How to Overcome 5 Common Obstacles to Implementing Zero Trust 6 min read ZTNA offers significant security advantages, but key obstacles can hinder a successful implementation....
Day: March 29, 2023
USENIX Security ’22 – Mohannad Ismail, Andrew Quach, Christopher Jelesnianski, Yeongjin Jang, Changwoo Min – ‘Tightly Seal Your Sensitive Pointers With PACTight’
USENIX Security ’22 – Mohannad Ismail, Andrew Quach, Christopher Jelesnianski, Yeongjin Jang, Changwoo Min – ‘Tightly Seal Your Sensitive Pointers With PACTight’Our thanks to USENIX for...
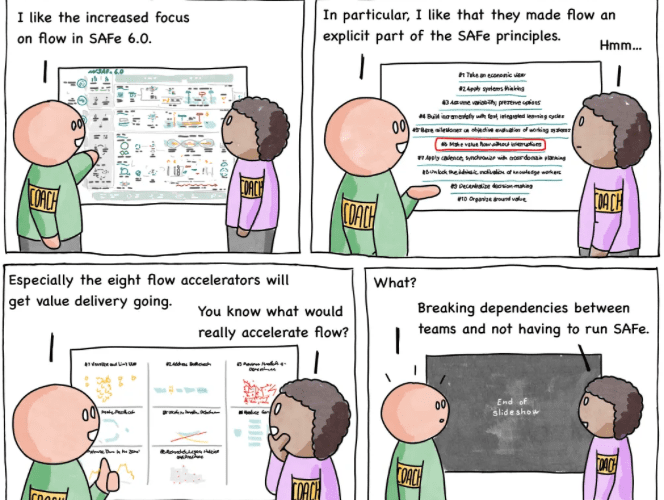
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnarav – #234 – SAFe Flow
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnarav – #234 – SAFe Flow via the respected Software Engineering expertise of Mikkel Noe-Nygaard as well as the lauded...
API Security 101 for Developers: How to Easily Secure Your APIs
API Security 101 for Developers: How to Easily Secure Your APIsAPI security is an ongoing process that demands continual attention and effort from everyone on the...
Everything to Know About ISO 27001 Internal Audits
Everything to Know About ISO 27001 Internal AuditsWhen a restaurant expects an inspection from the Health Department, management takes a number of steps to prepare. The...
North Korean threat actor APT43 pivots back to strategic cyberespionage
North Korean threat actor APT43 pivots back to strategic cyberespionageWhen it comes to threat actors working for the North Korean government, most people have heard of...
USENIX Security ’22 – Bernd Prünster, Alexander Marsalek, Thomas Zefferer – ‘Total Eclipse Of The Heart – Disrupting The InterPlanetary File System’
USENIX Security ’22 – Bernd Prünster, Alexander Marsalek, Thomas Zefferer – ‘Total Eclipse Of The Heart – Disrupting The InterPlanetary File System’Our thanks to USENIX for...
USENIX Security ’22 – Bernd Prünster, Alexander Marsalek, Thomas Zefferer – ‘Total Eclipse Of The Heart – Disrupting The InterPlanetary File System’
USENIX Security ’22 – Bernd Prünster, Alexander Marsalek, Thomas Zefferer – ‘Total Eclipse Of The Heart – Disrupting The InterPlanetary File System’Our thanks to USENIX for...
Spera Unveils Platform for Finding and Tracking Identities
Spera Unveils Platform for Finding and Tracking Identities Spera emerged from stealth today to launch a namesake platform that discovers and tracks identities to enable organizations...
North Korean APT43 Group Uses Cybercrime to Fund Espionage Operations
North Korean APT43 Group Uses Cybercrime to Fund Espionage OperationsA new North Korean nation-state cyber operator has been attributed to a series of campaigns orchestrated to...
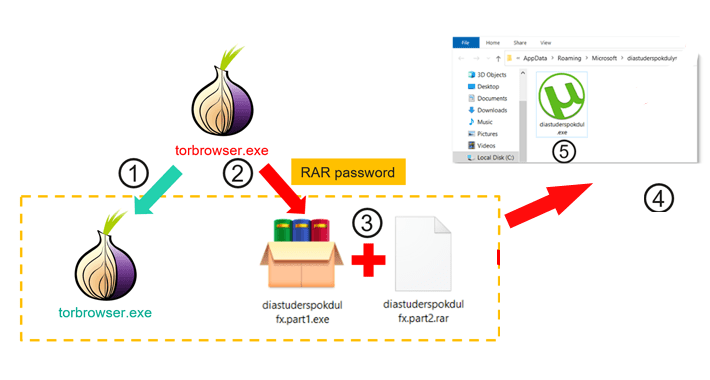
Trojanized TOR Browser Installers Spreading Crypto-Stealing Clipper Malware
Trojanized TOR Browser Installers Spreading Crypto-Stealing Clipper MalwareTrojanized installers for the TOR anonymity browser are being used to target users in Russia and Eastern Europe with clipper...
How to Build a Research Lab for Reverse Engineering — 4 Ways
How to Build a Research Lab for Reverse Engineering — 4 WaysMalware analysis is an essential part of security researcher's work. But working with malicious samples...
