MY TAKE: Poll shows consumers won’t patronize companies that fail to assure ‘digital trust’It’s all too easy to take for granted the amazing digital services we...
Day: December 15, 2022
The Microsoft Teams chat integration into Outlook
The Microsoft Teams chat integration into OutlookEXECUTIVE SUMMARY: What would it be like if Microsoft Teams were integrated into Outlook? Microsoft is not only working on...
GUEST ESSAY: Why ‘continuous pentesting’ is high among the trends set to accelerate in 2023
GUEST ESSAY: Why ‘continuous pentesting’ is high among the trends set to accelerate in 2023There is much that can be gleaned from helping companies identify and...
Attackers use SVG files to smuggle QBot malware onto Windows systems
Attackers use SVG files to smuggle QBot malware onto Windows systemsQBot malware phishing campaigns have adopted a new distribution method using SVG files to perform HTML...
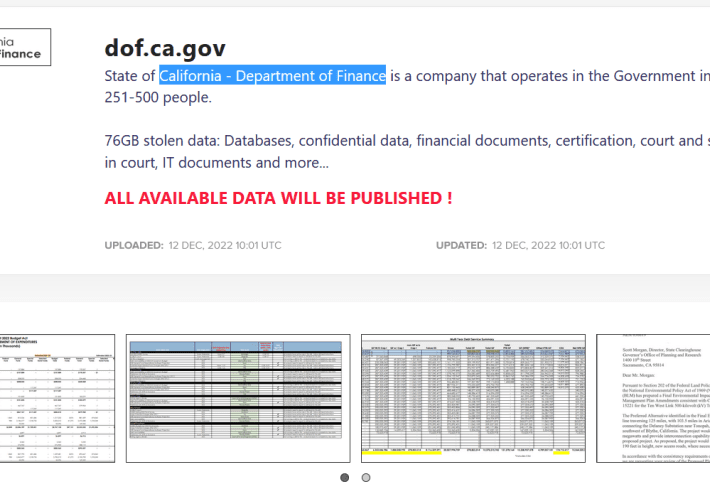
Lockbit ransomware gang hacked California Department of Finance
Lockbit ransomware gang hacked California Department of FinanceLockBit ransomware gang hacked the California Department of Finance and threatens to leak data stolen from its systems. The...
LockBit Ransomware 101: Here’s What You Need to Know
LockBit Ransomware 101: Here’s What You Need to KnowLockBit ransomware is a malicious software designed for one thing: locking up the user’s computer in exchange for...
Loan Fee Fraud Surges by a Fifth as Christmas Approaches
Loan Fee Fraud Surges by a Fifth as Christmas ApproachesFCA warns of pressure tactics as cost of living bitesLeer másFCA warns of pressure tactics as cost...
(Re) thinking about cyber security in terms of risk management
(Re) thinking about cyber security in terms of risk managementBy Tom Boltman, VP of Strategic Initiatives at Kovrr. Prior to Kovrr Tom held senior leadership positions...
FBI seized domains linked to 48 DDoS-for-hire service platforms
FBI seized domains linked to 48 DDoS-for-hire service platformsThe US Department of Justice has seized 48 Internet domains and charged six suspects for their involvement in...
Citrix and NSA urge admins to fix actively exploited zero-day in Citrix ADC and Gateway
Citrix and NSA urge admins to fix actively exploited zero-day in Citrix ADC and GatewayCitrix urges customers to update their installs to fix actively exploited zero-day...
The FBI Just Seized 48 Domain Names Linked to DDoS-For-Hire Platforms
The FBI Just Seized 48 Domain Names Linked to DDoS-For-Hire PlatformsThe Department of Justice has taken down 48 domains and charged six individuals for operating “booter”...
Iranian hacking group expands focus to US politicians, critical infrastructure, researchers find
Iranian hacking group expands focus to US politicians, critical infrastructure, researchers findContenido de la entradaLeer másProofpoint News Feed
New Google Tool Helps Devs Root Out Open Source Bugs
New Google Tool Helps Devs Root Out Open Source BugsFree OSV-Scanner searches transitive dependenciesLeer másFree OSV-Scanner searches transitive dependencies
International Engagement Blog: Singapore International Cyber Week, the Regional Initiative for Cybersecurity Education and Training, and More
International Engagement Blog: Singapore International Cyber Week, the Regional Initiative for Cybersecurity Education and Training, and MoreNIST has continued to collaborate into the fall season with...
