What Is Vulnerability Management?Some people still believe their IT infrastructure is unflawed simply because they’ve never experienced a cybersecurity incident – until something goes wrong and...
Day: November 28, 2022
What Is a Privileged Access Management (PAM) Policy?
What Is a Privileged Access Management (PAM) Policy?Cybersecurity technology goes hand in hand with policy-based governance, but simply developing a password policy to protect company data...
142 Arrests in the Biggest-Ever Counter-Fraud Operation Involving a Spoofing Shop
142 Arrests in the Biggest-Ever Counter-Fraud Operation Involving a Spoofing ShopOn Thursday, November 24, Europol and the United Kingdom’s police announced they stopped a criminal network...
Over 1,600 Docker Hub Repositories Were Found to Hide Malware
Over 1,600 Docker Hub Repositories Were Found to Hide MalwareMore than 1,600 publicly available images on Docker Hub were found to hide malicious behavior, including DNS...
The Pig Butchery Scams That The U.S. Department of Justice Just Busted
The Pig Butchery Scams That The U.S. Department of Justice Just BustedAuthorities have finally begun to crack down on fake investment platforms used by scammers. The...
INTERPOL: $130 Million Seized and 1,000 Suspects Arrested in Operation “HAECHI III”
INTERPOL: $130 Million Seized and 1,000 Suspects Arrested in Operation “HAECHI III”INTERPOL announced the results of a five-month operation codenamed “HAECHI III”: almost 1,000 suspects were...
RansomExx Ransomware upgrades to Rust programming language
RansomExx Ransomware upgrades to Rust programming languageRansomExx ransomware is the last ransomware in order of time to have a version totally written in the Rust programming...
What Are Mobile Device Threats and How to Avoid Them
What Are Mobile Device Threats and How to Avoid ThemMobile device threats are menaces over your mobile device that can manifest at the network level, can...
For Cybercriminals, the Game is On and They’re Playing to Win
For Cybercriminals, the Game is On and They’re Playing to WinWhy Football Clubs Need to Up their Cyber Defence By Ravi Pather, VP, Europe and Middle...
UK urges to disconnect Chinese security cameras in government buildings
UK urges to disconnect Chinese security cameras in government buildingsThe British government banned the installation of Chinese-linked security cameras at sensitive facilities due to security risks....
The Role of Compliance in Cybersecurity
The Role of Compliance in CybersecurityCybersecurity compliance is essential as it contributes to cyberspace safety in meaningful ways By Anas Baig, Product Manager, […] The post...
From Edge to Core: Security in the Data Center
From Edge to Core: Security in the Data CenterBy Timothy Liu, CTO and Co-Founder, Hillstone Networks Most organizations recognize the data center as the most essential...
Student Verification: How Edtech can benefit from Student ID Verification APIs
Student Verification: How Edtech can benefit from Student ID Verification APIsDue to the growing acceptance of distance learning, digital courses, and most recently, the COVID-19 epidemic,...
GUEST ESSAY: What ‘self-sovereign-identities’ are all about — and how SSIs can foster public good
GUEST ESSAY: What ‘self-sovereign-identities’ are all about — and how SSIs can foster public goodGovernment assistance can be essential to individual wellbeing and economic stability. This...
You Can’t Prevent Every Attack, But You Can Mitigate the Damage
You Can’t Prevent Every Attack, But You Can Mitigate the DamageMore than ever, attackers are leveraging compromised identities to carry out cyberattacks. Stopping them is a...
Why Microsegmentation is Critical for Securing CI/CD
Why Microsegmentation is Critical for Securing CI/CD Modern development environments are characterized by cloud-native technology, microservices architectures and DevOps or DevSecOps teams working in close coordination...
The 12 Online Scams of Christmas
The 12 Online Scams of ChristmasWhether you are a Christmas lover or more of a Grinch, chances are you’re going to do some online shopping whether...
