Apple has released emergency security updates to address two new zero-day vulnerabilities exploited in attacks to compromise iPhones, Macs, and iPads. “Apple is aware of a...
Day: April 7, 2023
Exploit available for critical bug in VM2 JavaScript sandbox library
Proof-of-concept exploit code has been released for a recently disclosed critical vulnerability in the popular VM2 library, a JavaScript sandbox that is used by multiple software to...
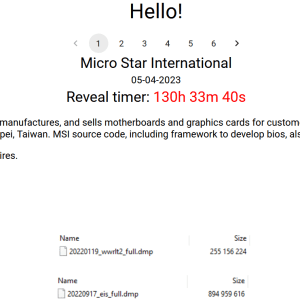
MSI confirms security breach following ransomware attack claims
Following reports of a ransomware attack, Taiwanese PC vendor MSI (short for Micro-Star International) confirmed today that its network was breached in a cyberattack. Earlier this week,...
Massive Balada Injector campaign attacking WordPress sites since 2017
An estimated one million WordPress websites have been compromised during a long-lasting campaign that exploits “all known and recently discovered theme and plugin vulnerabilities” to inject...
Microsoft Edge can now generate images with AI
Microsoft Edge has become the first and only browser with an integrated AI image generator, allowing users to create images that do not exist yet, powered...
FBI warns of companies exploiting sextortion victims for profit
For-profit companies reportedly linked to sextortion activity are targeting victims using various deceptive tactics to pressure them into paying for “assistance” services provided by non-profit agencies...
Flipper Zero banned by Amazon for being a ‘card skimming device’
Amazon has banned the sale of the Flipper Zero portable multi-tool for pen-testers as it no longer allows its sale on the platform after tagging it...
Cybercriminals ‘CAN’ Steal Your Car, Using Novel IoT Hack
Automotive security experts have uncovered a novel method for stealing cars by breaking into their control systems through a headlight. The key (so to speak) is...
Fight AI With AI
On Wednesday, KPMG Studios, the consulting giant’s incubator, launched Cranium, a startup to secure artificial intelligence (AI) applications and models. Cranium’s “end-to-end AI security and trust...
Twitter ‘Shadow Ban’ Bug Gets Official CVE
A vulnerability in Twitter’s code was recently discovered that allows users to game the algorithm with mass blocking actions from large numbers of accounts, in an...
US Space Force Requests $700M for Cybersecurity Blast Off
US Space Force top brass have requested a $700 million investment in cybersecurity as part of the military branch’s overall $30 billion 2024 budget. The Russian...
DDoS attacks rise as pro-Russia groups attack Finland, Israel
Image: Golden Sikorka/Adobe Stock The pro-Russia hacker group NoName057(16) reportedly claimed it was behind Denial of Service (DoS) attacks against the Finnish parliament’s website on Tuesday,...
Weekly Update 342
Next time I post a poll about something as simple as “when is next Friday”, I don’t expect I’ll get as much interest. Of course “next...
Phishers migrate to Telegram
Experts warn that Telegram is becoming a privileged platform for phishers that use it to automate their activities and for providing various services. Kaspersky researchers have...
OCR Labs exposes its systems, jeopardizing major banking clients
A digital identification tool provided by OCR Labs to major banks and government agencies leaked sensitive credentials, putting clients at severe risk. London-based OCR Labs is...
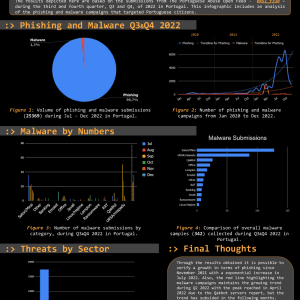
Threat Report Portugal: Q3 & Q4 2022
The Threat Report Portugal: H2 2022 compiles data collected on the malicious campaigns that occurred from July to December, H2, 2022. The Portuguese Abuse Open Feed 0xSI_f33d is...
Analyzing attacks conducted by North Korea-linked ARCHIPELAGO APT group
Google’s Threat Analysis Group (TAG) warns of a North Korea-linked cyberespionage group tracked as ARCHIPELAGO. Google’s Threat Analysis Group (TAG) is warning of the North Korea-linked...
Steer clear of tax scams – Week in security with Tony Anscombe
In a rush to file your taxes? Watch out for cybercriminals preying on stressed taxpayers as Tax Day looms large on the horizon. The IRS-approved tax...
Cleaning up your social media and passwords: What to trash and what to treasure
Give your social media presence a good spring scrubbing, audit your passwords and other easy ways to bring order to your digital chaos Spring has sprung,...
Designing Your Threat Hunting Framework from Scratch – Core Essentials
A threat hunting framework is a collation of data-driven adversarial scenarios, backed up by hypothetical, field-tested, or time-honored TTPs (i.e., Tactics, Techniques, and Procedures). Serving a...
Research on AI in Adversarial Settings
New research: “Achilles Heels for AGI/ASI via Decision Theoretic Adversaries“: As progress in AI continues to advance, it is important to know how advanced systems will...
What is an ‘island hopping’ attack? (and how to stop one)
EXECUTIVE SUMMARY: At the mention of island hopping, you’re likely dreaming about adventures in Hawaii, the Caribbean, or similar destinations with majestic views and white-sand beaches....
Ukrainian hackers spend $25,000 of pro-Russian blogger’s money on sex toys
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s. View all...
A fireside chat with four CISOs about how they secure their cybersecurity firms from attack
On Tuesday 11 April, I’ll be joined by the CISOs of security firms Wiz, Rubrik, Noname, and Abnormal, for a friendly chat about how they protect...
Own a Nexx “smart” alarm or garage door opener? Get rid of it, or regret it
Nexx is a manufacturer of “smart” devices – plus, alarms, garage door openers, that kind of thing. Unfortunately their response to vulnerabilities is not-so-smart. According to...