed sensitive data, including the company’s office plans and...
CISA adds bugs in Android and Novi Survey to its Known Exploited Vulnerabilities catalog
US Cybersecurity and Infrastructure Security Agency (CISA) added Android and Novi Survey flaws to its Known Exploited Vulnerabilities catalog. U.S. Cybersecurity and Infrastructure Security Agency (CISA)...
Volvo retailer leaks sensitive files
The Brazilian retail arm of car manufacturing giant Volvo leaked sensitive files, putting its clientele in the vast South American country in peril. Volvo’s retailer in...
A cyberattack on the Cornwall Community Hospital in Ontario is causing treatment delays
The Cornwall Community Hospital in Ontario, Canada, is under a cyber attack that is causing delays to scheduled and non-urgent care. A cyberattack on the Cornwall...
Google fixed the first Chrome zero-day of 2023
Google released an emergency security update to address a zero-day vulnerability in Chrome which is actively exploited in the wild. Google released an emergency security update to address the first Chrome zero-day...
Android malware infiltrates 60 Google Play apps with 100M installs
A new Android malware named ‘Goldoson’ has infiltrated Google Play through 60 legitimate apps that collectively have 100 million downloads. The malicious malware component is part...
The Week in Ransomware – April 14th 2023 – A Focus on Stolen Data
It has been mostly a quiet week regarding ransomware, with only a few bits of info released on older attacks and some reports released on existing...
European Scrutiny of ChatGPT Grows as Probes Increase
Artificial Intelligence & Machine Learning , General Data Protection Regulation (GDPR) , Next-Generation Technologies & Secure Development Concerns Raised Over ChatGPT’s Compliance With GDPR Akshaya Asokan...
HIMSS23: Tackling Some of Healthcare’s Top Cyber Challenges
Events , Healthcare , HIMSS The Annual Health IT Event Will Showcase Security, Privacy Marianne Kolbasuk McGee (HealthInfoSec) • April 14, 2023 Here’s one...
Data Protection: Data Has No Jurisdiction
Cloud Security , Incident & Breach Response , Next-Generation Technologies & Secure Development Skyhigh Security’s Rodman Ramezanian on Securing Data from Devices to the Cloud Cal...
Overcoming Federal Sector Compliance Regulation Challenges
The sheer volume of federal regulations in place makes it almost impossible for agencies to monitor and comply with all of them, much less understand the...
ISMG Editors: RSA Conference 2023 Preview
Events , RSA Conference , RSA Conference Videos Special Guests Join Editors to Share RSA Predictions, Themes, Coverage Anna Delaney (annamadeline) • April 14, 2023 ...
APT36 Running Espionage Ops Against India’s Education Sector
Fraud Management & Cybercrime , Social Engineering Pakistan-Linked APT Group Using Spear-Phishing to Plant Info Stealer Malware Jayant Chakravarti (@JayJay_Tech) • April 14, 2023 ...
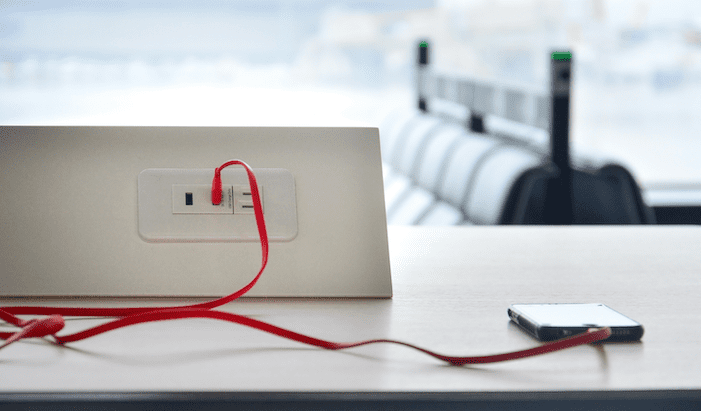
Why is ‘Juice Jacking’ Suddenly Back in the News?
KrebsOnSecurity received a nice bump in traffic this week thanks to tweets from the Federal Bureau of Investigation (FBI) and the Federal Communications Commission (FCC) about...
Russian SolarWinds Culprits Launch Fresh Barrage of Espionage Cyberattacks
As part of its ongoing invasion of Ukraine, Russian intelligence has once again enlisted the services of hacker group Nobelium/APT29, this time to spy on foreign...
Why xIoT Devices Are Cyberattackers’ Gateway Drug for Lateral Movement
Extended IoT devices (xIoT) stand as a perennial favorite for cyberattackers seeking to move laterally and establish persistence within enterprise networks. They’ve got everything the bad...
Software-Dependency Data Delivers Security to Developers
Developers interested in gauging the security of the open source components have an abundant number of choices, but still have to choose to use the information...
Security Is a Revenue Booster, Not a Cost Center
Security has historically been seen as a cost center, which has led to it being given as little money as possible. Many CISOs, CSOs, and CROs...
Bugs in Manarium Play-to-Earn Platform Showcase Crypto-Gaming Insecurity
A proof-of-concept (PoC) hack of the Manarium play-to-earn (P2E) gaming platform allowed researchers to arbitrarily change their scores to win daily tournaments and collect crypto tokens,...
Western Digital Hackers Demand 8-Figure Ransom Payment for Data
After stealing around 10TB of data from Western Digital Corp., the computer drive manufacturer behind digital storage brand SanDisk, hackers are now negotiating a ransom payment...
SASE Market Worth $5.9B by 2028 — Report by MarketsandMarkets™
CHICAGO, April 14, 2023 /PRNewswire/ — The global SASE Market size is projected to grow from USD 1.9 billion in 2023 to USD 5.9 billion by 2028, at a Compound Annual Growth Rate (CAGR) of...
What the Recent Collapse of SVB Means for Privacy
With the recent collapse of Silicon Valley Bank (SVB), we’re seeing a culmination of events leading to a perfect storm for digital bad actors. As businesses...
Friday Squid Blogging: Colossal Squid
Interesting article on the colossal squid, which is larger than the giant squid. The article answers a vexing question: So why do we always hear about...
Upcoming Speaking Engagements
About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I’ve been writing about security issues on my blog...
Hacking Suicide
Hacking Suicide Here’s a religious hack: You want to commit suicide, but it’s a mortal sin: your soul goes straight to hell, forever. So what you...
Gaining an Advantage in Roulette
You can beat the game without a computer: On a perfect [roulette] wheel, the ball would always fall in a random way. But over time, wheels...
Bypassing a Theft Threat Model
Thieves cut through the wall of a coffee shop to get to an Apple store, bypassing the alarms in the process. I wrote about this kind...