GUEST ESSAY: The rising need to defend against super hackers, master thieves and digital ghostsConsider what might transpire if malicious hackers began to intensively leverage Artificial...
Day: November 21, 2022
GUEST ESSAY — Security practices companies must embrace to stop AI-infused cyber attacks
GUEST ESSAY — Security practices companies must embrace to stop AI-infused cyber attacksConsider what might transpire if malicious hackers began to intensively leverage Artificial Intelligence (AI)...
Building a World-Class eSIM Registration Process
Building a World-Class eSIM Registration ProcessTelcos are part of the vital infrastructure that serves as a forerunner for the rest of the industry as their digital...
Aviation Starting to Get Hit with Rise of Cyberattacks Post-Pandemic
Aviation Starting to Get Hit with Rise of Cyberattacks Post-PandemicThreat actors are turning their attention to the aviation industry post-pandemic, but what motivations and challenges are...
What is Security Service Edge(SSE) and How Does It Help to Achieve SASE?
What is Security Service Edge(SSE) and How Does It Help to Achieve SASE?Introduction Every technology has its downside. Likewise, internet use also has its drawback of...
Fall lawn cleaning – AppSec style | Contrast Security
Fall lawn cleaning – AppSec style | Contrast Security Every year toward the end of September, I get anxious about the falling leaves. This year, I...
Google Wins Lawsuit Against Russians Linked to Blockchain-based Glupteba Botnet
Google Wins Lawsuit Against Russians Linked to Blockchain-based Glupteba BotnetGoogle has won a lawsuit filed against two Russian nationals in connection with the operation of a...
Webinar – Manage “Achieving DOD Impact Level 4 – Lessons Learned & Much More”
Webinar – Manage “Achieving DOD Impact Level 4 – Lessons Learned & Much More”If you are an ISV or SaaS solutions provider looking to pursue US...
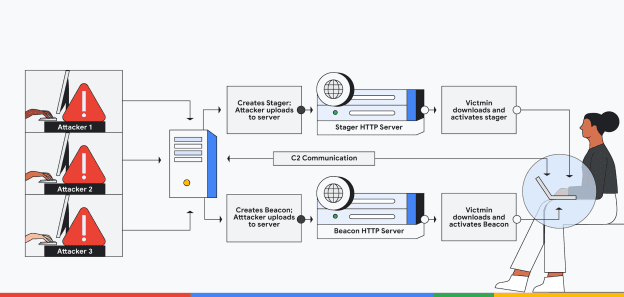
Google Identifies 34 Cracked Versions of Popular Cobalt Strike Hacking Toolkit in the Wild
Google Identifies 34 Cracked Versions of Popular Cobalt Strike Hacking Toolkit in the WildGoogle Cloud last week disclosed that it identified 34 different hacked release versions...
Supreme Court to Consider Identity Theft Case
Supreme Court to Consider Identity Theft Case William Dubin, a licensed psychologist in Austin, Texas, provided psychological services to a youth facility known as Williams House....
Been Doing It The Same Way For Years? Think Again.
Been Doing It The Same Way For Years? Think Again.[Want Bob to stop complaining? Change your practices.] [Don't delay change – it can cost you] ["Always...
How to Add DMARC Record in Namecheap
How to Add DMARC Record in NamecheapFor any organization, its email infrastructure must be crucial. The first step to start protecting your domain for your clients,...
Achieve Defense-in-Depth in Multi-Cloud Environments
Achieve Defense-in-Depth in Multi-Cloud Environments Today, 90% of organizations are operating in hybrid and multi-cloud environments—a number that has increased over the past two years due...
How remote working impacts security incident reporting
How remote working impacts security incident reportingThe ability for employees to work remotely comes with many benefits, from better work-life balance to lower expenses to higher...
Tor vs. VPN: Which should you choose?
Tor vs. VPN: Which should you choose?Both Tor and a VPN can greatly help you keep prying eyes away from your online life, but they’re also...
Netflix Phishing Emails Surge 78%
Netflix Phishing Emails Surge 78%Social engineers are using Unicode techniques to bypass filtersLeer másSocial engineers are using Unicode techniques to bypass filters
CISA, NSA, ODNI Publish Software Supply Chain Guidelines For Customers
CISA, NSA, ODNI Publish Software Supply Chain Guidelines For CustomersThe come after the August release of guidance for developers and the October one for suppliersLeer másThe...
New improved versions of LodaRAT spotted in the wild
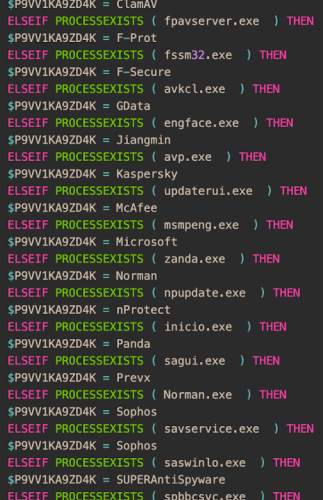
New improved versions of LodaRAT spotted in the wildCisco Talos spotted multiple updated versions of LodaRAT that were deployed alongside other malware families, including RedLine and...
