Challenges With AI: Artistry, Copyrights and Fake NewsThe world is buzzing about the new AI applications that are rapidly changing the landscape at home and work....
Day: March 26, 2023
Continuity Joins Dell Technologies ETC Program to Help Protect Customers’ Storage and Data Protection Systems
Continuity Joins Dell Technologies ETC Program to Help Protect Customers’ Storage and Data Protection SystemsThe ETC Program underscores Dell’s commitment to offer customers flexibility and choice...
Born In A Pandemic – Our Story | Blog by anecdotes
Born In A Pandemic – Our Story | Blog by anecdotesTrials and errors during a pandemic. Launching a successful start-up is always a challenge. Now you...
Privacy Compliance In 2023
Privacy Compliance In 2023anecdotes outlines the state privacy laws of 2023. Learn which are relevant to your organization, what they require and how to comply. The...
Vice Society claims attack on Puerto Rico Aqueduct and Sewer Authority
Vice Society claims attack on Puerto Rico Aqueduct and Sewer AuthorityPuerto Rico Aqueduct and Sewer Authority (PRASA) is investigating a cyber attack with the help of...
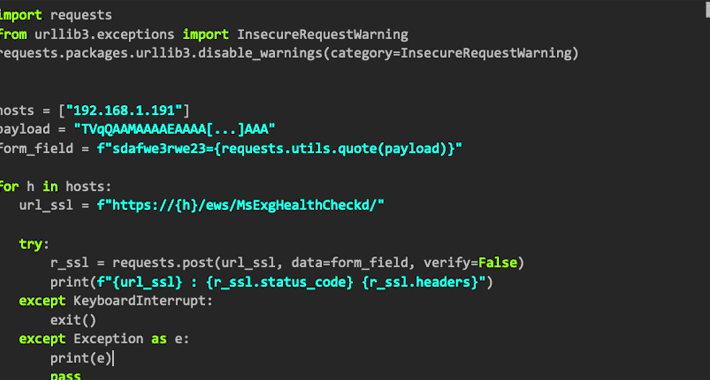
Microsoft shares guidance for investigating attacks exploiting CVE-2023-23397
Microsoft shares guidance for investigating attacks exploiting CVE-2023-23397Microsoft is warning of cyber attacks exploiting a recently patched Outlook vulnerability tracked as CVE-2023-23397 (CVSS score: 9.8). Microsoft...
Security Affairs newsletter Round 412 by Pierluigi Paganini – International edition
Security Affairs newsletter Round 412 by Pierluigi Paganini – International editionA new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from...
Weekly Update 340
Weekly Update 340I'm excited about coming to Prague. One more country to check off the list, apparently a beautiful city and perhaps what I'm most stoked...
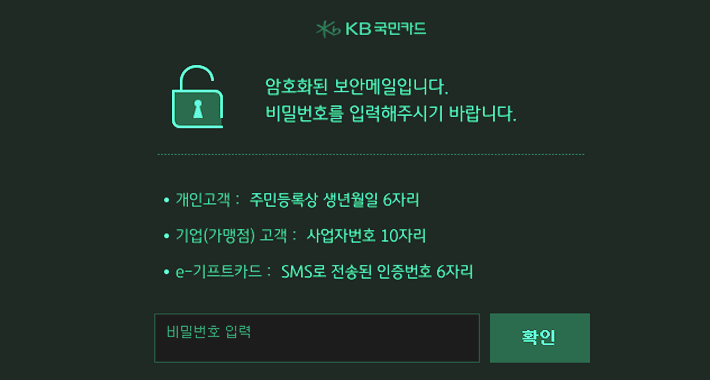
Emotet malware distributed as fake W-9 tax forms from the IRS
Emotet malware distributed as fake W-9 tax forms from the IRSA new Emotet phishing campaign is targeting U.S. taxpayers by impersonating W-9 tax forms allegedly sent...
Yes, it’s crazy to have TikTok on official phones. But it’s not good for any of us | John Naughton
Yes, it’s crazy to have TikTok on official phones. But it’s not good for any of us | John NaughtonFears for data security lie behind recent...