New Attack Vector: 144k Phishing Packages Found on Open-source Repositories
New Attack Vector: 144k Phishing Packages Found on Open-source RepositoriesThreat actors found a new attack vector spamming open-source ecosystem with packages that contain links to phishing...
VMware fixed critical VM Escape bug demonstrated at Geekpwn hacking contest
VMware fixed critical VM Escape bug demonstrated at Geekpwn hacking contestVMware fixed three flaws in multiple products, including a virtual machine escape issue exploited at the...
How acceptable is your acceptable use policy?
How acceptable is your acceptable use policy?In a world before smartphones, social media, and hybrid workplaces, an acceptable use policy was a lot easier to write—and...
3.5m IP cameras exposed, with US in the lead
3.5m IP cameras exposed, with US in the leadThe number of internet-facing cameras in the world is growing exponentially. Some of the most popular brands don’t...
Windows Zero-day Exploited for Ransomware Was Fixed
Windows Zero-day Exploited for Ransomware Was FixedMicrosoft announced an important zero-day that threat actors used for launching ransomware attacks was resolved during the latest Patch Tuesday....
Apple Fixes Actively Exploited iPhone Zero-Day Vulnerability
Apple Fixes Actively Exploited iPhone Zero-Day VulnerabilityThe vulnerability could allow remote code execution (RCE) on a victim's deviceLeer másThe vulnerability could allow remote code execution (RCE)...
Why Privileged Access Management is a priority task
Why Privileged Access Management is a priority taskExploring how PAM can help mitigate and prevent threats to customer dataLeer másArticles RSS FeedExploring how PAM can help...
New Royal ransomware group evades detection with partial encryption
New Royal ransomware group evades detection with partial encryptionA new ransomware group dubbed Royal that formed earlier this year has significantly ramped up its operations over...
Mozilla Fixes Firefox Vulnerabilities That Could Have Lead to System Takeover
Mozilla Fixes Firefox Vulnerabilities That Could Have Lead to System TakeoverMultiple high-impact vulnerabilities affecting Thunderbird, Firefox ESR, and Firefox were fixed by updates from Mozilla. The...
Obligatory ChatGPT Post
Obligatory ChatGPT PostSeems like absolutely everyone everywhere is playing with Chat GPT. So I did, too…. Write an essay in the style of Bruce Schneier on...
Apple fixed the tenth actively exploited zero-day this year
Apple fixed the tenth actively exploited zero-day this yearApple rolled out security updates to iOS, iPadOS, macOS, tvOS, and Safari to fix a new actively exploited...
Hacking Boston’s CharlieCard
Hacking Boston’s CharlieCardInteresting discussion of vulnerabilities and exploits against Boston’s CharlieCard. Leer másSchneier on SecurityInteresting discussion of vulnerabilities and exploits against Boston’s CharlieCard.
AgentTesla Remains Most Prolific Malware in November, Emotet and Qbot Grow
AgentTesla Remains Most Prolific Malware in November, Emotet and Qbot GrowThese are some of the key findings from the latest Check Point Research Most Wanted reportLeer...
Reimagining Democracy
Reimagining DemocracyLast week, I hosted a two-day workshop on reimagining democracy. The idea was to bring together people from a variety of disciplines who are all...
A Security Vulnerability in the KmsdBot Botnet
A Security Vulnerability in the KmsdBot BotnetSecurity researchers found a software bug in the KmsdBot cryptomining botnet: With no error-checking built in, sending KmsdBot a malformed...
December 2022 Patch Tuesday fixed 2 zero-day flaws
December 2022 Patch Tuesday fixed 2 zero-day flawsMicrosoft released December 2022 Patch Tuesday security updates that fix 52 vulnerabilities across its products. Microsoft December 2022 Patch Tuesday security...