Top 5 Tips for Choosing Endpoint SecurityFollowing years now of digital transformation, cloud migration and deployment of hybrid workforces, enterprises have more endpoints than ever. Which...
Day: December 20, 2022
Healthcare: Essential Defenses for Combating Ransomware
Healthcare: Essential Defenses for Combating RansomwareMove Infrastructure to the Cloud and Hone Incident Response Plans, Experts SayTo avoid having to even consider paying a ransom, experts...
Chinese Hackers Exploit Citrix Vulnerabilities
Chinese Hackers Exploit Citrix VulnerabilitiesHealth Sector Entities Urged to Patch Citrix ADC, Gateway FlawsChinese hackers are exploiting known vulnerabilities in a Citrix networking appliance and virtual...
Microsoft Vulnerability Upgraded to Critical Due to RCE Risk
Microsoft Vulnerability Upgraded to Critical Due to RCE RiskCode-Execution Bug Has Broader Scope that Flaw Exploited by EternalBlue, IBM SaysMicrosoft upgraded a vulnerability first discovered in...
Nueva variante de Agenda Ransomware, escrita en Rust, dirigida a la infraestructura crítica
Nueva variante de Agenda Ransomware, escrita en Rust, dirigida a la infraestructura críticaSe ha observado una variante de Rust de una variedad de ransomware conocida como...
Samba emite actualizaciones de seguridad para parchar múltiples vulnerabilidades de alta gravedad
Samba emite actualizaciones de seguridad para parchar múltiples vulnerabilidades de alta gravedadSamba ha lanzado actualizaciones de software para remediar múltiples vulnerabilidades que, si se explotan con...
Phishing Targets Ukrainian Battlefield Awareness Tool Users
Phishing Targets Ukrainian Battlefield Awareness Tool UsersDigital Map Users Lured Into Installing Malware that Looked for Office FilesA phishing campaign against users of a Ukrainian battlefield...
Moving Containers: Uncovering Challenges. Finding Solutions.
Moving Containers: Uncovering Challenges. Finding Solutions. Get expert tips and best practices for securing containers in your business in our blog from Cloud Security experts, GuidePoint...
Iran-linked Charming Kitten espionage gang bares claws to pollies, power orgs
Iran-linked Charming Kitten espionage gang bares claws to pollies, power orgsContenido de la entradaLeer másProofpoint News Feed
Agenda Ransomware Uses Rust to Target More Vital Industries
Agenda Ransomware Uses Rust to Target More Vital IndustriesThis year, various ransomware-as-a-service groups have developed versions of their ransomware in Rust, including Agenda. Agenda's Rust variant...
How to Address the Skills Gap Crisis with DCIM Software
How to Address the Skills Gap Crisis with DCIM SoftwareData centers are essential components of the modern business landscape, providing the critical infrastructure that enables businesses...
Lacework Stiffens Cloud Security Posture Management
Lacework Stiffens Cloud Security Posture Management Lacework has added additional cloud security posture management (CSPM) capabilities to its platform to make it possible to create fine-grained...
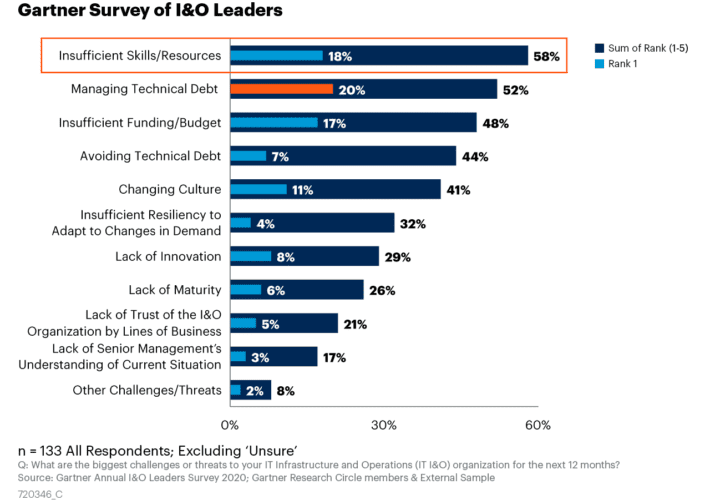
The security skills shortage is here, here’s how to prepare
The security skills shortage is here, here’s how to prepareCorporate security is near the top of the list of CIO concerns for 2023 — but a...
