Threat actors are offering access to corporate networks via unauthorized Fortinet VPN accessCyble observed Initial Access Brokers (IABs) offering access to enterprise networks compromised via a critical...
Month: December 2022
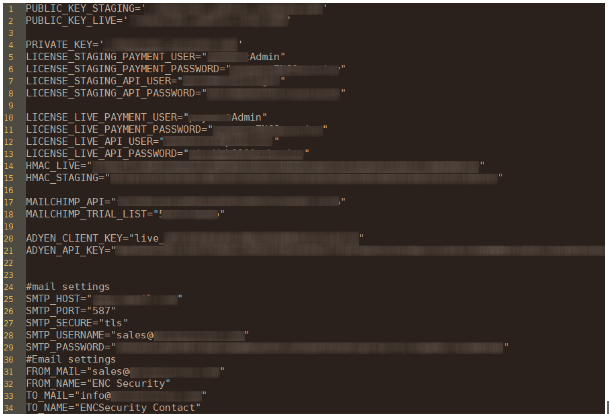
ENC Security, the encryption provider for Sony and Lexar, leaked sensitive data for over a year
ENC Security, the encryption provider for Sony and Lexar, leaked sensitive data for over a yearCyberNews experts discovered that ENC Security, a Netherlands software company, had...
Cloudflare raises monthly plan prices for the first time
Cloudflare raises monthly plan prices for the first timeCloudflare announced today that they are raising prices for their Pro and Business plans for the first time...
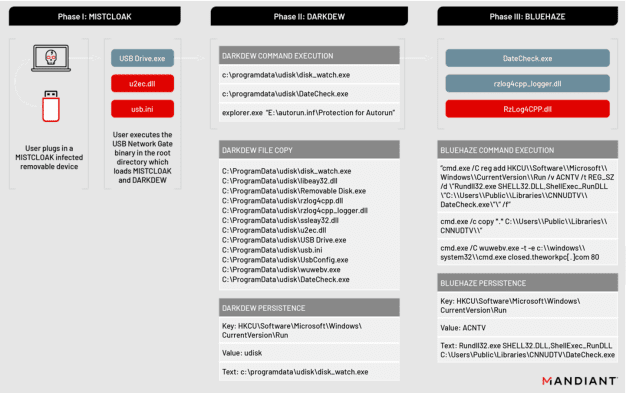
China-linked UNC4191 APT relies on USB Devices in attacks against entities in the Philippines
China-linked UNC4191 APT relies on USB Devices in attacks against entities in the PhilippinesAn alleged China-linked cyberespionage group, tracked as UNC4191, used USB devices in attacks...
Sirius XM flaw unlocks so-called smart cars thanks to code flaw
Sirius XM flaw unlocks so-called smart cars thanks to code flawTelematics program doesn't just give you music, but a big security flaw Sirius XM's Connected Vehicle...
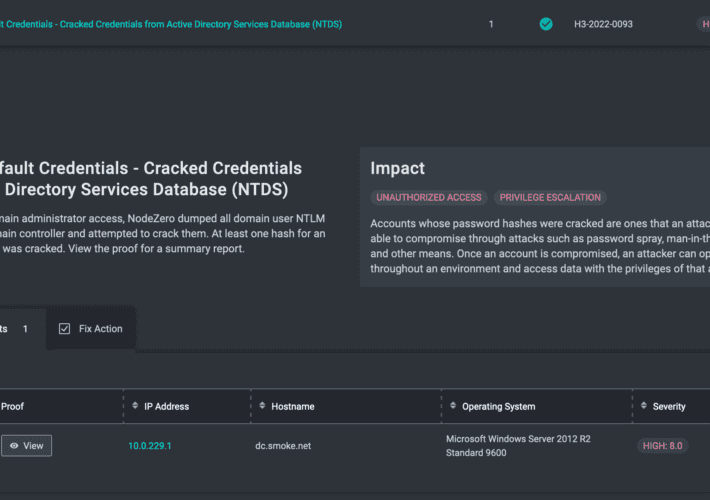
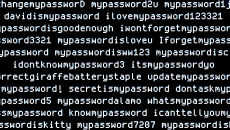
Metrics That Matter: An Attacker’s Perspective on Assessing Password Policy
Metrics That Matter: An Attacker’s Perspective on Assessing Password PolicyAfter compromising a Windows domain controller, one of the actions that NodeZero, our autonomous pentest product, performs...