Understanding Cybersecurity in IoT: The Power of Small Steps
Understanding Cybersecurity in IoT: The Power of Small StepsIn today’s digital world, the Internet of Things (IoT) is everywhere. From smart watches and televisions to connected...
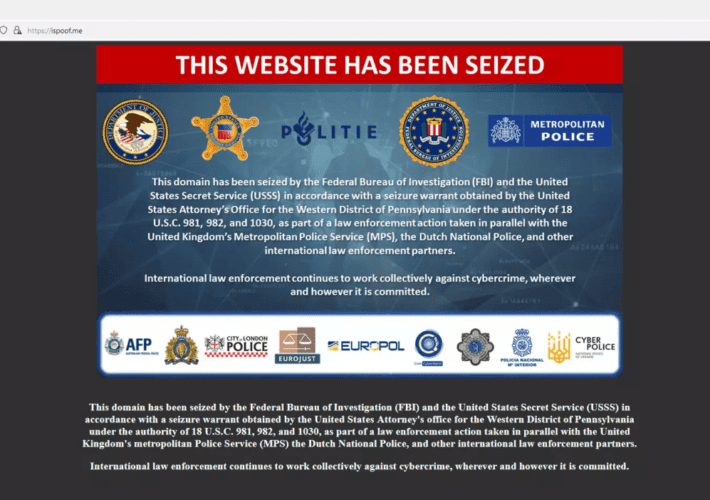
An international police operation dismantled the spoofing service iSpoof
An international police operation dismantled the spoofing service iSpoofAn international law enforcement operation has dismantled an online phone number spoofing service called iSpoof. An international law enforcement...
RansomExx2 Released – Linux Users, Watch Out For a New Ransomware Variant!
RansomExx2 Released – Linux Users, Watch Out For a New Ransomware Variant!Linux users should be on guard for the new variant of RansomExx ransomware that was...
Cybersecurity Threats Need Fresh Data Recovery Strategies
Cybersecurity Threats Need Fresh Data Recovery Strategies The information age is a double-edged sword. Advanced technologies are accelerating incredible achievements for businesses and consumers. We are...
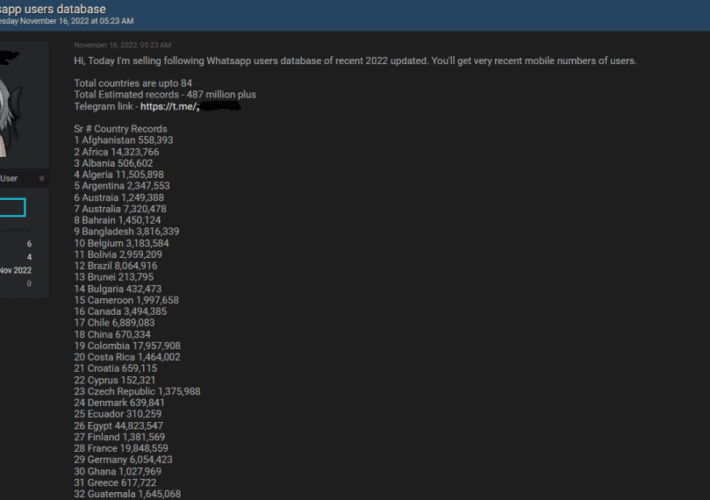
Experts investigate WhatsApp data leak: 500M user records for sale
Experts investigate WhatsApp data leak: 500M user records for saleCybernews investigated a data sample available for sale containing up-to-date mobile phone numbers of nearly 500 million...
Cybersecurity Threats Require More Hands-On Investment by US Oil and Gas Companies
Cybersecurity Threats Require More Hands-On Investment by US Oil and Gas CompaniesBy Martin Riley, Director of Managed Security Services, Bridewell The US oil and gas industry...
FC Barcelona’s Website Used by Scammers for Fraud
FC Barcelona’s Website Used by Scammers for FraudTop European football club, FC Barcelona, recently has its official website used by scammers in a sophisticated third-party fraud...
