New Version of Prometei Botnet Infects Over 10,000 Systems WorldwideAn updated version of a botnet malware called Prometei has infected more than 10,000 systems worldwide since November 2022....
Day: March 11, 2023
S3 Ep125: When security hardware has security holes [Audio + Text]
S3 Ep125: When security hardware has security holes [Audio + Text]Lastest episode - listen now! (Full transcript inside.)Read MoreNaked SecurityLastest episode - listen now! (Full transcript...
SHEIN shopping app goes rogue, grabs price and URL data from your clipboard
SHEIN shopping app goes rogue, grabs price and URL data from your clipboardIt's not exactly data theft, but it's worryingly close to "unintentional treachery" - apparently...
‘Extraordinary, Egregious’ Data Breach at House and Senate
‘Extraordinary, Egregious’ Data Breach at House and Senate Capitol Trouble: Senators, representatives and staffers suffer PII leak. Could it finally kickstart some action? The post ‘Extraordinary, Egregious’...
Vendor Tips for the SIG Questionnaire
Vendor Tips for the SIG Questionnaire Many companies understand the pain of constantly filling out extremely arduous customer- requested security questionnaires. Most of the time, the...
USENIX Security ’22 – Mohammadkazem Taram, Xida Ren, Ashish Venkat, Dean Tullsen – ‘SecSMT: Securing SMT Processors against Contention-Based Covert Channels’
USENIX Security ’22 – Mohammadkazem Taram, Xida Ren, Ashish Venkat, Dean Tullsen – ‘SecSMT: Securing SMT Processors against Contention-Based Covert Channels’Our thanks to USENIX for publishing...
Digital Trust Digest: This Week’s Must-Know News
Digital Trust Digest: This Week’s Must-Know NewsThe Digital Trust Digest is a curated overview of the week’s top cybersecurity news. Here's what happened the week of...
Sick of that Security Questionnaire? Automation is the Answer
Sick of that Security Questionnaire? Automation is the AnswerSecurity questionnaires (SQs) are not fun. They’re time-consuming, tedious work and sometimes, they’re the one thing standing between...
Camelot Launches Cybersecurity Service Augmented by ML
Camelot Launches Cybersecurity Service Augmented by ML Camelot this week launched a Secure360 cybersecurity platform that enables its cybersecurity team to leverage machine learning algorithms to...
Securing Software for Healthy, Energy-Efficient Smart Buildings
Securing Software for Healthy, Energy-Efficient Smart Buildings Jason Christman, Vice President and CPSO of Johnson Controls, Inc., talks about the value of shifting left in design...
SAST Tools Must Support Your Embedded Operating Systems, Toolchains & Compilers – Chose Wisely
SAST Tools Must Support Your Embedded Operating Systems, Toolchains & Compilers – Chose Wisely Embedded software development is very close to the development platform used. Whether...
Reducing Risks and Threats with Continuous SaaS Compliance
Reducing Risks and Threats with Continuous SaaS ComplianceCISOs and GRC officers are quickly recognizing the growing threats posed by misconfigured SaaS applications and integrations between SaaS...
Fighting Bots and Saving Costs in a Time of Shrinking Resources
Fighting Bots and Saving Costs in a Time of Shrinking ResourcesBeing a Chief Information Security Officer (CISO) is a challenging job, especially in today’s world where...
Refreshed from its holiday, Emotet has gone phishing
Refreshed from its holiday, Emotet has gone phishingNotorious botnet starts spamming again after a three-month pause Emotet is back. After another months-long lull since a spate...
US House reps, staff health data swiped in cyber-heist
US House reps, staff health data swiped in cyber-heistData for sale via dark web, Senate in line of fire, too Health data and other personal information...
AT&T blames marketing bods for exposing 9M accounts
AT&T blames marketing bods for exposing 9M accountsSays it was old and boring data, so that's OK, then ... AT&T has confirmed that miscreants had access...
