US RESTRICT Act Gains Supports, Empowers Biden to Ban Foreign TechThe White House and a bipartisan group of 12 senators have endorsed the legislationRead MoreThe White...
Day: March 8, 2023
Cisco Event Response: March 2023 Semiannual Cisco IOS XR Software Security Advisory Bundled Publication
Cisco Event Response: March 2023 Semiannual Cisco IOS XR Software Security Advisory Bundled PublicationPost ContentRead MoreCisco Event Responses
VMware NSX Manager bugs actively exploited in the wild since December
VMware NSX Manager bugs actively exploited in the wild since DecemberSecurity researchers warn of hacking attempts in the wild exploiting critical vulnerabilities in VMware NSX Manager....
China-linked APT Sharp Panda targets government entities in Southeast Asia
China-linked APT Sharp Panda targets government entities in Southeast AsiaChina-linked APT group Sharp Panda targets high-profile government entities in Southeast Asia with the Soul modular framework....
CISA adds three new bugs to Known Exploited Vulnerabilities Catalog
CISA adds three new bugs to Known Exploited Vulnerabilities CatalogUS CISA added actively exploited flaws in Teclib GLPI, Apache Spark, and Zoho ManageEngine ADSelfService Plus to...
North Korea-linked Lazarus APT used a 0-day in a recent attack
North Korea-linked Lazarus APT used a 0-day in a recent attackNorth Korea-linked Lazarus APT group exploits a zero-day vulnerability in attacks aimed at a South Korean financial entity. ASEC...
PIM vs PAM vs IAM: What’s The Difference?
PIM vs PAM vs IAM: What’s The Difference?Identity management has become an essential aspect of cybersecurity as businesses struggle to protect their sensitive data from cyber...
Acer Discloses Data Breach: 160GB of Sensitive Information for Sale
Acer Discloses Data Breach: 160GB of Sensitive Information for SaleA threat actor claimed to have hacked Taiwanese multinational hardware and electronics business Acer, prompting the company...
A New Emotet Campaign Is Ongoing After a Three-month Break
A New Emotet Campaign Is Ongoing After a Three-month BreakA new Emotet campaign started infecting devices all over the world on Tuesday, 7 March 2023. After...
New Info Stealer SYS01 Targets Key Government Infrastructure
New Info Stealer SYS01 Targets Key Government InfrastructureCybersecurity researchers uncovered a new, highly-advanced information stealer, dubbed SYS01 stealer, that has been deployed in attacks on critical...
Making the most of your time at the RSA 2023 conference
Making the most of your time at the RSA 2023 conferenceBen Rothke, CISSP, CISM, CISA, is a Senior Information Security Manager at Tapad Going to RSA...
Has Adoption of ‘Connected Devices’ Outpaced Security?
Has Adoption of ‘Connected Devices’ Outpaced Security?By Scott Register, Vice President, Security Solutions, Keysight Technologies We’ve all seen the rush to deploy the new wave of...
How to Stay GDPR Compliant While Sending Cold Emails
How to Stay GDPR Compliant While Sending Cold EmailsUnderstand the limits of data consent when sending cold emails By Tim Green, Cybersecurity Specialist Cold emailing is...
BlackLotus Malware Hijacks Windows Secure Boot Process
BlackLotus Malware Hijacks Windows Secure Boot ProcessResearchers have discovered malware that “can hijack a computer’s boot process even when Secure Boot and other advanced protections are...
Pen Testers using Vulnerability Scanners – Closing the Gap
Pen Testers using Vulnerability Scanners – Closing the GapBoth penetration testing and vulnerability scanning are essential to upholding and maintaining a strong security posture. Here are...
DuckDuckGo launches AI-powered search query answering tool
DuckDuckGo launches AI-powered search query answering toolPrivacy-focused search engine DuckDuckGo has launched the first beta version of DuckAssist, an AI-assisted feature that writes accurate summaries to...
Ransomware gang posts video of data stolen from Minneapolis schools
Ransomware gang posts video of data stolen from Minneapolis schoolsThe Medusa ransomware gang is demanding a $1,000,000 ransom from the Minneapolis Public Schools (MPS) district to...
Celebrating International Women’s Day: Creating awareness & driving change
Celebrating International Women’s Day: Creating awareness & driving changeUlrica is a VP of Product & Strategy at Indeni with over 30 years experience developing software in...
GUEST ESSAY: Five stages to attain API security — and mitigate attack surface exposures
GUEST ESSAY: Five stages to attain API security — and mitigate attack surface exposuresAPIs (Application Programming Interfaces) play a critical role in digital transformation by enabling...
Darktrace warns of rise in AI-enhanced scams since ChatGPT release
Darktrace warns of rise in AI-enhanced scams since ChatGPT releaseCybersecurity firm notes emergence of sophisticated email scams featuring improved linguistic complexity The cybersecurity firm Darktrace has...
Co-Working for the Ransomware Age: How Hive Thrived
Co-Working for the Ransomware Age: How Hive ThrivedMixing Conti's Leftovers and Small Teams Helped Hive Earn Millions, Researcher SaysKey to the business success of top ransomware...
Staying Ahead of Financial Crimes in the Age of Real-Time Payments
Staying Ahead of Financial Crimes in the Age of Real-Time PaymentsInsights for Fraud Prevention and AML ProfessionalsWatch this interview to learn how the faster payments space...
Nuevo malware para cajeros automáticos FiXS dirigido a bancos mexicanos
Nuevo malware para cajeros automáticos FiXS dirigido a bancos mexicanosSe ha observado una nueva variedad de malware para cajeros automáticos denominada FiXS dirigida a bancos mexicanos...
Shein’s Android App Caught Transmitting Clipboard Data to Remote Servers
Shein's Android App Caught Transmitting Clipboard Data to Remote ServersAn older version of Shein's Android application suffered from a bug that periodically captured and transmitted clipboard contents to...
OWASP API Security Top 10: Upcoming Changes You Need To Know About
OWASP API Security Top 10: Upcoming Changes You Need To Know AboutCheck out these changes coming to the OWASP API Security Top 10 list! The post...
BlackMamba: Using AI to Generate Polymorphic Malware
BlackMamba: Using AI to Generate Polymorphic Malware New Threats Emerging The introduction of ChatGPT last year marked the first time neural network code synthesis was made...
White House cyber strategy: A love/hate story
White House cyber strategy: A love/hate story The post White House cyber strategy: A love/hate story appeared first on Security Boulevard. Read MoreSecurity BoulevardThe post White...
Do You Want to Know a Secret? Just Take a Look Inside Top Finance Apps
Do You Want to Know a Secret? Just Take a Look Inside Top Finance Apps Financial apps have access to valuable and sensitive personal data, so you...
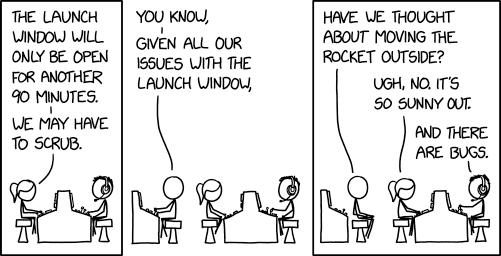
Randall Munroe’s XKCD ‘Launch Window’
Randall Munroe’s XKCD ‘Launch Window’ via the comic artistry and dry wit of Randall Munroe, resident at XKCD! Permalink The post Randall Munroe’s XKCD ‘Launch Window’...
What the LastPass Hack Says About Modern Cybersecurity
What the LastPass Hack Says About Modern CybersecurityOnline password managers are meant to help users keep track of the long and complex... The post What the...