New Version of Prometei Botnet Infects Over 10,000 Systems WorldwideAn updated version of a botnet malware called Prometei has infected more than 10,000 systems worldwide since November 2022....
Day: March 11, 2023
SHEIN shopping app goes rogue, grabs price and URL data from your clipboard
SHEIN shopping app goes rogue, grabs price and URL data from your clipboardIt's not exactly data theft, but it's worryingly close to "unintentional treachery" - apparently...
S3 Ep125: When security hardware has security holes [Audio + Text]
S3 Ep125: When security hardware has security holes [Audio + Text]Lastest episode - listen now! (Full transcript inside.)Read MoreNaked SecurityLastest episode - listen now! (Full transcript...
‘Extraordinary, Egregious’ Data Breach at House and Senate
‘Extraordinary, Egregious’ Data Breach at House and Senate Capitol Trouble: Senators, representatives and staffers suffer PII leak. Could it finally kickstart some action? The post ‘Extraordinary, Egregious’...
Vendor Tips for the SIG Questionnaire
Vendor Tips for the SIG Questionnaire Many companies understand the pain of constantly filling out extremely arduous customer- requested security questionnaires. Most of the time, the...
USENIX Security ’22 – Mohammadkazem Taram, Xida Ren, Ashish Venkat, Dean Tullsen – ‘SecSMT: Securing SMT Processors against Contention-Based Covert Channels’
USENIX Security ’22 – Mohammadkazem Taram, Xida Ren, Ashish Venkat, Dean Tullsen – ‘SecSMT: Securing SMT Processors against Contention-Based Covert Channels’Our thanks to USENIX for publishing...
Digital Trust Digest: This Week’s Must-Know News
Digital Trust Digest: This Week’s Must-Know NewsThe Digital Trust Digest is a curated overview of the week’s top cybersecurity news. Here's what happened the week of...
Sick of that Security Questionnaire? Automation is the Answer
Sick of that Security Questionnaire? Automation is the AnswerSecurity questionnaires (SQs) are not fun. They’re time-consuming, tedious work and sometimes, they’re the one thing standing between...
Camelot Launches Cybersecurity Service Augmented by ML
Camelot Launches Cybersecurity Service Augmented by ML Camelot this week launched a Secure360 cybersecurity platform that enables its cybersecurity team to leverage machine learning algorithms to...
Securing Software for Healthy, Energy-Efficient Smart Buildings
Securing Software for Healthy, Energy-Efficient Smart Buildings Jason Christman, Vice President and CPSO of Johnson Controls, Inc., talks about the value of shifting left in design...
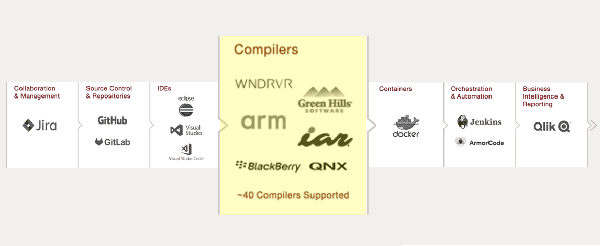
SAST Tools Must Support Your Embedded Operating Systems, Toolchains & Compilers – Chose Wisely
SAST Tools Must Support Your Embedded Operating Systems, Toolchains & Compilers – Chose Wisely Embedded software development is very close to the development platform used. Whether...
Reducing Risks and Threats with Continuous SaaS Compliance
Reducing Risks and Threats with Continuous SaaS ComplianceCISOs and GRC officers are quickly recognizing the growing threats posed by misconfigured SaaS applications and integrations between SaaS...
Fighting Bots and Saving Costs in a Time of Shrinking Resources
Fighting Bots and Saving Costs in a Time of Shrinking ResourcesBeing a Chief Information Security Officer (CISO) is a challenging job, especially in today’s world where...
Lazarus group infiltrated South Korean finance firm twice last year
Lazarus group infiltrated South Korean finance firm twice last yearLazarus group was spotted exploiting flaws in unnamed software to gain access to a South Korean finance...
GitHub begins 2FA rollout for code contributors
GitHub begins 2FA rollout for code contributorsGitHub has begun its official rollout of two-factor authentication (2FA) for developers who contribute code to the platform to enhance...
New Chinese regulatory body expected to streamline data governance rules
New Chinese regulatory body expected to streamline data governance rulesA new data regulation body that China is reportedly set to create is expected to clarify and...
Congressional health insurance service hit by data breach
Congressional health insurance service hit by data breachA health insurance marketplace that provides coverage for members of the US Congress and congressional staffers was found to...
Stolen credentials increasingly empower the cybercrime underground
Stolen credentials increasingly empower the cybercrime undergroundThe cybercrime underground has long functioned as an open market where sellers of products and services are paired with buyers...
Attacks on SonicWall appliances linked to Chinese campaign: Mandiant
Attacks on SonicWall appliances linked to Chinese campaign: MandiantA persistent malware targeting unpatched SonicWall Secure Mobile Access (SMA) appliances has been linked to a Chinese campaign...
Top cybersecurity M&A deals for 2023
Top cybersecurity M&A deals for 2023Uncertainty and instability marked the end of 2022 for many in the tech sector, a trend that bled into the beginning...
AT&T informs 9M customers about data breach
AT&T informs 9M customers about data breachAT&T is informing customers about a data breach at a vendor’s system that allowed threat actors to gain access to...
New variant of the IceFire ransomware targets Linux enterprise systems
New variant of the IceFire ransomware targets Linux enterprise systemsA novel Linux version of the IceFire ransomware that exploits a vulnerability in IBM's Aspera Faspex file-sharing software...
BrandPost: Cybersecurity Automation: Leveling the Playing Field
BrandPost: Cybersecurity Automation: Leveling the Playing FieldMany things challenge how we practice cybersecurity these days. Digital transformation has brought significant adoption of new technology and business...
Common WhatsApp scams and how to avoid them
Common WhatsApp scams and how to avoid themHere's a roundup of some of the most common tricks that fraudsters use to dupe their victims on WhatsApp...
APT hackers set a honeytrap to ensnare victims – Week in security with Tony Anscombe
APT hackers set a honeytrap to ensnare victims – Week in security with Tony AnscombeA request to move an online conversation to a supposedly more secure...
Tehran Targets Female Activists in Espionage Campaign
Tehran Targets Female Activists in Espionage CampaignCovert crackdown on Mahsa Amini protests continuesRead MoreCovert crackdown on Mahsa Amini protests continues
Understanding the Shared Responsibility Model, Critical Step to Ensure Cloud Security
Understanding the Shared Responsibility Model, Critical Step to Ensure Cloud SecurityDuring the Cloud & Cyber Security Expo, cloud security experts attributed the security shortcomings of cloud...
TikTok Initiates Project Clover Amid European Data Security Concerns
TikTok Initiates Project Clover Amid European Data Security ConcernsSocial media giant TikTok has retaliated to European data security concerns with Project Clover and the announcement of...
Acer Confirms Unauthorized Access But Says No Consumer Data Stolen
Acer Confirms Unauthorized Access But Says No Consumer Data StolenKernelware threat actor claimed responsibility for the hack on a dark web forumRead MoreKernelware threat actor claimed...
8220 Gang Behind ScrubCrypt Attack Targeting Oracle Weblogic Server
8220 Gang Behind ScrubCrypt Attack Targeting Oracle Weblogic ServerScrubCrypt malware obfuscates and encrypts applications to evade antivirus detectionRead MoreScrubCrypt malware obfuscates and encrypts applications to evade...