Cybersecurity Experts Uncover Inner Workings of Destructive Azov RansomwareCybersecurity researchers have published the inner workings of a new wiper called Azov Ransomware that's deliberately designed to corrupt data...
Day: December 19, 2022
Serious Attacks Could Have Been Staged Through This Amazon ECR Public Gallery Vulnerability
Serious Attacks Could Have Been Staged Through This Amazon ECR Public Gallery VulnerabilityA critical security flaw has been disclosed in Amazon Elastic Container Registry (ECR) Public...
Google Launches OSV-Scanner Tool to Identify Open Source Vulnerabilities
Google Launches OSV-Scanner Tool to Identify Open Source VulnerabilitiesGoogle on Tuesday announced the open source availability of OSV-Scanner, a scanner that aims to offer easy access to...
Cisco Firepower Management Center and Firepower Threat Defense Software SSH Denial of Service Vulnerability
Cisco Firepower Management Center and Firepower Threat Defense Software SSH Denial of Service VulnerabilityA vulnerability in the processing of SSH connections of Cisco Firepower Management Center...
Cisco Firepower Management Center and Firepower Threat Defense Software SSH Denial of Service Vulnerability
Cisco Firepower Management Center and Firepower Threat Defense Software SSH Denial of Service VulnerabilityA vulnerability in the processing of SSH connections of Cisco Firepower Management Center...
Cisco Firepower Management Center Software Command Injection Vulnerabilities
Cisco Firepower Management Center Software Command Injection VulnerabilitiesMultiple vulnerabilities in the web management interface of Cisco Firepower Management Center (FMC) Software could allow an authenticated, remote...
Cisco Firepower Management Center Software Command Injection Vulnerabilities
Cisco Firepower Management Center Software Command Injection VulnerabilitiesMultiple vulnerabilities in the web management interface of Cisco Firepower Management Center (FMC) Software could allow an authenticated, remote...
New Actively Exploited Zero-Day Vulnerability Discovered in Apple Products
New Actively Exploited Zero-Day Vulnerability Discovered in Apple ProductsApple on Tuesday rolled out security updates to iOS, iPadOS, macOS, tvOS, and Safari web browser to address...
A tell-all conversation: The biggest cloud security trends, challenges & solutions
A tell-all conversation: The biggest cloud security trends, challenges & solutionsEXECUTIVE SUMMARY: In this dynamic tell-all conversation, excerpted from The TechArena podcast, VP of Cloud Security...
GUEST ESSAY: ‘Initial access brokers’ — IABs — specialize in enabling surreptitious access
GUEST ESSAY: ‘Initial access brokers’ — IABs — specialize in enabling surreptitious accessCybercrime is a big business. And like any other large industry, specialization has emerged....
Hackers Actively Exploiting Citrix ADC and Gateway Zero-Day Vulnerability
Hackers Actively Exploiting Citrix ADC and Gateway Zero-Day VulnerabilityThe U.S. National Security Agency (NSA) on Tuesday said a threat actor tracked as APT5 has been actively exploiting a...
Why PCI DSS 4.0 Should Be on Your Radar in 2023
Why PCI DSS 4.0 Should Be on Your Radar in 2023Protecting customer data is critical for any business accepting online payment information. The Payment Card Industry...
Can Thieves Steal Identities With Only a Name and Address?
Can Thieves Steal Identities With Only a Name and Address? Can thieves steal identities with only a name and address? In short, the answer is “no.”...
Ransomware Attackers Use Microsoft-Signed Drivers to Gain Access to Systems
Ransomware Attackers Use Microsoft-Signed Drivers to Gain Access to SystemsMicrosoft on Tuesday disclosed it took steps to implement blocking protections and suspend accounts that were used...
Know Your Superpower: Brenda’s McAfee Journey
Know Your Superpower: Brenda’s McAfee Journey Our How I Got Here series spotlights the stories of McAfee team members who have successfully grown their careers. Read more about...
How to Protect Yourself From Identity Theft After a Data Breach
How to Protect Yourself From Identity Theft After a Data Breach Did you just get word that your personal information may have been caught up in...
How to Browse Privately on Your Phone
How to Browse Privately on Your Phone Your phone is likely a daily companion, giving you access to work emails, chats with friends, weather reports, and...
