DAST tools as force multipliers for human cybersecurity skillsModern DAST tools help humans and technology work together at peak efficiency, allowing development and security teams to...
Day: November 16, 2022
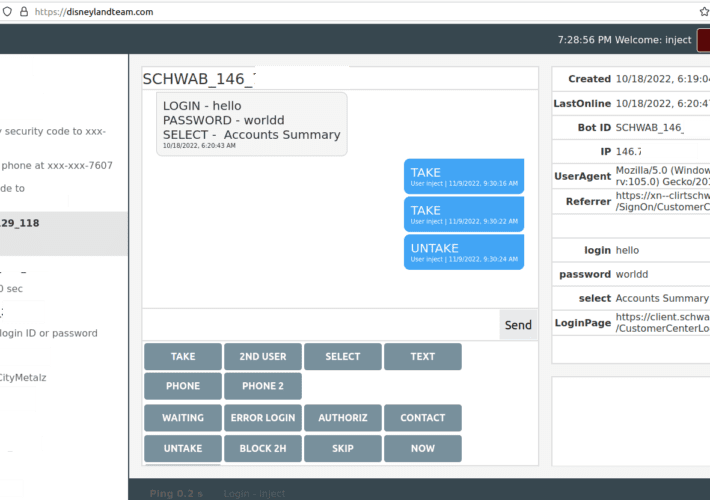
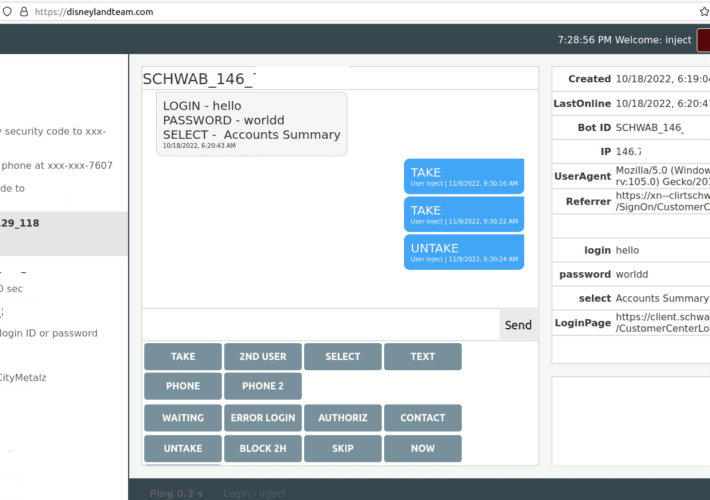
Disneyland Malware Team: It’s a Puny World After All
Disneyland Malware Team: It’s a Puny World After AllA financial cybercrime group calling itself the Disneyland Team has been making liberal use of visually confusing phishing...
Creating a culture of giving back
Creating a culture of giving back{{consumer="/components/cta/consumer"}} The team at the J.P. Morgan Corporate Challenge in 2015. It’s been almost two years since I moved from Boston...
Randall Munroe’s XKCD ‘Y2K And 2038’
Randall Munroe’s XKCD ‘Y2K And 2038’ via the comic artistry and dry wit of Randall Munroe, resident at XKCD! Permalink The post Randall Munroe’s XKCD ‘Y2K...
Why Cyber Risk in Critical Infrastructure Needs to be Understood and Prioritized
Why Cyber Risk in Critical Infrastructure Needs to be Understood and PrioritizedPart 1 of Axio’s multi-part series on cyber risk in critical infrastructure - why it’s...
Construction Firm Strengthens its ITDR Foundation with Purple Knight
Construction Firm Strengthens its ITDR Foundation with Purple KnightBetween remote users and contractors, construction company Maple Reinders needed to get control of Active Directory (AD) user...
Physical Threat Assessment: What to Know About the 2022 Qatar World Cup
Physical Threat Assessment: What to Know About the 2022 Qatar World CupFrom accusations of human rights abuses and corruption to negative reactions from religious extremists, the...
New Paradigm in Endpoint Protection
New Paradigm in Endpoint ProtectionDevice security has evolved over the last 10-20 years. With new devices (employee-owned smartphones) and new technologies (SaaS and the cloud), the...
Why Security & IT Teams in the Financial Industry Are Under Enormous Strain
Why Security & IT Teams in the Financial Industry Are Under Enormous StrainSecurity and IT teams in the financial services industry face incredible pressure to shore...
Researchers Discover Hundreds of Amazon RDS Instances Leaking Users’ Personal Data
Researchers Discover Hundreds of Amazon RDS Instances Leaking Users' Personal DataHundreds of databases on Amazon Relational Database Service (Amazon RDS) are exposing personal identifiable information (PII),...
7 Reasons to Choose an MDR Provider
7 Reasons to Choose an MDR ProviderAccording to a recent survey, 90% of CISOs running teams in small to medium-sized enterprises (SMEs) use a managed detection and...
Firefox fixes fullscreen fakery flaw – get the update now!
Firefox fixes fullscreen fakery flaw – get the update now!What's so bad about a web page going fullscreen without warning you first?Leer másNaked SecurityWhat's so bad...
Police dismantle pirated TV streaming network with 500,000 users
Police dismantle pirated TV streaming network with 500,000 usersThe Spanish police have dismantled a network of pirated streaming sites that illegally distributed content from 2,600 TV...
BSidesKC 2022 – Vincent Matteo’s ‘I Know What You Did Last Summer… I’m Still Hacking Your Small Business’
BSidesKC 2022 – Vincent Matteo’s ‘I Know What You Did Last Summer… I’m Still Hacking Your Small Business’Our sincere thanks to BSidesKC 2022 for publishing their...
