The State of the Security TeamThe success of the cybersecurity team requires support across the entire organization. LogRhythm’s 2022 State of the Security Team global research...
Day: March 6, 2023
5 Tactical Tips For Security Teams Using AWS
5 Tactical Tips For Security Teams Using AWS Security teams face new and unique challenges as they move their workloads to AWS. Legacy SIEM solutions were...
Find More Secrets with Nosey Parker v.0.12.0
Find More Secrets with Nosey Parker v.0.12.0On March 2, 2023, we issued some updates to our secrets sniffing tool, Nosey Parker, which has been available as...
6 Ways to Vet Your Next ASM Vendor
6 Ways to Vet Your Next ASM Vendor Attack surface management (ASM) is a critical security function, and the market for ASM solutions is growing rapidly....
USENIX Security ’22 – Shravan Srinivasan, Alexander Chepurnoy, Charalampos Papamanthou, Alin Tomescu, Yupeng Zhang – ‘Hyperproofs: Aggregating and Maintaining Proofs in Vector Commitments’
USENIX Security ’22 – Shravan Srinivasan, Alexander Chepurnoy, Charalampos Papamanthou, Alin Tomescu, Yupeng Zhang – ‘Hyperproofs: Aggregating and Maintaining Proofs in Vector Commitments’Our thanks to USENIX...
ZTNA and the Death of the Network Perimeter
ZTNA and the Death of the Network PerimeterTony Bradley Editor-in-Chief at TechSpective Zero trust network access (ZTNA) is becoming increasingly relevant as the concept...
Darktrace launches AI-driven vulnerability detection, alert system Newsroom
Darktrace launches AI-driven vulnerability detection, alert system NewsroomAI-focused cybersecurity vendor Darktrace has announced the release of Newsroom, a new detection and warning system for critical vulnerabilities...
Tracking device technology: A double-edged sword for CISOs
Tracking device technology: A double-edged sword for CISOsThe transportation industry has doubled down in the area of fleet tracking in recent years, which has come with...
Open letter demands OWASP overhaul, warns of mass project exodus
Open letter demands OWASP overhaul, warns of mass project exodusFor more than two decades, the Open Worldwide Application Security Project (OWASP) has provided free and open...
FTC Proposes $7.8m Fine for BetterHelp
FTC Proposes $7.8m Fine for BetterHelpOnline counseling service shared health dataRead MoreOnline counseling service shared health data
UK Government Plans Skills Boost for Public Sector Fraud Fight
UK Government Plans Skills Boost for Public Sector Fraud FightFocus will be on enhancing prevention and identification skillsRead MoreFocus will be on enhancing prevention and identification...
City of Oakland Faces Major Data Leak
City of Oakland Faces Major Data LeakInformation was stolen during recent ransomware attackRead MoreInformation was stolen during recent ransomware attack
DoppelPaymer Ransomware Gang Members Busted in Germany, Ukraine
DoppelPaymer Ransomware Gang Members Busted in Germany, UkrainePolice also seized electronic equipment and are currently performing forensic examinationsRead MorePolice also seized electronic equipment and are currently...
EPA Calls For Cybersecurity Improvements in Public Water Systems
EPA Calls For Cybersecurity Improvements in Public Water SystemsThe memorandum highlights the need for states to include cybersecurity in periodic auditsRead MoreThe memorandum highlights the need...
Almost Half of Industrial Sector Computers Affected By Malware in 2022
Almost Half of Industrial Sector Computers Affected By Malware in 2022Kaspersky said the figures represented a 1.5 increase compared with the second half of 2021Read MoreKaspersky...
Hatch Bank data breach caused by the exploitation of the GoAnywhere MFT zero-day
Hatch Bank data breach caused by the exploitation of the GoAnywhere MFT zero-dayFintech platform Hatch Bank disclosed a data breach, hackers exploited a recently discovered zero-day...
Colour-Blind, a fully featured info stealer and RAT in PyPI
Colour-Blind, a fully featured info stealer and RAT in PyPIExperts discovered a fully featured information stealer, tracked as ‘Colour-Blind’ in the Python Package Index (PyPI). Researchers...
