Panel Discussion | Demystifying Cyber Risk QuantificationContenido de la entradaLeer másDataBreachToday.com RSS Syndication
Day: December 14, 2022
Irish Healthcare Ransomware Hack Cost Over 80 Million Euros
Irish Healthcare Ransomware Hack Cost Over 80 Million EurosVictims Still Learning Their Personal Data Was Illegally Accessed, Copied in 2021A ransomware attack on the Irish healthcare...
LockBit 3.0 Ransomware Threatens Health Sector, Feds Warn
LockBit 3.0 Ransomware Threatens Health Sector, Feds WarnLatest Variant Uses Capabilities of BlackMatter, Other MalwareU.S. federal authorities are warning healthcare providers, vendors and public health sector...
Fortinet advierte sobre la explotación activa de la nueva vulnerabilidad RCE de autenticación previa de SSL-VPN
Fortinet advierte sobre la explotación activa de la nueva vulnerabilidad RCE de autenticación previa de SSL-VPNFortinet emitió el lunes parches de emergencia para una falla de...
DNS Is Conduit Into Air-Gapped Networks, Say Researchers
DNS Is Conduit Into Air-Gapped Networks, Say ResearchersAttackers Use DNS Tunneling as Command-and-Control Channel, Says PenteraAssets kept behind air-gapped networks should be inaccessible, but researchers from...
Variedades de malware dirigidas a desarrolladores de Python y JavaScript a través de repositorios oficiales
Variedades de malware dirigidas a desarrolladores de Python y JavaScript a través de repositorios oficialesUna campaña activa de malware está dirigida a los repositorios Python Package...
K83430580: SAMBA vulnerability CVE-2022-42898
K83430580: SAMBA vulnerability CVE-2022-42898SAMBA vulnerability CVE-2022-42898 Security Advisory Security Advisory Description ** RESERVED ** This candidate has been reserved by an organization or individual that will...
Sam Bankman-Fried’s Terrible, Horrible, Very Bad Day
Sam Bankman-Fried's Terrible, Horrible, Very Bad DayFormer FTX CEO Will Stay in Bahamas Jail Pending Extradition to USThe many alleged failures of former FTX CEO Sam...
K45012151: Layer 2 security bypass issue CVE-2021-27861, CVE-2021-27862, CVE-2021-27853, CVE-2021-27854
K45012151: Layer 2 security bypass issue CVE-2021-27861, CVE-2021-27862, CVE-2021-27853, CVE-2021-27854Layer 2 security bypass issue CVE-2021-27861, CVE-2021-27862, CVE-2021-27853, CVE-2021-27854 Security Advisory Security Advisory Description CVE-2021-27861 Layer 2...
K87046687: VMware Tools vulnerability CVE-2022-31676
K87046687: VMware Tools vulnerability CVE-2022-31676VMware Tools vulnerability CVE-2022-31676 Security Advisory Security Advisory Description VMware Tools (12.0.0, 11.x.y and 10.x.y) contains a local privilege escalation vulnerability. A...
K37923932: libTIFF vulnerability CVE-2022-3970
K37923932: libTIFF vulnerability CVE-2022-3970libTIFF vulnerability CVE-2022-3970 Security Advisory Security Advisory Description A vulnerability was found in LibTIFF. It has been classified as critical. This affects the...
K17011311: NodeJS vulnerability CVE-2022-35256
K17011311: NodeJS vulnerability CVE-2022-35256NodeJS vulnerability CVE-2022-35256 Security Advisory Security Advisory Description The llhttp parser in the http module in Node v18.7.0 does not correctly handle header...
15 seasonal cyber security shopping tips, keep your celebrations bright
15 seasonal cyber security shopping tips, keep your celebrations brightEXECUTIVE SUMMARY: Many people are eager to celebrate the beauty of the holiday season with parties, parades,...
Malware Strains Targeting Python and JavaScript Developers Through Official Repositories
Malware Strains Targeting Python and JavaScript Developers Through Official RepositoriesAn active malware campaign is targeting the Python Package Index (PyPI) and npm repositories for Python and...
Proofpoint to Buy Deception Firm Illusive, Boost Offerings
Proofpoint to Buy Deception Firm Illusive, Boost OfferingsContenido de la entradaLeer másProofpoint News Feed
Microsoft-signed malicious Windows drivers used in ransomware attacks
Microsoft-signed malicious Windows drivers used in ransomware attacksMicrosoft has revoked several Microsoft hardware developer accounts after drivers signed through their profiles were used in cyberattacks, including...
