Building a modern API security strategy — API components Part three of the five-part series, Building a modern API security strategy. The post Building a modern...
Year: 2022
Traditional Security Won’t Cut It for Secure Cloud-Native Applications: Here’s Why
Traditional Security Won’t Cut It for Secure Cloud-Native Applications: Here’s WhyTraditional Security Won’t Cut It for Secure Cloud-Native Applications: Here’s Why brooke.crothers Wed, 08/10/2022 - 16:43...
Is Your AppSec Program Developer-Centric?
Is Your AppSec Program Developer-Centric? You need an AppSec program. Software supports your business, and you need to know that attackers can’t kick that ground out...
Twilio Breach: Three Steps to Protect Your Company
Twilio Breach: Three Steps to Protect Your CompanyTwilio published an incident report on August 4, 2022 about an attack that led to employee and customer account...
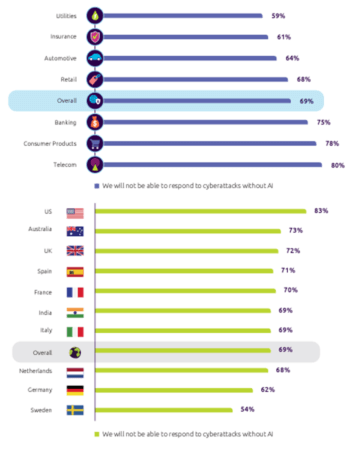
Convergence and adoption of AI and ML countering the cyber threat
Convergence and adoption of AI and ML countering the cyber threatDuring the last few years, we have witnessed an increase in advanced cyber attacks. Cybercriminals utilize...
NSA, DOE, MITRE and Industry Experts Share Advice on Building Cyber Resilience
NSA, DOE, MITRE and Industry Experts Share Advice on Building Cyber ResilienceThe post NSA, DOE, MITRE and Industry Experts Share Advice on Building Cyber Resilience appeared...
Digital milestones for elementary schoolers
Digital milestones for elementary schoolers The internet is a vital part of kids’ lives today. They see grown-ups and older kids going online with all kinds...
Why is Cybersecurity Essential for Small Businesses?
Why is Cybersecurity Essential for Small Businesses?Cybersecurity is a common term for every business but how seriously is it taken? Small businesses often have no budget...
APIC/EPIC! Intel chips leak secrets even the kernel shouldn’t see…
APIC/EPIC! Intel chips leak secrets even the kernel shouldn’t see…If you've ever written code that left stuff lying around in memory when you didn't need it...
Former Twitter Employee Found Guilty of Spying for Saudi Arabia
Former Twitter Employee Found Guilty of Spying for Saudi ArabiaA former Twitter employee has been pronounced guilty for his role in digging up private information pertaining...
Experts Uncover Details on Maui Ransomware Attack by North Korean Hackers
Experts Uncover Details on Maui Ransomware Attack by North Korean HackersThe first ever incident possibly involving the ransomware family known as Maui occurred on April 15,...
Decentralized IPFS networks forming the ‘hotbed of phishing’
Decentralized IPFS networks forming the 'hotbed of phishing'P2P file system makes it more difficult to detect and take down malicious content Threat groups are increasingly turning...
Feds put $10m bounty on Putin pal accused of bankrolling US election troll farm
Feds put $10m bounty on Putin pal accused of bankrolling US election troll farmJust in time for the midterms The Feds have put up a $10...
This is what to expect when a managed service provider gets popped
This is what to expect when a managed service provider gets poppedMSP should just stand for My Server's Pwned! A Russian-language miscreant claims to have hacked...
Hybrid Identity Protection with Denis Ontiveros Merlo
Hybrid Identity Protection with Denis Ontiveros MerloSecurity architectures depend on identity—the “new security boundary.” Yet despite investment in identity and attempts to drive a sustainable identity...
Debunking IAST myths
Debunking IAST myths If you have followed Contrast's progress over the years, you will recognize us as a leading provider of Interactive Application Security Testing (IAST)/...
Microsoft Patch Tuesday, August 2022 Edition
Microsoft Patch Tuesday, August 2022 EditionMicrosoft today released updates to fix a record 141 security vulnerabilities in its Windows operating systems and related software. Once again,...
U.S. Sanctions Virtual Currency Mixer Tornado Cash for Alleged Use in Laundering
U.S. Sanctions Virtual Currency Mixer Tornado Cash for Alleged Use in LaunderingThe U.S. Treasury Department on Monday placed sanctions against crypto mixing service Tornado Cash, citing...
The Truth About False Positives in Security
The Truth About False Positives in SecurityTL;DR: As weird as it might sound, seeing a few false positives reported by a security scanner is probably a...
Twilio Suffers Data Breach After Employees Fall Victim to SMS Phishing Attack
Twilio Suffers Data Breach After Employees Fall Victim to SMS Phishing AttackCustomer engagement platform Twilio on Monday disclosed that a "sophisticated" threat actor gained "unauthorized access"...
Hackers Opting New Attack Methods After Microsoft Blocked Macros by Default
Hackers Opting New Attack Methods After Microsoft Blocked Macros by DefaultContenido de la entradaLeer másProofpoint News Feed
Attacks using Office macros decline in wake of Microsoft action
Attacks using Office macros decline in wake of Microsoft actionContenido de la entradaLeer másProofpoint News Feed
Proofpoint: 97% of top universities in the US, UK and Australia putting students, staff, and stakeholders at risk of being impersonated by cybercriminals
Proofpoint: 97% of top universities in the US, UK and Australia putting students, staff, and stakeholders at risk of being impersonated by cybercriminalsContenido de la entradaLeer...
Ransomware: Hive, LockBit & BlackCat pounce on this one firm’s network…
Ransomware: Hive, LockBit & BlackCat pounce on this one firm’s network…EXECUTIVE SUMMARY: Three prominent ransomware gangs -Hive, Lockbit and BlackCat- have consecutively attacked a single network...
CEO Talk: With 2022’s Tech for Humanity Award winner
CEO Talk: With 2022’s Tech for Humanity Award winnerAri Gargir is the Founder and CEO of RedC Biotech, developing an industrial process for production of life...
GUEST ESSAY: How to secure ‘Digital Twins’ to optimize asset use, while reducing exposures
GUEST ESSAY: How to secure ‘Digital Twins’ to optimize asset use, while reducing exposuresOur technological world is advancing at dizzying speeds. Related: The coming of a...
SOC 2 compliance checklist and best practices (for an audit) 2022
SOC 2 compliance checklist and best practices (for an audit) 2022EXECUTIVE SUMMARY: Numerous types of SOC reports for service organizations are out there. However, one of...
CEO Talk: One of the fastest-growing startups in SaaS
CEO Talk: One of the fastest-growing startups in SaaSLior is the CEO and Co-Founder of Grip Security, one of the fastest-growing SaaS security startups today. He...
New trends! Check Point Software’s Mid-Year Security Report
New trends! Check Point Software’s Mid-Year Security ReportEXECUTIVE SUMMARY: According to a recent report issued by Check Point Software, cyber attacks around the globe have increased...
Timely phishing prevention strategies for today’s stealthiest attacks
Timely phishing prevention strategies for today’s stealthiest attacksPatrik Honegger has worked in the IT sector since the 1990’s and has specialized in the IT security field...