US government orders States to conduct cyber security audits of public water systems
US government orders States to conduct cyber security audits of public water systemsThe US government urges cyber security audits of public water systems, highlighting the importance...
European police dismantled the DoppelPaymer ransomware gang
European police dismantled the DoppelPaymer ransomware gangGerman police announced to have dismantled an international cybercrime gang behind the DoppelPaymer ransomware operation. Europol has announced that an...
BidenCash Leaks Database with Over 2 Million Stolen Credit Cards
BidenCash Leaks Database with Over 2 Million Stolen Credit CardsA database containing over 2 million debit and credit cards was released for free by carding marketplace...
What Is Domain Generation Algorithm? Definition and Role in Malware Attacks
What Is Domain Generation Algorithm? Definition and Role in Malware AttacksDomain generation algorithms (DGA) are software that creates large numbers of domain names. This helps hackers...
BetterHelp Accused of Sharing Mental Health Data with Advertisers
BetterHelp Accused of Sharing Mental Health Data with AdvertisersThe Federal Trade Commission (FTC) accused BetterHelp online counseling service of sharing customers’ mental health data with advertisers....
Play Ransomware Starts Leaking Oakland City Data
Play Ransomware Starts Leaking Oakland City DataThe Play ransomware group has begun leaking data stolen in a recent cyberattack from the City of Oakland, California. The initial...
Europe Envies America’s Cybersecurity Industry. What Can We Learn from It?
Europe Envies America’s Cybersecurity Industry. What Can We Learn from It?Europe’s cyber industry has huge potential. Copying what’s worked in the US is a route to...
Expanding Macroeconomic Pressure And Attack Surface Will Drive Security Automation In 2023
Expanding Macroeconomic Pressure And Attack Surface Will Drive Security Automation In 2023By Leonid Belkind, CTO and Co-Founder, Torq Security automation continued to have significant, positive impact...
MQsTTang Backdoor Detection: New Custom Malware by Mustang Panda APT Actively Used in the Latest Campaign Against Government Entities
MQsTTang Backdoor Detection: New Custom Malware by Mustang Panda APT Actively Used in the Latest Campaign Against Government Entities New day, new malicious threat challenging...
Study reveals companies are wasting millions on unused Kubernetes resources
Study reveals companies are wasting millions on unused Kubernetes resourcesGraham Cluley Security News is sponsored this week by the folks at Sysdig. Thanks to the great...
New National Cybersecurity Strategy
New National Cybersecurity StrategyLast week the Biden Administration released a new National Cybersecurity Strategy (summary here). There is lots of good commentary out there. It’s basically...
Core DoppelPaymer ransomware gang members targeted in Europol operation
Core DoppelPaymer ransomware gang members targeted in Europol operationEuropol has announced that law enforcement in Germany and Ukraine targeted two individuals believed to be core members...
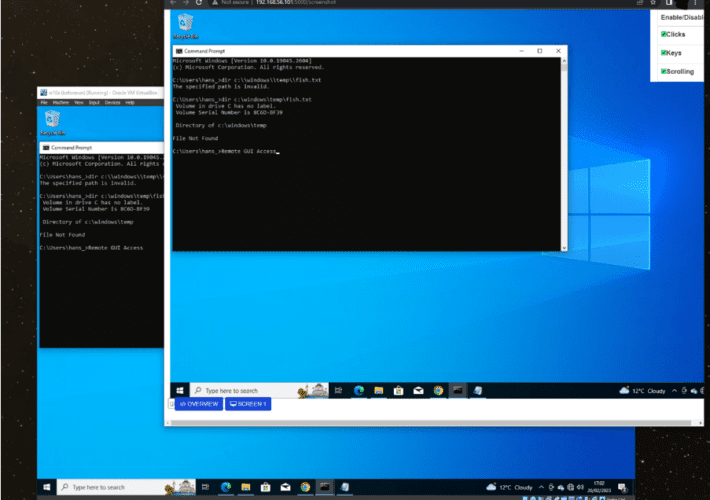
DrayTek VPN routers hacked with new malware to steal data, evade detection
DrayTek VPN routers hacked with new malware to steal data, evade detectionAn ongoing hacking campaign called 'Hiatus' targets DrayTek Vigor router models 2960 and 3900 to...