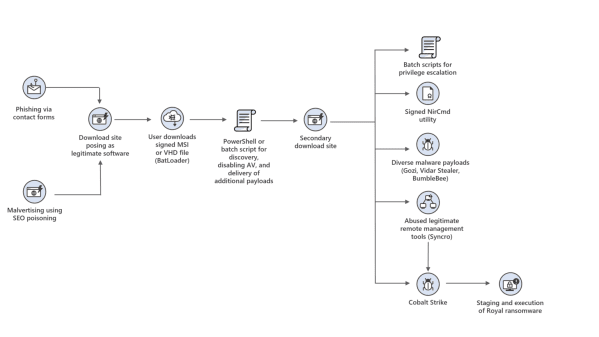
Emerging Threat Actor DEV-0569 Expands Its Toolkit to Deliver Royal Ransomware
Emerging Threat Actor DEV-0569 Expands Its Toolkit to Deliver Royal RansomwareAs well as malvertising and phishing links, the new threat actor is now also using contact...
New AXLocker Ransomware Steals Victims’ Discord Tokens
New AXLocker Ransomware Steals Victims' Discord TokensResearchers also discover two additional new variantsLeer másResearchers also discover two additional new variants
Ten Charged in $11m Healthcare BEC Plots
Ten Charged in $11m Healthcare BEC PlotsSeveral of the men diverted funds intended for hospitalsLeer másSeveral of the men diverted funds intended for hospitals
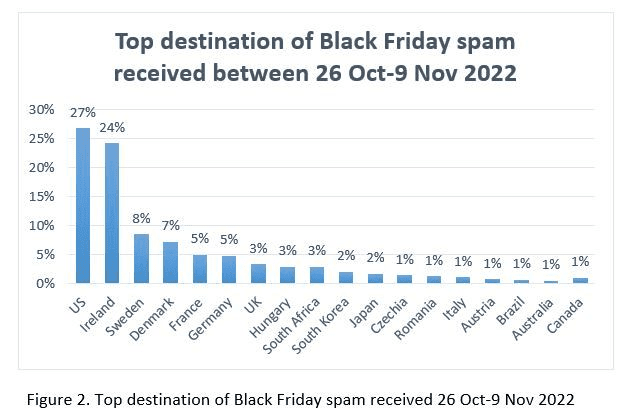
Black Friday and Cyber Monday, crooks are already at work
Black Friday and Cyber Monday, crooks are already at workEvery year during Black Friday and Cyber Monday, crooks take advantage of the bad habits of users...
Private Equity Exposed by Cyber-Hygiene Shortcomings
Private Equity Exposed by Cyber-Hygiene ShortcomingsFifth of portfolio companies feature "zero tolerance findings"Leer másFifth of portfolio companies feature "zero tolerance findings"
Security Affairs newsletter Round 394
Security Affairs newsletter Round 394A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs free for you in...
PoC exploit code for ProxyNotShell Microsoft Exchange bugs released online
PoC exploit code for ProxyNotShell Microsoft Exchange bugs released onlineProof-of-concept exploit code for two actively exploited Microsoft Exchange ProxyNotShell flaws released online. Proof-of-concept exploit code has...
DEV-0569 group uses Google Ads to distribute Royal Ransomware
DEV-0569 group uses Google Ads to distribute Royal RansomwareMicrosoft warns that a threat actor, tracked as DEV-0569, is using Google Ads to distribute the recently discovered...
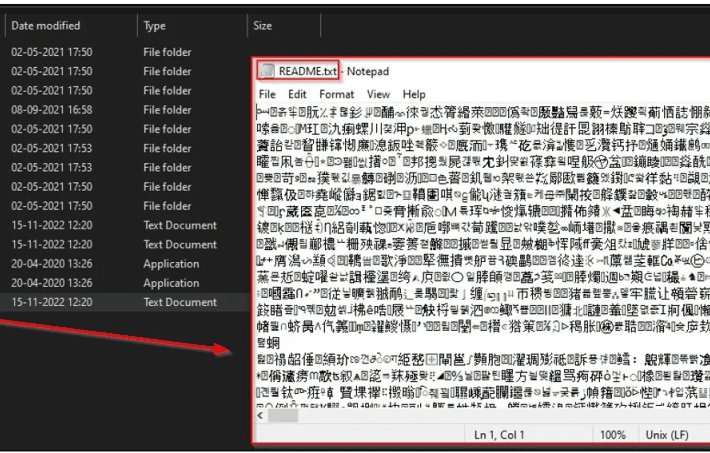
Octocrypt, Alice, and AXLocker Ransomware, new threats in the wild
Octocrypt, Alice, and AXLocker Ransomware, new threats in the wildExperts from Cyble Research and Intelligence Labs (CRIL) discovered three new ransomware families: AXLocker, Octocrypt, and Alice...
Google provides rules to detect tens of cracked versions of Cobalt Strike
Google provides rules to detect tens of cracked versions of Cobalt StrikeResearchers at Google Cloud identified 34 different hacked release versions of the Cobalt Strike tool...
Google won a lawsuit against the Glupteba botnet operators
Google won a lawsuit against the Glupteba botnet operatorsGoogle won a lawsuit filed against two Russian nationals involved in the operations of the Glupteba botnet. This...
Weekly Update 322
Weekly Update 322It's very strange to have gone 1,051 days without spending more than a few hours apart, but here we are... very temporarily: Only 15,501km...