Are robots too insecure for lethal use by law enforcement?
Are robots too insecure for lethal use by law enforcement?In late November, the San Francisco Board of Supervisors voted 8-3 to give the police the option...
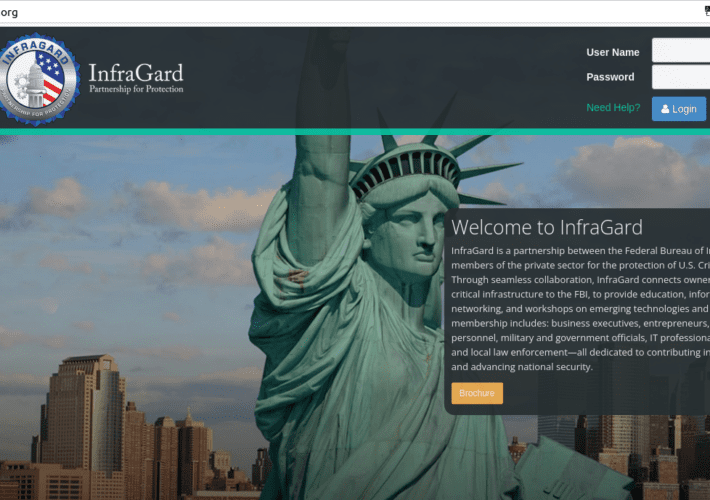
FBI’s Vetted Info Sharing Network ‘InfraGard’ Hacked
FBI’s Vetted Info Sharing Network ‘InfraGard’ HackedInfraGard, a program run by the U.S. Federal Bureau of Investigation (FBI) to build cyber and physical threat information sharing...
Twitter Addresses November Data Leak Claims
Twitter Addresses November Data Leak ClaimsNo passwords were reportedly exposed, but Twitter prompted users to enable 2FA to protect accountsLeer másNo passwords were reportedly exposed, but...
PCI Secure Software Standard version 1.2 sets out new payment security requirements
PCI Secure Software Standard version 1.2 sets out new payment security requirementsThe Payment Card Industry Security Standards Council (PCI SSC) has published version 1.2 of the...
European Commission takes step toward approving EU-US data privacy pact
European Commission takes step toward approving EU-US data privacy pactThe EU-US Data Privacy Framework—drafted to allow the flow of data between the US and the European...
Palo Alto Networks flags top cyberthreats, offers new zero-day protections
Palo Alto Networks flags top cyberthreats, offers new zero-day protectionsFirewall and security software vendor Palo Alto Network’s annual Ignite conference kicked off Tuesday, highlighted by several...
BrandPost: Securing Operational Technology Environments for Critical Infrastructure
BrandPost: Securing Operational Technology Environments for Critical InfrastructureJuniper Networks is applying its industry leading AI-driven capabilities and cloud-native architectures to Critical Infrastructure (CI) networks. We’re directly...
FBI’s Vetted Info Sharing Network ‘InfraGard’ Hacked
FBI’s Vetted Info Sharing Network ‘InfraGard’ HackedInfraGard, a program run by the U.S. Federal Bureau of Investigation (FBI) to build cyber and physical threat information sharing...
COVID-bit: the wireless spyware trick with an unfortunate name
COVID-bit: the wireless spyware trick with an unfortunate nameIt's not the switching that's the problem, it's the switching of the switching!Leer másNaked SecurityIt's not the switching...
Apple patches everything, finally reveals mystery of iOS 16.1.2
Apple patches everything, finally reveals mystery of iOS 16.1.2There's an update for everything this time, not just for iOS.Leer másNaked SecurityThere's an update for everything this...
How Amazon’s new Identity Verification System authenticates Seller Identity
How Amazon’s new Identity Verification System authenticates Seller IdentityAs a new alternative to offline seller onboarding, a new digital onboarding method is being tested by amazon...
Patch Tuesday: 0-days, RCE bugs, and a curious tale of signed malware
Patch Tuesday: 0-days, RCE bugs, and a curious tale of signed malwareTales of derring-do in the cyberunderground! (And some zero-days.)Leer másNaked SecurityTales of derring-do in the...