Two-Thirds of Security Pros Have Burnt Out in Past Year
Two-Thirds of Security Pros Have Burnt Out in Past YearExcessive workload is the most common contributing factorLeer másExcessive workload is the most common contributing factor
LogRhythm Partners with SentinelOne to Accelerate Prevention, Detection and Response for Enterprise Environments
LogRhythm Partners with SentinelOne to Accelerate Prevention, Detection and Response for Enterprise EnvironmentsNew integration empowers security teams to identify behavioral anomalies, internal and external threats, and...
Social Blade Confirms Data Breach Exposing PII on the Dark Web
Social Blade Confirms Data Breach Exposing PII on the Dark WebThe company confirmed the data does not include any credit card informationLeer másThe company confirmed the...
The Smart Home Security Guide
The Smart Home Security Guide The smarts behind a smart home come from you. At least when it comes to keeping it more private and secure. ...
Why Privileged Access Management is a priority task
Why Privileged Access Management is a priority taskExploring how PAM can help mitigate and prevent threats to customer dataLeer másArticles RSS FeedExploring how PAM can help...
Hacked Ring Cams Used to Record Swatting Victims
Hacked Ring Cams Used to Record Swatting Victims Photo: BrandonKleinPhoto / Shutterstock.com Two U.S. men have been charged with hacking into the Ring home security cameras...
Meta’s Bug Bounty Program Shows $2m Awarded in 2022
Meta's Bug Bounty Program Shows $2m Awarded in 2022The total amount since the program's establishment in 2011 is reportedly $16mLeer másThe total amount since the program's...
The global state of DevSecOps
The global state of DevSecOpsHow DevOps teams are embracing new approaches of embedding application security testing into their development pipelines to truly achieve DevSecOps and application...
ForgeRock and the new DoD Zero Trust Strategy
ForgeRock and the new DoD Zero Trust StrategyOn November 7, 2023, the United States Department of Defense (DoD) released a new Zero Trust strategy, clarifying the...
How to Surrender to a Drone
How to Surrender to a DroneThe Ukrainian army has released an instructional video explaining how Russian soldiers should surrender to a drone: “Seeing the drone in...
Agenda Ransomware Switches to Rust to Attack Critical Infrastructure
Agenda Ransomware Switches to Rust to Attack Critical InfrastructureVictim companies have a combined revenue of around $550mLeer másVictim companies have a combined revenue of around $550m
Analysts Rate Tesla Mediocre Car Not Even Worth $20 Stock: “too unreliable for widespread use”
Analysts Rate Tesla Mediocre Car Not Even Worth $20 Stock: “too unreliable for widespread use”A car collector is angry the Tesla fraud happened to him. Soon...
Exposing the “Data Leaks” Paradise – An Analysis
Exposing the "Data Leaks" Paradise – An Analysis In a world dominated by a countless number of malicious and fraudulent cyber threat actor adversaries including the...
Ostrich Cyber-Risk Welcomes Chip Whitmer as Vice President of Software Development
Ostrich Cyber-Risk Welcomes Chip Whitmer as Vice President of Software Development Ostrich Cyber-Risk Appoints Chip Whitmer as Vice President of Software Development. Former VP of Platform Architecture at...
API Vulnerabilities Discovered in LEGO Marketplace
API Vulnerabilities Discovered in LEGO MarketplaceThe vulnerabilities, which are now fixed, could have put sensitive customer data at riskLeer másThe vulnerabilities, which are now fixed, could...
Glupteba botnet is back after Google disrupted it in December 2021
Glupteba botnet is back after Google disrupted it in December 2021The Glupteba botnet is back, researchers reported a surge in infection worldwide after Google disrupted its...
NIST to Scrap SHA-1 Algorithm by 2030
NIST to Scrap SHA-1 Algorithm by 2030The agency said it will stop using SHA-1 in its last remaining specified protocols by December 31 2030Leer másThe agency...