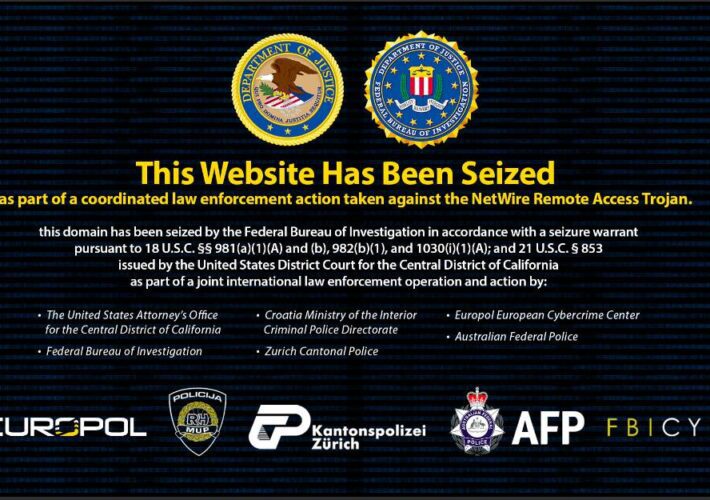
FBI and international cops catch a NetWire RAT
FBI and international cops catch a NetWire RATMalware-seekers were diverted to the Feds, severing a Croatian connection International law enforcement agencies have claimed another victory over...
Catholic clergy surveillance org ‘outs gay priests’
Catholic clergy surveillance org 'outs gay priests'Religious non-profit allegedly hoovered up location data from dating apps to ID clerics A Catholic clergy conformance organization has reportedly...
Acronis downplays intrusion after 12GB trove leaks online
Acronis downplays intrusion after 12GB trove leaks onlineCyber-thief said goal was to 'humiliate' data-protection biz The CISO of Acronis has downplayed what appeared to be an...
Electronics market shows US-China decoupling will hike inflation and slow growth
Electronics market shows US-China decoupling will hike inflation and slow growthSingapore's central bank has a gloomy vision of the future According to the Monetary Authority of...
What happens if you ‘cover up’ a ransomware infection? For Blackbaud, a $3m charge
What happens if you 'cover up' a ransomware infection? For Blackbaud, a $3m chargeFile under cost of doing business Blackbaud has agreed to pay $3 million...
Google euthanizes Chrome Cleanup Tool because it no longer has a purpose
Google euthanizes Chrome Cleanup Tool because it no longer has a purposeTimes have changed and unwanted software on Windows is a rarity (unless you count Windows...
Lazarus group infiltrated South Korean finance firm twice last year
Lazarus group infiltrated South Korean finance firm twice last yearLazarus group was spotted exploiting flaws in unnamed software to gain access to a South Korean finance...
GitHub begins 2FA rollout for code contributors
GitHub begins 2FA rollout for code contributorsGitHub has begun its official rollout of two-factor authentication (2FA) for developers who contribute code to the platform to enhance...
New Chinese regulatory body expected to streamline data governance rules
New Chinese regulatory body expected to streamline data governance rulesA new data regulation body that China is reportedly set to create is expected to clarify and...
Congressional health insurance service hit by data breach
Congressional health insurance service hit by data breachA health insurance marketplace that provides coverage for members of the US Congress and congressional staffers was found to...
Stolen credentials increasingly empower the cybercrime underground
Stolen credentials increasingly empower the cybercrime undergroundThe cybercrime underground has long functioned as an open market where sellers of products and services are paired with buyers...
Attacks on SonicWall appliances linked to Chinese campaign: Mandiant
Attacks on SonicWall appliances linked to Chinese campaign: MandiantA persistent malware targeting unpatched SonicWall Secure Mobile Access (SMA) appliances has been linked to a Chinese campaign...
Top cybersecurity M&A deals for 2023
Top cybersecurity M&A deals for 2023Uncertainty and instability marked the end of 2022 for many in the tech sector, a trend that bled into the beginning...
AT&T informs 9M customers about data breach
AT&T informs 9M customers about data breachAT&T is informing customers about a data breach at a vendor’s system that allowed threat actors to gain access to...