Source: securityboulevard.com – Author: wlrmblog
Welcome to the 7th post in our weekly series on the new 2023 OWASP API Security Top-10 list, with a particular focus on security practitioners. This post will focus on API6:2023 Unrestricted Access to Sensitive Business Flows.
In this series we are taking an in-depth look at each category – the details, the impact and what you can do about it. To see previous posts you might have missed, click here.
TL;DR
Unrestricted Access to Sensitive Business Flows involves exploitation of the business model behind the application, such as buying all the product, reserving all the seats, or artificially initiating a price reduction. In these vulnerabilities, the API facilitates an unexpected and unwanted business flow. Most commonly, exploitation of this class of vulnerabilities might be called API Abuse or be associated with malicious bot traffic.
The Details
APIs exist for a reason. They’re an interface to an application, which is part of some kind of workflow. Usually those workflows have a purpose, and often it’s a business purpose. When an API is designed in a way that supports the business function, but there’s no restriction on usage, it can be subject to this type of vulnerability. This situation is distinct from some of the other OWASP Top 10 in that it’s less of a vulnerability in code and more of a missing restriction on usage. This distinction also makes this type of vulnerability more difficult to detect and prevent.
Let’s say you have an ecommerce website and you’re selling shoes. The website is driven by a set of APIs. When a visitor views a pair of shoes, the web application pulls an image, price, and description of the item via the API to display for the visitor. Without any restrictions in place, a malicious attacker could access the API directly and pull all of the pricing information, i.e., price scraping.
Another example might be an API that provides information about a user in an application. That user information might be publicly available within the application so that one user can view the details of another user, one at a time. The API, without restrictions, would allow anyone to effectively scrape all the user data available programmatically. It’s worth mentioning an attack that affected Duolingo as an example here.
These are examples where the API is performing as it was designed, but the business flow itself assumes some restrictions that aren’t enforced programmatically.
What’s the Impact?
When we talk about this type of API abuse, there are a number of attacker “use cases” that exist.
- Fake Accounts: Attackers might use an unrestricted account creation API to generate hundreds or thousands of fake accounts, allowing them to overwhelm an application or engage in programmatic exploitation of their status as ‘authorized’ users.
- Spamming: An API to add user-generated content, such as comments or reviews can allow an attacker to add malicious links or even simply advertisements into an application at massive scale.
- Scalping: An API that allows direct purchasing without browsing through a web interface can allow an attacker to jump ahead of desired customers and purchase an inventory of items to resell at a higher price.
- Content Scraping: Of course, APIs that provide data, whether about products, prices, or users, can be used to collect that data in bulk for malicious purposes.
What Can You Do About It?
In order to effectively mitigate these kinds of attacks, you need to understand the business flows you’re protecting. This makes approaches based on automated tools tricky. There are some blunt-force approaches, such as blocking all traffic from TOR exit nodes or from specific geographies, which can cut down on some of the more obvious malicious bot activity. If you can filter based on user-agents, that can help eliminate traffic from bad user agents.
Good API governance can help as well. Ensuring that the deployed endpoints match the API specification (and making sure you have API specifications) can help to eliminate risks from unused endpoints or endpoints that should have been removed. Commercial tools can be employed to perform more sophisticated malicious bot and API abuse prevention as well.
How Wallarm Can Help
The Wallarm platform provides multiple protections to help combat unrestricted resource consumption. Blocking based on IPs and user-agents is available, but so is more sophisticated rate limiting by user-agent. Wallarm’s API Discovery feature allows users to compare what’s in production with API specifications to improve API governance and reduce the risk of shadow and orphan APIs. Finally, Wallarm offers AI-based API Abuse Protection that uses machine-learning to identify malicious bots based on criteria like suspicious behavior, query abuse, and business logic.
Learn More
Come back next week as we dig into the details of another category of the new 2023 OWASP Top-10 API Security Risks list – or click here to see previous posts you might have missed.
In the meantime, here are some other resources which might help on your journey to end-to-end API security:
- Solution Brief: OWASP API Security Top-10 2023 Reference Guide (PDF)
- Blog Post: OWASP API Security Top-10 Risks for 2023 Released
- Blog Post: OWASP API Security Top-10 for 2023 Risk Ratings
- On-Demand Webinar: A Practitioner’s Guide to the New 2023 OWASP API Security Update
- On-Demand Webinar: A CISOs Guide to the New 2023 OWASP API Security Update
- Research Report: 2022 Year-End API ThreatStats™ Report (blog and linked full report)
Protect Your APIs from OWASP API Security Top-10 Threats
Wallarm End-to-End API Security solution provides comprehensive protection against the OWASP API Security Top-10 threats. And in 2023, we’ve made it even easier for you!
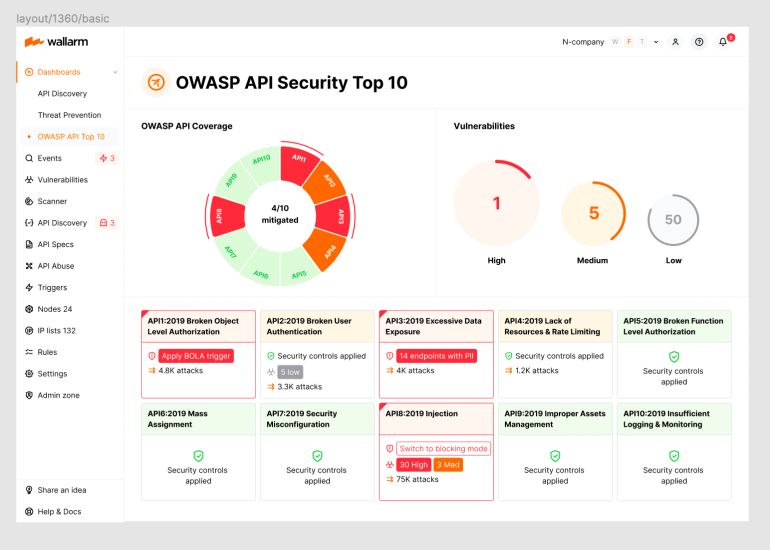
The Wallarm 2023 OWASP API Security Top-10 Dashboard provides you with complete visibility into the security state of your APIs, easy identification of your most critical security risks, and ability to immediately apply protective measures.

If you are interested in learning more about how we can help you protect your APIs, please schedule a demo with one of our security experts today!
The post 2023 OWASP Top-10 Series: API6:2023 Unrestricted Access to Sensitive Business Flows appeared first on Wallarm.
*** This is a Security Bloggers Network syndicated blog from Wallarm authored by wlrmblog. Read the original post at: https://lab.wallarm.com/api62023-unrestricted-access-to-sensitive-business-flows/
Original Post URL: https://securityboulevard.com/2023/09/2023-owasp-top-10-series-api62023-unrestricted-access-to-sensitive-business-flows/
Category & Tags: Application Security,Security Bloggers Network,owasp,OWASP APIsec Top-10 2023 Series,OWASP Top 10 – Application Security,Security Bloggers Network,owasp,OWASP APIsec Top-10 2023 Series,OWASP Top 10
Views: 1