Google fixed the eighth actively exploited #Chrome #zeroday this year
Google fixed the eighth actively exploited #Chrome #zeroday this yearGoogle on Thursday released security updates to address a new zero-day vulnerability, tracked as CVE-2022-4135, impacting the...
Account Takeover & Compromised Accounts: Protecting Your Business From ATO Attacks
Account Takeover & Compromised Accounts: Protecting Your Business From ATO AttacksAccount takeover/ATO attacks have been on the rise throughout 2022, meaning more criminals are taking control...
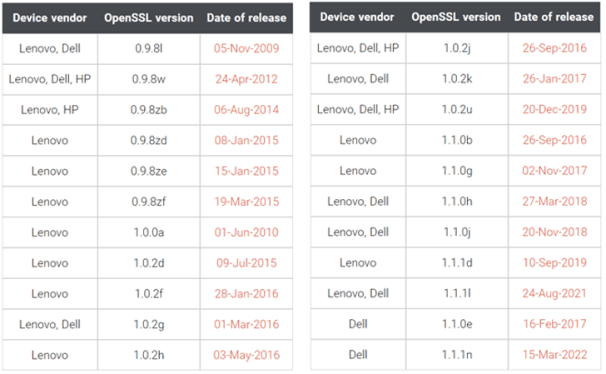
Devices from Dell, HP, and Lenovo used outdated OpenSSL versions
Devices from Dell, HP, and Lenovo used outdated OpenSSL versionsResearchers discovered that devices from Dell, HP, and Lenovo are still using outdated versions of the OpenSSL cryptographic library....
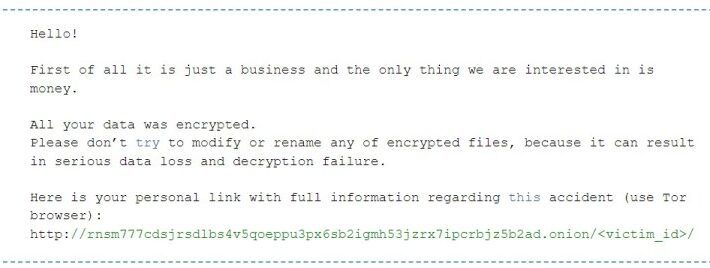
Vice Society Ransomware Gang Strikes Again
Vice Society Ransomware Gang Strikes AgainThe name of the ransomware gang known as Vice Society is now linked to new victims, as stolen data is being...
Here is why you should have Cobalt Strike detection in place
Here is why you should have Cobalt Strike detection in placeGoogle recently released a list of YARA detection rules for malicious variants of the legitimate Cobalt...
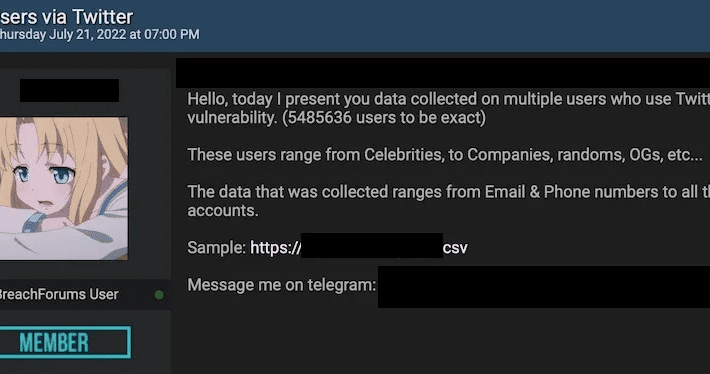
Data from 5.4M Twitter users obtained from multiple threat actors and combined with data from other breaches
Data from 5.4M Twitter users obtained from multiple threat actors and combined with data from other breachesThe massive data breach suffered by Twitter that exposed emails...