Hackers Steal Over $1.6 Million in Crypto from General Bytes Bitcoin ATMs Using Zero-Day Flaw
Hackers Steal Over $1.6 Million in Crypto from General Bytes Bitcoin ATMs Using Zero-Day FlawBitcoin ATM maker General Bytes disclosed that unidentified threat actors stole cryptocurrency...
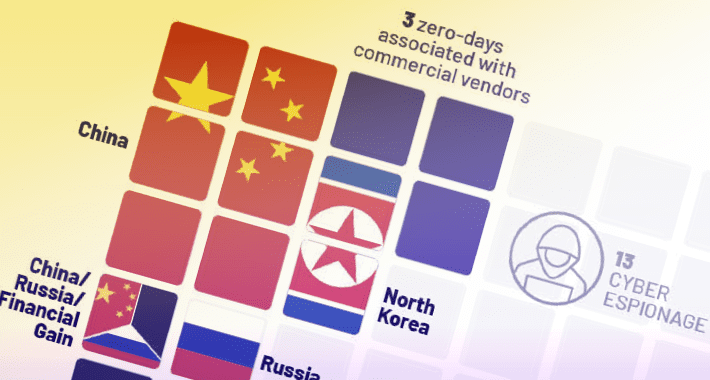
From Ransomware to Cyber Espionage: 55 Zero-Day Vulnerabilities Weaponized in 2022
From Ransomware to Cyber Espionage: 55 Zero-Day Vulnerabilities Weaponized in 2022As many as 55 zero-day vulnerabilities were exploited in the wild in 2022, with most of...
The Best Defense Against Cyber Threats for Lean Security Teams
The Best Defense Against Cyber Threats for Lean Security TeamsH0lyGh0st, Magecart, and a slew of state-sponsored hacker groups are diversifying their tactics and shifting their focus...
New ShellBot DDoS Malware Variants Targeting Poorly Managed Linux Servers
New ShellBot DDoS Malware Variants Targeting Poorly Managed Linux ServersPoorly managed Linux SSH servers are being targeted as part of a new campaign that deploys different...
New ‘Bad Magic’ Cyber Threat Disrupts Ukraine’s Key Sectors Amid War
New 'Bad Magic' Cyber Threat Disrupts Ukraine's Key Sectors Amid WarAmid the ongoing war between Russia and Ukraine, government, agriculture, and transportation organizations located in Donetsk, Lugansk, and...
BreachForums Administrator Baphomet Shuts Down Infamous Hacking Forum
BreachForums Administrator Baphomet Shuts Down Infamous Hacking ForumIn a sudden turn of events, Baphomet, the current administrator of BreachForums, said in an update on March 21,...
NAPLISTENER: New Malware in REF2924 Group’s Arsenal for Bypassing Detection
NAPLISTENER: New Malware in REF2924 Group's Arsenal for Bypassing DetectionThe threat group tracked as REF2924 has been observed deploying previously unseen malware in its attacks aimed at entities...
Rogue NuGet Packages Infect .NET Developers with Crypto-Stealing Malware
Rogue NuGet Packages Infect .NET Developers with Crypto-Stealing MalwareThe NuGet repository is the target of a new "sophisticated and highly-malicious attack" aiming to infect .NET developer systems with...
Preventing Insider Threats in Your Active Directory
Preventing Insider Threats in Your Active DirectoryActive Directory (AD) is a powerful authentication and directory service used by organizations worldwide. With this ubiquity and power comes...
ScarCruft’s Evolving Arsenal: Researchers Reveal New Malware Distribution Techniques
ScarCruft's Evolving Arsenal: Researchers Reveal New Malware Distribution TechniquesThe North Korean advanced persistent threat (APT) actor dubbed ScarCruft is using weaponized Microsoft Compiled HTML Help (CHM)...
CISA Alerts on Critical Security Vulnerabilities in Industrial Control Systems
CISA Alerts on Critical Security Vulnerabilities in Industrial Control SystemsThe U.S. Cybersecurity and Infrastructure Security Agency (CISA) has released eight Industrial Control Systems (ICS) advisories on Tuesday, warning...