Okta shares workaround for ongoing Microsoft 365 SSO outage
Okta shares workaround for ongoing Microsoft 365 SSO outageOkta, a leading provider of authentication services, has shared a workaround for ongoing issues preventing customers to log into...
Palo Alto releases PAN-OS 11.0 Nova with new evasive malware, injection attack protection
Palo Alto releases PAN-OS 11.0 Nova with new evasive malware, injection attack protectionPalo Alto Networks has announced PAN-OS 11.0 Nova, the latest version of its PAN-OS...
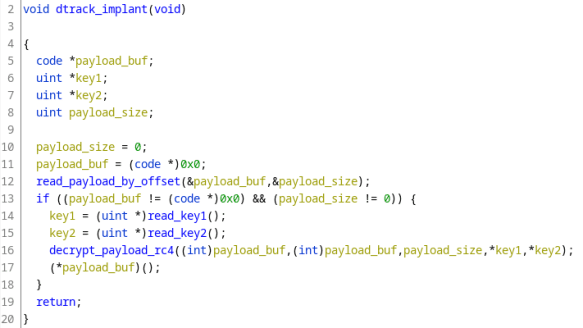
Lazarus APT uses DTrack backdoor in attacks against LATAM and European orgs
Lazarus APT uses DTrack backdoor in attacks against LATAM and European orgsNorth Korea-linked Lazarus APT is using a new version of the DTrack backdoor in attacks...
F5 fixed 2 high-severity Remote Code Execution bugs in its products
F5 fixed 2 high-severity Remote Code Execution bugs in its productsResearchers at cybersecurity firm Rapid7 have identified several vulnerabilities and other potential security issues affecting F5...
Heimdal® Publishes Biannual Threatscape Review
Heimdal® Publishes Biannual Threatscape ReviewAs part of our ongoing effort to stem the malignant tide of cybersecurity threats, we are proud to announce the publishing of...
Magento stores targeted in massive surge of TrojanOrders attacks
Magento stores targeted in massive surge of TrojanOrders attacksAt least seven hacking groups are behind a massive surge in 'TrojanOrders' attacks targeting Magento 2 websites, exploiting...
Disneyland Malware Team: It’s a Puny World After All
Disneyland Malware Team: It’s a Puny World After AllA financial cybercrime group calling itself the Disneyland Team has been making liberal use of visually confusing phishing...
Four Main Pillars Of Cloud Security
Four Main Pillars Of Cloud SecurityCloud migration led to cloud evolution which has led to a cloud-first mindset. With a pandemic push, global corporate enterprise has...
US govt: Iranian hackers breached federal agency using Log4Shell exploit
US govt: Iranian hackers breached federal agency using Log4Shell exploitThe FBI and CISA revealed in a joint advisory published today that an unnamed Iranian-backed threat group...
Threat Actors Taking Advantage of FTX Bankruptcy
Threat Actors Taking Advantage of FTX Bankruptcy Authored by Oliver Devane It hasn’t taken malicious actors long to take advantage of the recent bankruptcy filing of...
Microsoft’s Edge over Popups (and Google Chrome)
Microsoft’s Edge over Popups (and Google Chrome) Following up on our previous blog, How to Stop the Popups, McAfee Labs saw a sharp decrease in the...
Twitter source code indicates end-to-end encrypted DMs are coming
Twitter source code indicates end-to-end encrypted DMs are comingTwitter is reportedly working on finally adding end-to-end encryption (E2EE) for direct messages (DMs) exchanged between users on...
Suspected Zeus cybercrime ring leader ‘Tank’ arrested by Swiss police
Suspected Zeus cybercrime ring leader ‘Tank’ arrested by Swiss policeVyacheslav Igorevich Penchukov, also known as Tank and one of the leaders of the notorious JabberZeus cybercrime...
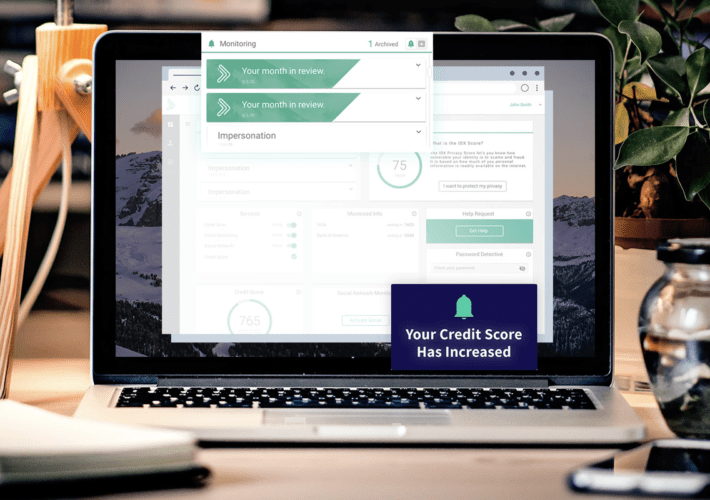
Get elite identity theft protection from a top-rated provider
Get elite identity theft protection from a top-rated providerPrevent cybercriminals from stealing your identity by acting on this great deal for IDX, which will monitor the...
Updated RapperBot malware targets game servers in DDoS attacks
Updated RapperBot malware targets game servers in DDoS attacksThe Mirai-based botnet 'RapperBot' has re-emerged via a new campaign that infects IoT devices for DDoS (Distributed Denial...
6 ways to keep your employees safe online in 2022
6 ways to keep your employees safe online in 2022By Anas Baig. With the increase in new technologies and remote working, workplace cyber security is more...