The role of API inventory in SBOM and cyber securityThis article explores the importance of API inventory in the software bill of materialsRead MoreArticles RSS FeedThis...
Month: March 2023
Digital Spring Cleaning: Seven Steps for Faster, Safer Devices
Digital Spring Cleaning: Seven Steps for Faster, Safer Devices Throw open the windows and let in some fresh air. It’s time for spring cleaning. And that...
How You May be Sharing Private Information Online Without Even Knowing
How You May be Sharing Private Information Online Without Even Knowing When I started my job as Cybermum – over 10 years ago – it was...
What Parents Need To Know About TikTok’s New Screen Time Limits
What Parents Need To Know About TikTok’s New Screen Time Limits Social media platforms often get a hard time by us parents. But a recent announcement...
QNAP warns customers to patch Linux Sudo flaw in NAS devices
QNAP warns customers to patch Linux Sudo flaw in NAS devicesTaiwanese hardware vendor QNAP warns customers to secure their Linux-powered network-attached storage (NAS) devices against a...
SafeMoon ‘burn’ bug abused to drain $8.9 million from liquidity pool
SafeMoon ‘burn’ bug abused to drain $8.9 million from liquidity poolThe SafeMoon token liquidity pool lost $8.9 million after a hacker exploited a newly created 'burn'...
Steam will drop support for Windows 7 and 8 in January 2024
Steam will drop support for Windows 7 and 8 in January 2024Valve announced that its Steam online game platform will officially drop support for the Windows...
Hackers compromise 3CX desktop app in a supply chain attack
Hackers compromise 3CX desktop app in a supply chain attackA digitally signed and trojanized version of the 3CX Voice Over Internet Protocol (VOIP) desktop client is...
Promoting company success with AI-based talent recruitment
Promoting company success with AI-based talent recruitmentBy Devin Partida, Editor-in-Chief, Rehack.com. There’s no question that cyber security is becoming a top concern for virtually every company,...
10 ways ChatGPT is disrupting the financial services industry
10 ways ChatGPT is disrupting the financial services industryEXECUTIVE SUMMARY: In today’s fast-paced financial services industry, banks and other financial institutions are looking for new ways...
Live Webinar | Education Cybersecurity Best Practices: Devices, Ransomware, Budgets and Resources
Live Webinar | Education Cybersecurity Best Practices: Devices, Ransomware, Budgets and ResourcesPost ContentRead MoreDataBreachToday.com RSS Syndication
FDA Will Begin Rejecting Medical Devices Over Cyber Soon
FDA Will Begin Rejecting Medical Devices Over Cyber SoonGuidance Says Device Makers Must Now Give Cyber Details for New Product SubmissionsThe Food and Drug Administration on...
Cisco Buys Startup Lightspin to Address Cloud Security Risks
Cisco Buys Startup Lightspin to Address Cloud Security RisksLightspin Deal Will Help Prioritize and Remediate Issues for Cloud-Native ResourcesCisco plans to purchase its second cloud security...
Airbus, Atos Ax Deal for Minority Stake in Evidian Cyber Arm
Airbus, Atos Ax Deal for Minority Stake in Evidian Cyber ArmAircraft Manufacturer's Bid for 30% Stake in Evidian Splinters on Negotiating TableAirbus has halted efforts to...
Tech Luminaries Call for Pause in AI Development
Tech Luminaries Call for Pause in AI DevelopmentJust Because AI Can Doesn't Mean AI Should, Say Letter SignatoriesA slew of top tech executives and artificial intelligence...
How to Overcome 5 Common Obstacles to Implementing Zero Trust
How to Overcome 5 Common Obstacles to Implementing Zero Trust 6 min read ZTNA offers significant security advantages, but key obstacles can hinder a successful implementation....
USENIX Security ’22 – Mohannad Ismail, Andrew Quach, Christopher Jelesnianski, Yeongjin Jang, Changwoo Min – ‘Tightly Seal Your Sensitive Pointers With PACTight’
USENIX Security ’22 – Mohannad Ismail, Andrew Quach, Christopher Jelesnianski, Yeongjin Jang, Changwoo Min – ‘Tightly Seal Your Sensitive Pointers With PACTight’Our thanks to USENIX for...