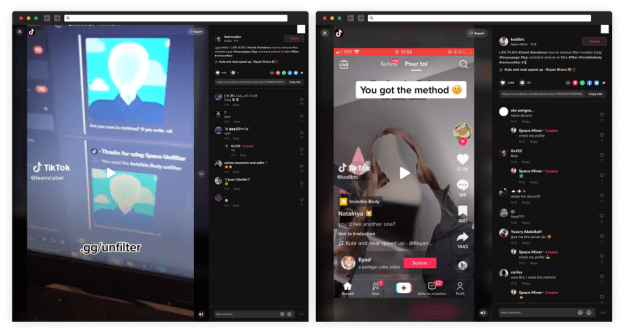
Attackers abused the popular TikTok Invisible Challenge to spread info-stealer
Attackers abused the popular TikTok Invisible Challenge to spread info-stealerThreat actors are exploiting interest in a popular TikTok challenge, dubbed Invisible Challenge, to trick users into...
Cybersecurity researchers take down DDoS botnet by accident
Cybersecurity researchers take down DDoS botnet by accidentWhile analyzing its capabilities, Akamai researchers have accidentally taken down a cryptomining botnet that was also used for distributed...
Almost 300 predatory loan apps found in Google and Apple stores
Almost 300 predatory loan apps found in Google and Apple storesNote to self: Lenders don’t need the contact list on your mobile device Almost 300 apps,...
Label Engineering for Supervised Bot Detection Models
Label Engineering for Supervised Bot Detection ModelsDiscover how label engineering helps DataDome leverage thousands of domain expert rules—updated daily—to identify & block bots in real time....
How Virtual CISOs Are Reshaping SMB Cybersecurity
How Virtual CISOs Are Reshaping SMB Cybersecurity Cybersecurity has become a central business pillar these days. Unfortunately for small and medium businesses, hiring a full-time head...
Google links three exploitation frameworks to Spanish commercial spyware vendor Variston
Google links three exploitation frameworks to Spanish commercial spyware vendor VaristonGoogle’s Threat Analysis Group (TAG) linked three exploitation frameworks to a Spanish surveillance spyware vendor named Variston....
Keeping customers happy means the big IAM just got bigger
Keeping customers happy means the big IAM just got biggerYou need to open up core systems to consumers and partners. Here's how to do it securely...
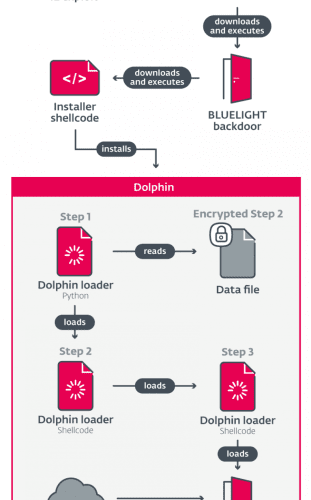
New Windows malware also steals data from victims’ mobile phones
New Windows malware also steals data from victims’ mobile phonesSecurity researchers found a previously unknown backdoor they call Dophin that's been used by North Korean hackers...
S3 Ep110: Spotlight on cyberthreats – an expert speaks [Audio + Text]
S3 Ep110: Spotlight on cyberthreats – an expert speaks [Audio + Text]Latest episode - security expert John Shier explains what the real-life cybercrime stories in the...
Twenty years on, command-line virus scanner ClamAV puts out version 1
Twenty years on, command-line virus scanner ClamAV puts out version 1Used by millions – and the first official finished version The ClamAV command-line virus scanner used...
