Multiple High-Severity Flaws Affect Widely Used OpenLiteSpeed Web Server SoftwareMultiple high-severity flaws have been uncovered in the open source OpenLiteSpeed Web Server as well as its...
Day: November 16, 2022
Russian-Canadian National Charged Over Involvement in LockBit Ransomware Attacks
Russian-Canadian National Charged Over Involvement in LockBit Ransomware AttacksThe U.S. Department of Justice (DoJ) has announced charges against a dual Russian and Canadian national for his...
Experts Uncover Two Long-Running Android Spyware Campaigns Targeting Uyghurs
Experts Uncover Two Long-Running Android Spyware Campaigns Targeting UyghursTwo long-running surveillance campaigns have been found targeting the Uyghur community in China and elsewhere with Android spyware...
Malicious Google Play Store App Spotted Distributing Xenomorph Banking Trojan
Malicious Google Play Store App Spotted Distributing Xenomorph Banking TrojanGoogle has removed two new malicious dropper apps that have been detected on the Play Store for...
VPN vs. DNS Security
VPN vs. DNS SecurityWhen you are trying to get another layer of cyber protection that would not require a lot of resources, you are most likely...
New KmsdBot Malware Hijacking Systems for Mining Crypto and Launch DDoS Attacks
New KmsdBot Malware Hijacking Systems for Mining Crypto and Launch DDoS AttacksA newly discovered evasive malware leverages the Secure Shell (SSH) cryptographic protocol to gain entry...
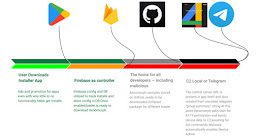
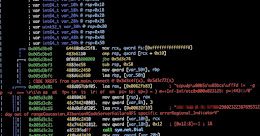
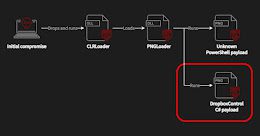
Worok Hackers Abuse Dropbox API to Exfiltrate Data via Backdoor Hidden in Images
Worok Hackers Abuse Dropbox API to Exfiltrate Data via Backdoor Hidden in ImagesA recently discovered cyber espionage group dubbed Worok has been found hiding malware in seemingly innocuous...
Global 2000 companies failing to adopt key domain security measures
Global 2000 companies failing to adopt key domain security measuresForbes Global 2000 companies are failing to adopt key domain security measures, exposing them to significant security...
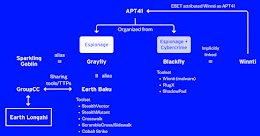
New “Earth Longzhi” APT Targets Ukraine and Asian Countries with Custom Cobalt Strike Loaders
New "Earth Longzhi" APT Targets Ukraine and Asian Countries with Custom Cobalt Strike LoadersEntities located in East and Southeast Asia as well as Ukraine have been...
Over 15,000 WordPress Sites Compromised in Malicious SEO Campaign
Over 15,000 WordPress Sites Compromised in Malicious SEO CampaignA new malicious campaign has compromised over 15,000 WordPress websites in an attempt to redirect visitors to bogus Q&A portals....
What is an External Penetration Test?
What is an External Penetration Test?A penetration test (also known as a pentest) is a security assessment that simulates the activities of real-world attackers to identify...
Researchers Say China State-backed Hackers Breached a Digital Certificate Authority
Researchers Say China State-backed Hackers Breached a Digital Certificate AuthorityA suspected Chinese state-sponsored actor breached a digital certificate authority as well as government and defense agencies...
Google to Pay $391 Million Privacy Fine for Secretly Tracking Users’ Location
Google to Pay $391 Million Privacy Fine for Secretly Tracking Users' LocationInternet giant Google has agreed to pay a record $391.5 million to settle with 40...
PCspooF: New Vulnerability Affects Networking Tech Used by Spacecraft and Aircraft
PCspooF: New Vulnerability Affects Networking Tech Used by Spacecraft and AircraftCredit: Marina Minkin A novel attack method has been disclosed against a crucial piece of technology called...