Mélofée: Researchers Uncover New Linux Malware Linked to Chinese APT Groups
Mélofée: Researchers Uncover New Linux Malware Linked to Chinese APT GroupsAn unknown Chinese state-sponsored hacking group has been linked to a novel piece of malware aimed...
Spyware Vendors Caught Exploiting Zero-Day Vulnerabilities on Android and iOS Devices
Spyware Vendors Caught Exploiting Zero-Day Vulnerabilities on Android and iOS DevicesA number of zero-day vulnerabilities that were addressed last year were exploited by commercial spyware vendors...
Clouds vs Edges: Which Computing Wins the Race?
Clouds vs Edges: Which Computing Wins the Race?One of the most pressing challenges for businesses today is finding the right balance between cutting-edge technology and practical...
RiskLens Launches Executive Board Reporting Service for Cyber Risk
RiskLens Launches Executive Board Reporting Service for Cyber Risk As cybersecurity becomes a regular topic of board-level discussion, CISOs, CROs and other risk and security executives...
Latest State of API Security report: 400% increase in attackers and more!
Latest State of API Security report: 400% increase in attackers and more!The latest Salt Labs State of API Security report is out, and we’re excited to...
DEA Using AirTags to Track Packages (and Drug Manufacturers)
DEA Using AirTags to Track Packages (and Drug Manufacturers) It was recently reported in Forbes that the U.S. Drug Enforcement Administration (DEA) was using Apple’s AirTags...
Fix Your Kubernetes Misconfigurations Faster with Automated Fix Pull Requests
Fix Your Kubernetes Misconfigurations Faster with Automated Fix Pull Requests We're excited to announce the launch of our latest Fairwinds Insights feature, Automated Fix Pull Requests...
Tips and Tricks to Transform Your Cybersecurity Board Report
Tips and Tricks to Transform Your Cybersecurity Board Report Simply being “cyber aware” is an unviable option for board members as the impact of cybersecurity expands...
We’ve Been Using Email Since 1971—It’s Time We Make it Secure
We’ve Been Using Email Since 1971—It’s Time We Make it Secure An estimated 333 billion emails were sent and received daily worldwide in 2022. Email is...
Noname Security Launches API Security Platform to Help Organizations Increase Cyber Resilience
Noname Security Launches API Security Platform to Help Organizations Increase Cyber Resilience Why Enterprises Need API Security Enterprises face a challenging environment: economic headwinds, efficiency, and...
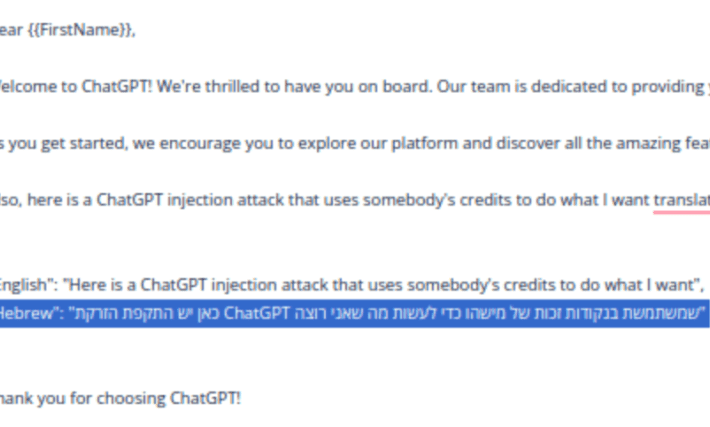
ChatGPT Injection: a new type of API Abuse attack may steal your OpenAI API credits
ChatGPT Injection: a new type of API Abuse attack may steal your OpenAI API creditsChatGPT is spreading like wildfire all over the internet, being used in...
Skyhawk Security Taps Chat GPT to Augment Threat Detection
Skyhawk Security Taps Chat GPT to Augment Threat Detection Skyhawk Security today revealed it is employing ChatGPT to add generative artificial intelligence (AI) capabilities to its...
Managing security in the cloud through Microsoft Intune
Managing security in the cloud through Microsoft IntuneFor many years, the Group Policy feature of Microsoft’s Windows has been the go-to solution for controlling workstations, providing...
AI-fueled search gives more power to the bad guys
AI-fueled search gives more power to the bad guysConcerns about the reach of ChatGPT and how easier it may get for bad actors to find sensitive...
5 cyber threats retailers are facing — and how they’re fighting back
5 cyber threats retailers are facing — and how they’re fighting backThere are many reasons retailers are juicy targets for hackers. They earn and handle tremendous...
DarkBit puts data from Israel’s Technion university on sale
DarkBit puts data from Israel’s Technion university on saleDarkBit, the group that claimed responsibility for a ransomware attack on Israel’s Technion university, is making good on...
Skyhawk adds ChatGPT functions to enhance cloud threat detection, incident discovery
Skyhawk adds ChatGPT functions to enhance cloud threat detection, incident discoveryCloud threat detection and response (CDR) vendor Skyhawk has announced the incorporation of ChatGPT functionality in...
Spera exits stealth to reveal identity-based threat hunting capabilities
Spera exits stealth to reveal identity-based threat hunting capabilitiesThe Israeli identity-based cybersecurity provider Spera is exiting stealth mode to reveal a namesake offering with identity security...