K11742512: BIND vulnerability CVE-2022-2795BIND vulnerability CVE-2022-2795 Security Advisory Security Advisory Description By flooding the target resolver with queries exploiting this flaw an attacker can significantly impair...
Month: December 2022
K53556508: Apache mod_authz_svn vulnerability CVE-2015-3184
K53556508: Apache mod_authz_svn vulnerability CVE-2015-3184Apache mod_authz_svn vulnerability CVE-2015-3184 Security Advisory Security Advisory Description mod_authz_svn in Apache Subversion 1.7.x before 1.7.21 and 1.8.x before 1.8.14, when using...
K28508558: Apache mod_cache vulnerability CVE-2013-4352
K28508558: Apache mod_cache vulnerability CVE-2013-4352Apache mod_cache vulnerability CVE-2013-4352 Security Advisory Security Advisory Description The cache_invalidate function in modules/cache/cache_storage.c in the mod_cache module in the Apache ......
K17296065: Apache mod_userdir vulnerability CVE-2016-4975
K17296065: Apache mod_userdir vulnerability CVE-2016-4975Apache mod_userdir vulnerability CVE-2016-4975 Security Advisory Security Advisory Description Possible CRLF injection allowing HTTP response splitting attacks for sites which use mod_userdir....
Could we have one app for everything? We ask an expert
Could we have one app for everything? We ask an expertSuper apps can revolutionise your life – but do you want to pay the price, wonders...
No Pressure: Water Utility Drips Alert 4 Months After Breach
No Pressure: Water Utility Drips Alert 4 Months After BreachSome Customers at Risk of Identity Theft, South Staffordshire Water Belatedly WarnsIs a four-month delay between learning...
Why Ransomware Victims Avoid Calling It ‘Ransomware’
Why Ransomware Victims Avoid Calling It 'Ransomware'The latest edition of the ISMG Security Report discusses why too few organizations admit to being victims of ransomware attacks,...
Securonix Taps Ivanti, BMC, SAP Vet Nayaki Nayyar as New CEO
Securonix Taps Ivanti, BMC, SAP Vet Nayaki Nayyar as New CEONayyar Is Securonix's First Female CEO; Longtime CEO Ends 12-Year RunSecuronix has snagged longtime Ivanti, BMC...
Fresh CryWiper Wiper Malware Aims to Destroy Russian Data
Fresh CryWiper Wiper Malware Aims to Destroy Russian DataFake Ransomware Isn't First Wiper to Target Windows Systems in Russia for DeletionWindows systems in Russia are being...
Hacked French Hospital Suspends Emergency Operations
Hacked French Hospital Suspends Emergency OperationsSix Patients Transferred; 'Total Reorganization' Ongoing, Says Health MinisterA French hospital in the Parisian suburbs scrambled to respond to a weekend...
Los piratas informáticos filtran otro conjunto de datos de clientes de Medibank en la Dark Web
Los piratas informáticos filtran otro conjunto de datos de clientes de Medibank en la Dark WebMedibank confirmó el jueves que los actores de amenazas detrás del...
Microsoft Warns of Growing Russian Digital Threats to Europe
Microsoft Warns of Growing Russian Digital Threats to EuropeRussia May Target Supply Chain Operations and Boost Influence OperationsRussian actors may be more willing this winter to...
Qué significa la regla de informes CISA para su protocolo de seguridad de TI
Qué significa la regla de informes CISA para su protocolo de seguridad de TILa nueva Ley de Informes de Incidentes Cibernéticos para Infraestructuras Críticas de 2022...
Revelan una falla en la cadena de suministro que afecta a las bases de datos en la nube de IBM para PostgreSQL
Revelan una falla en la cadena de suministro que afecta a las bases de datos en la nube de IBM para PostgreSQLIBM ha corregido una vulnerabilidad...
Google lanza una nueva actualización del navegador Chrome para parchar otra vulnerabilidad de día cero
Google lanza una nueva actualización del navegador Chrome para parchar otra vulnerabilidad de día ceroEl gigante de las búsquedas Google lanzó el viernes una actualización de...
Piratas informáticos explotan vulnerabilidad de Redis para implementar el nuevo malware Redigo en servidores
Piratas informáticos explotan vulnerabilidad de Redis para implementar el nuevo malware Redigo en servidoresUn malware basado en Go no documentado previamente se dirige a los servidores...