Voice-scamming site “iSpoof” seized, 100s arrested in massive crackdown
Voice-scamming site “iSpoof” seized, 100s arrested in massive crackdownThose numbers or names that pop up when a call comes up? They're OK as a hint of...
Lastpass discloses the second security breach this year
Lastpass discloses the second security breach this yearLastPass disclosed a new security breach, threat actors had access to its cloud storage using information stolen in the...
Chrome fixes 8th zero-day of 2022 – check your version now (Edge too!)
Chrome fixes 8th zero-day of 2022 – check your version now (Edge too!)There isn't a rhyme to remind you which months have browser zero-days... you just...
Serious Security: MD5 considered harmful – to the tune of $600,000
Serious Security: MD5 considered harmful – to the tune of $600,000It's not just the hashing, by the way. It's the salting and the stretching, too!Leer másNaked...
Google Accuses Spanish Spyware Vendor of Exploiting Chrome, Firefox, and Windows Zero-Days
Google Accuses Spanish Spyware Vendor of Exploiting Chrome, Firefox, and Windows Zero-DaysA Barcelona-based surveillanceware vendor named Variston IT is said to have surreptitiously planted spyware on...
TikTok “Invisible Challenge” porn malware puts us all at risk
TikTok “Invisible Challenge” porn malware puts us all at riskAn injury to one is an injury to all. Especially if the other people are part of...
Intruders gain access to user data in LastPass incident
Intruders gain access to user data in LastPass incidentPassword manager working to identify info affected but says credentials are safely encrypted Intruders broke into a third-party...
Healthcare Breaches Expose Sensitive Information; Twitter Users’ Data Leaked Online
Healthcare Breaches Expose Sensitive Information; Twitter Users’ Data Leaked OnlineThe end of the year is upon us. You’ll soon begin to see plenty of articles recapping...
Lastpass says hackers accessed customer data in new breach
Lastpass says hackers accessed customer data in new breachLastPass says unknown attackers breached its cloud storage using information stolen during a previous security incident from August 2022....
North Korea ScarCruft APT used previously undetected Dolphin Backdoor against South Korea
North Korea ScarCruft APT used previously undetected Dolphin Backdoor against South KoreaNorth Korea-linked ScarCruft group used a previously undocumented backdoor called Dolphin against targets in South Korea. ESET researchers discovered...
3 of the Worst Data Breaches in the World That Could Have Been Prevented
3 of the Worst Data Breaches in the World That Could Have Been PreventedData breaches can be devastating for organizations, these are 3 of the worst...
Critical RCE bugs in Android remote keyboard apps with 2M installs
Critical RCE bugs in Android remote keyboard apps with 2M installsThree Android applications that allow users to use devices as remote keyboards for their computers have...
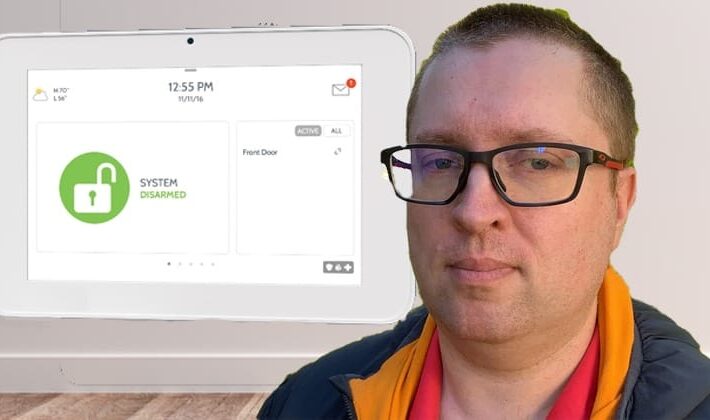
Flaw allowed man to access private information of other Brinks Home Security customers
Flaw allowed man to access private information of other Brinks Home Security customersA Canadian man has revealed that the company he chose to provide security for...
Sigma Rules Bot for Threat Bounty
Sigma Rules Bot for Threat Bounty How to Create, Test & Have Your Sigma Rules Published to SOC Prime’s Platform via Slack SOC Prime has recently...