German and South Korean Agencies Warn of Kimsuky’s Expanding Cyber Attack Tactics
German and South Korean Agencies Warn of Kimsuky's Expanding Cyber Attack TacticsGerman and South Korean government agencies have warned about cyber attacks mounted by a threat...
Operation Soft Cell: Chinese Hackers Breach Middle East Telecom Providers
Operation Soft Cell: Chinese Hackers Breach Middle East Telecom ProvidersTelecommunication providers in the Middle East are the subject of new cyber attacks that commenced in the...
2023 Cybersecurity Maturity Report Reveals Organizational Unpreparedness for Cyberattacks
2023 Cybersecurity Maturity Report Reveals Organizational Unpreparedness for CyberattacksIn 2022 alone, global cyberattacks increased by 38%, resulting in substantial business loss, including financial and reputational damage....
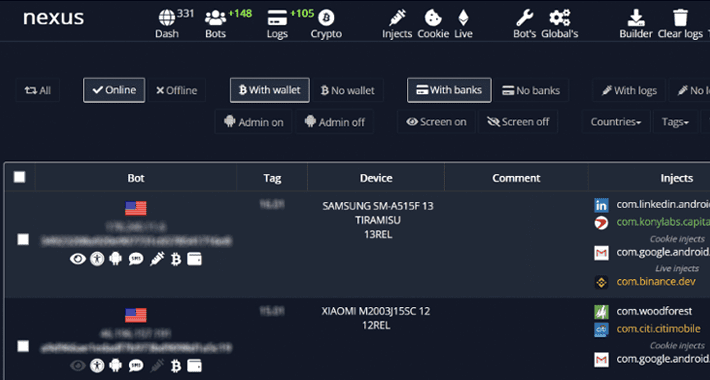
Nexus: A New Rising Android Banking Trojan Targeting 450 Financial Apps
Nexus: A New Rising Android Banking Trojan Targeting 450 Financial AppsAn emerging Android banking trojan dubbed Nexus has already been adopted by several threat actors to target 450...
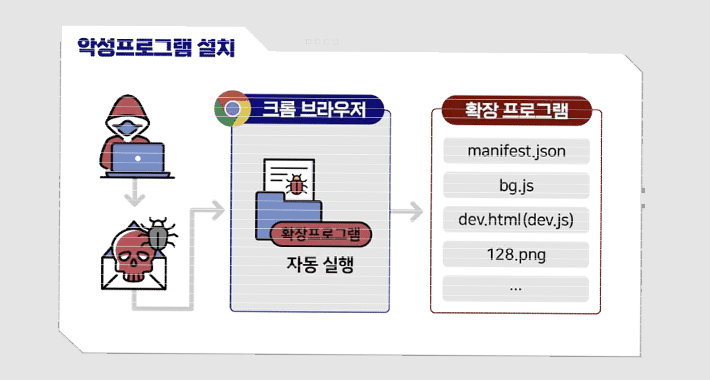
Fake ChatGPT Chrome Browser Extension Caught Hijacking Facebook Accounts
Fake ChatGPT Chrome Browser Extension Caught Hijacking Facebook AccountsGoogle has stepped in to remove a bogus Chrome browser extension from the official Web Store that masqueraded...
Critical WooCommerce Payments Plugin Flaw Patched for 500,000+ WordPress Sites
Critical WooCommerce Payments Plugin Flaw Patched for 500,000+ WordPress SitesPatches have been released for a critical security flaw impacting the WooCommerce Payments plugin for WordPress, which...
Researchers Uncover Chinese Nation State Hackers’ Deceptive Attack Strategies
Researchers Uncover Chinese Nation State Hackers' Deceptive Attack StrategiesA recent campaign undertaken by Earth Preta indicates that nation-state groups aligned with China are getting increasingly proficient at bypassing...
GitHub Swiftly Replaces Exposed RSA SSH Key to Protect Git Operations
GitHub Swiftly Replaces Exposed RSA SSH Key to Protect Git OperationsCloud-based repository hosting service GitHub said it took the step of replacing its RSA SSH host...
THN Webinar: Inside the High Risk of 3rd-Party SaaS Apps
THN Webinar: Inside the High Risk of 3rd-Party SaaS AppsAny app that can improve business operations is quickly added to the SaaS stack. However, employees don't...