Cohesity previews AI-powered ransomware protection suite, Datahawk
Cohesity previews AI-powered ransomware protection suite, DatahawkBackup and data management vendor Cohesity has started to preview a new ransomware protection SaaS product called Datahawk, which leverages...
Researchers Reported Critical SQLi and Access Flaws in Zendesk Analytics Service
Researchers Reported Critical SQLi and Access Flaws in Zendesk Analytics ServiceCybersecurity researchers have disclosed details of now-patched flaws in Zendesk Explore that could have been exploited...
Deep Packet Inspection vs. Metadata Analysis of Network Detection & Response (NDR) Solutions
Deep Packet Inspection vs. Metadata Analysis of Network Detection & Response (NDR) SolutionsToday, most Network Detection and Response (NDR) solutions rely on traffic mirroring and Deep...
Warning: New RapperBot Campaign Aims to Launch DDoS Attacks at Game Servers
Warning: New RapperBot Campaign Aims to Launch DDoS Attacks at Game ServersCybersecurity researchers have unearthed new samples of malware called RapperBot that are being used to...
Google to Roll Out Privacy Sandbox Beta on Android 13 by Early 2023
Google to Roll Out Privacy Sandbox Beta on Android 13 by Early 2023Internet behemoth Google on Tuesday said it plans to roll out Privacy Sandbox for...
The Slippery Slope of Cyber Insurance: What Every MS(S)P Needs to Know
The Slippery Slope of Cyber Insurance: What Every MS(S)P Needs to Know Reduce Your Risk, Protect Yourself and Your Clients, and Build New Revenue As an...
Critical RCE Flaw Reported in Spotify’s Backstage Software Catalog and Developer Platform
Critical RCE Flaw Reported in Spotify's Backstage Software Catalog and Developer PlatformSpotify's Backstage has been discovered as vulnerable to a severe security flaw that could be...
Dangerous SIM-swap lockscreen bypass – update Android now!
Dangerous SIM-swap lockscreen bypass – update Android now!A bit like leaving the front door keys under the doormat...Leer másNaked SecurityA bit like leaving the front door...
S3 Ep108: You hid THREE BILLION dollars in a popcorn tin?
S3 Ep108: You hid THREE BILLION dollars in a popcorn tin?Patches, busts, leaks and why even low-likelihood exploits can be high-severity risks - listen now!Leer másNaked...
Log4Shell-like code execution hole in popular Backstage dev tool
Log4Shell-like code execution hole in popular Backstage dev toolGood old "string templating", also known as "string interpolation", in the spotlight again...Leer másNaked SecurityGood old "string templating",...
Unsupervised Machine Learning: Benefits for the Financial Services Industry
Unsupervised Machine Learning: Benefits for the Financial Services IndustryUnsupervised learning actually draws inferences from datasets without labels. It is best used if you want to find...
Quick Guide to Install SSL Certificate in RedHat Linux Server
Quick Guide to Install SSL Certificate in RedHat Linux ServerHere’s How You Can Install Your Purchased SSL Certificate in RedHat Linux Web Server RedHat is a...
“Gucci Master” business email scammer Hushpuppi gets 11 years
“Gucci Master” business email scammer Hushpuppi gets 11 yearsLearn how to protect yourself from big-money tricksters like the Hushpuppis of the world...Leer másNaked SecurityLearn how to...
China-Linked Cybercrime Group Attacks Asian Certificate Authority, Breaches Government Agencies
China-Linked Cybercrime Group Attacks Asian Certificate Authority, Breaches Government AgenciesChina-Linked Cybercrime Group Attacks Asian Certificate Authority, Breaches Government Agencies brooke.crothers Tue, 11/15/2022 - 15:14 8 views...
Kanye West Won a Grammy in 2006 for Anti-Semitism. Are You Really Surprised at Him Today?
Kanye West Won a Grammy in 2006 for Anti-Semitism. Are You Really Surprised at Him Today?Seems to me some obvious hate propaganda methods (even “fighting words”)...
Why Russian Hackers Fell Down and Ran Away When Ukraine Put Up Even a Little Defense
Why Russian Hackers Fell Down and Ran Away When Ukraine Put Up Even a Little DefenseThere’s an old bogus saw in IT that goes something like...