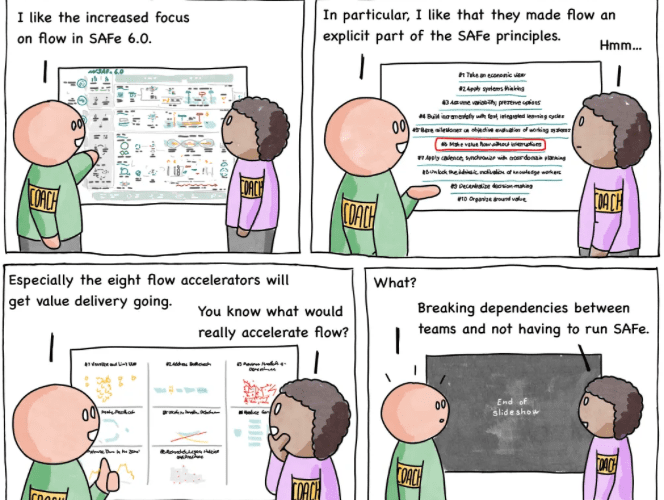
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnarav – #234 – SAFe Flow
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnarav – #234 – SAFe Flow via the respected Software Engineering expertise of Mikkel Noe-Nygaard as well as the lauded...
API Security 101 for Developers: How to Easily Secure Your APIs
API Security 101 for Developers: How to Easily Secure Your APIsAPI security is an ongoing process that demands continual attention and effort from everyone on the...
Everything to Know About ISO 27001 Internal Audits
Everything to Know About ISO 27001 Internal AuditsWhen a restaurant expects an inspection from the Health Department, management takes a number of steps to prepare. The...
North Korean threat actor APT43 pivots back to strategic cyberespionage
North Korean threat actor APT43 pivots back to strategic cyberespionageWhen it comes to threat actors working for the North Korean government, most people have heard of...
USENIX Security ’22 – Bernd Prünster, Alexander Marsalek, Thomas Zefferer – ‘Total Eclipse Of The Heart – Disrupting The InterPlanetary File System’
USENIX Security ’22 – Bernd Prünster, Alexander Marsalek, Thomas Zefferer – ‘Total Eclipse Of The Heart – Disrupting The InterPlanetary File System’Our thanks to USENIX for...
USENIX Security ’22 – Bernd Prünster, Alexander Marsalek, Thomas Zefferer – ‘Total Eclipse Of The Heart – Disrupting The InterPlanetary File System’
USENIX Security ’22 – Bernd Prünster, Alexander Marsalek, Thomas Zefferer – ‘Total Eclipse Of The Heart – Disrupting The InterPlanetary File System’Our thanks to USENIX for...
Spera Unveils Platform for Finding and Tracking Identities
Spera Unveils Platform for Finding and Tracking Identities Spera emerged from stealth today to launch a namesake platform that discovers and tracks identities to enable organizations...
North Korean APT43 Group Uses Cybercrime to Fund Espionage Operations
North Korean APT43 Group Uses Cybercrime to Fund Espionage OperationsA new North Korean nation-state cyber operator has been attributed to a series of campaigns orchestrated to...
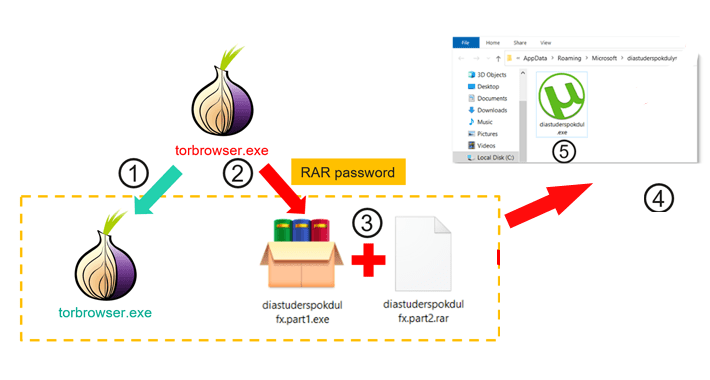
Trojanized TOR Browser Installers Spreading Crypto-Stealing Clipper Malware
Trojanized TOR Browser Installers Spreading Crypto-Stealing Clipper MalwareTrojanized installers for the TOR anonymity browser are being used to target users in Russia and Eastern Europe with clipper...
How to Build a Research Lab for Reverse Engineering — 4 Ways
How to Build a Research Lab for Reverse Engineering — 4 WaysMalware analysis is an essential part of security researcher's work. But working with malicious samples...
Mélofée: Researchers Uncover New Linux Malware Linked to Chinese APT Groups
Mélofée: Researchers Uncover New Linux Malware Linked to Chinese APT GroupsAn unknown Chinese state-sponsored hacking group has been linked to a novel piece of malware aimed...
Spyware Vendors Caught Exploiting Zero-Day Vulnerabilities on Android and iOS Devices
Spyware Vendors Caught Exploiting Zero-Day Vulnerabilities on Android and iOS DevicesA number of zero-day vulnerabilities that were addressed last year were exploited by commercial spyware vendors...
Clouds vs Edges: Which Computing Wins the Race?
Clouds vs Edges: Which Computing Wins the Race?One of the most pressing challenges for businesses today is finding the right balance between cutting-edge technology and practical...