72% de las organizaciones siguen siendo vulnerables a Log4j
72% de las organizaciones siguen siendo vulnerables a Log4jLa vulnerabilidad Log4j (CVE-2021-44228) continúa presentando una gran amenaza para las organizaciones un año después de que la...
Android and iOS apps with 15 million installs extort loan seekers
Android and iOS apps with 15 million installs extort loan seekersOver 280 Android and iOS apps on the Google Play and the Apple App stores trapped...
NVIDIA releases GPU driver update to fix 29 security flaws
NVIDIA releases GPU driver update to fix 29 security flawsNVIDIA has released a security update for its GPU display driver for Windows, containing a fix for...
How Mayhem Helped Uncover a Security Vulnerability in RustOS (CVE-2022-36086)
How Mayhem Helped Uncover a Security Vulnerability in RustOS (CVE-2022-36086)This post outlines some of the techniques used to identify the vulnerability CVE-2022-36086 in RustOS and how...
Microsoft fixes Windows 11 22H2 file copy performance hit
Microsoft fixes Windows 11 22H2 file copy performance hitMicrosoft has addressed a known issue leading to significant performance hits when copying large files over SMB after...
ZetaNile: Open source software trojans from North Korea
ZetaNile: Open source software trojans from North Korea ReversingLabs Malware Researcher Joseph Edwards takes a deep dive into ZetaNile, a set of open-source software trojans being...
What your district should know about the State and Local Cybersecurity Grant Program
What your district should know about the State and Local Cybersecurity Grant ProgramThere’s good news and there’s bad news. The good: Reinforcements are on their way....
Google discovers Windows exploit framework used to deploy spyware
Google discovers Windows exploit framework used to deploy spywareGoogle's Threat Analysis Group (TAG) has linked an exploit framework that targets now-patched vulnerabilities in the Chrome and...
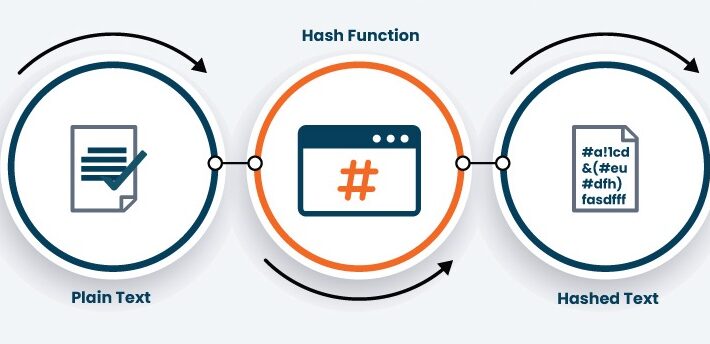
A Comprehensive Study of the Hash Function in Cryptography
A Comprehensive Study of the Hash Function in CryptographyHash Function in Cryptography — Get to know its Definition, Features, Applications, and Necessary Characteristics! Security and privacy...
3 cybersecurity essentials for education institutions and state agencies
3 cybersecurity essentials for education institutions and state agenciesState and local agencies, K–12 school districts, and public institutions of higher learning are rapidly becoming enticing targets...
Tips for Gamifying Your Cybersecurity Awareness Training Program
Tips for Gamifying Your Cybersecurity Awareness Training ProgramIn today’s technological world, educating people about cybersecurity awareness is an absolute necessity. According to one report, 82% of...
Hunter Biden’s Laptop, Privacy and Computer Technicians
Hunter Biden’s Laptop, Privacy and Computer Technicians A recent study conducted by the University of Guelph in Ontario looked at privacy and the practices of computer...
Australia will now fine firms up to AU$50 million for data breaches
Australia will now fine firms up to AU$50 million for data breachesThe Australian parliament has approved a bill to amend the country's privacy legislation, significantly increasing...
CISA adds Oracle Fusion Middleware flaw to its Known Exploited Vulnerabilities Catalog
CISA adds Oracle Fusion Middleware flaw to its Known Exploited Vulnerabilities CatalogCISA added a critical flaw impacting Oracle Fusion Middleware, tracked as CVE-2021-35587, to its Known Exploited Vulnerabilities...