New GoTrim Botnet Attempting to Break into WordPress Sites’ Admin Accounts
New GoTrim Botnet Attempting to Break into WordPress Sites' Admin AccountsA new Go-based botnet has been spotted scanning and brute-forcing self-hosted websites using the WordPress content...
Six Charged in Mass Takedown of DDoS-for-Hire Sites
Six Charged in Mass Takedown of DDoS-for-Hire SitesThe U.S. Department of Justice (DOJ) today seized four-dozen domains that sold “booter” or “stresser” services — businesses that...
Social Blade Confirms Data Breach Exposing PII on the Dark Web
Social Blade Confirms Data Breach Exposing PII on the Dark WebThe company confirmed the data does not include any credit card informationLeer másThe company confirmed the...
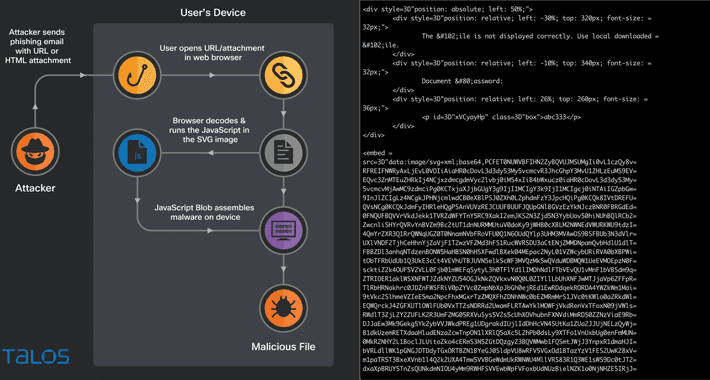
Hacking Using SVG Files to Smuggle QBot Malware onto Windows Systems
Hacking Using SVG Files to Smuggle QBot Malware onto Windows SystemsPhishing campaigns involving the Qakbot malware are using Scalable Vector Graphics (SVG) images embedded in HTML email attachments....
NIST says you better dump weak SHA-1 … by 2030
NIST says you better dump weak SHA-1 ... by 2030How about right now? Right now is good The US National Institute of Standards and Technology (NIST)...
This year’s hottest tech: Related privacy concerns
This year’s hottest tech: Related privacy concerns The holiday season is upon us, and many of us are looking forward to soon unwrapping the latest and...
Know Your Gamer: The Need for Identity Verification in the Gaming Industry 2023
Know Your Gamer: The Need for Identity Verification in the Gaming Industry 2023Isn’t it time the video gaming business rectified its KYG (Know Your Gamer) issue...
What are RUA and RUF in DMARC?
What are RUA and RUF in DMARC?DMARC, or Domain-based Messaging Authentication, Reporting, and Conformance is an […] The post What are RUA and RUF in DMARC?...
Instagram: Are You a Pig?
Instagram: Are You a Pig?I thought this street edit of an Instagram billboard was pretty clever: The post Instagram: Are You a Pig? appeared first on...
Facebook Cracks Down on Spyware Vendors from U.S., China, Russia, Israel, and India
Facebook Cracks Down on Spyware Vendors from U.S., China, Russia, Israel, and IndiaMeta Platforms disclosed that it took down no less than 200 covert influence operations...
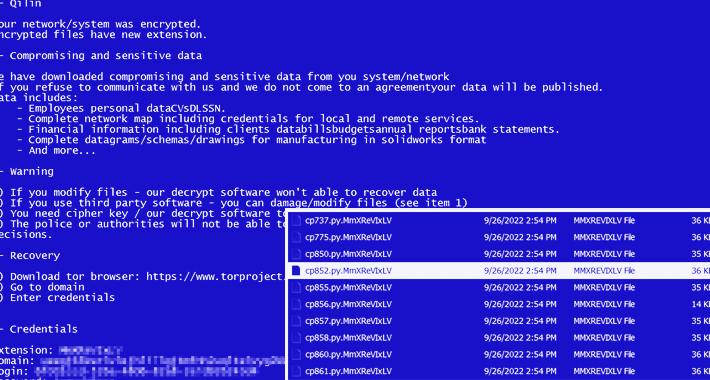
New Agenda Ransomware Variant, Written in Rust, Aiming at Critical Infrastructure
New Agenda Ransomware Variant, Written in Rust, Aiming at Critical InfrastructureA Rust variant of a ransomware strain known as Agenda has been observed in the wild, making it...