The Hacker Mind Podcast: Hacking High-Tech CarsVamosi: One of the unintended consequences of convenience is complexity. In order to make things easier to connect to more...
Day: November 10, 2022
What’s Next for Cybercrime in Australia?
What’s Next for Cybercrime in Australia?What’s Next for Cybercrime in Australia? Did you know, last year in Australia, a cybercrime was reported every eight minutes? Not...
Patch Tuesday Update – Nov 2022
Patch Tuesday Update – Nov 2022Well daylight savings time for much of the United States has arrived. Changing clocks is always a good reminder to do...
World Cup 2022: Watch out for scams
World Cup 2022: Watch out for scams In less than two weeks, the largest sporting event in the world will begin: The FIFA World Cup 2022....
The 247th United States Marine Corps Birthday: A Message From The Commandant Of The Marine Corps
The 247th United States Marine Corps Birthday: A Message From The Commandant Of The Marine Corps10 November 2022 A MESSAGE FROM THE COMMANDANT OF THE MARINE...
How can Digital Adoption Unlock Your Business’ Full Potential?
How can Digital Adoption Unlock Your Business’ Full Potential?Digital adoption can play a remarkable role in your business growth journey; but what is it, why is...
The 247th United States Marine Corps Birthday: A Message From The Commandant Of The Marine Corps
The 247th United States Marine Corps Birthday: A Message From The Commandant Of The Marine CorpsU.S. Marine Corps video by SSgt John Martinez, SSgt Aaron Patterson...
Fortanix unveils free DSM Explorer edition for managed data security
Fortanix unveils free DSM Explorer edition for managed data securityFortanix is offering a free tier for its data security manager software, aiming squarely at attracting new...
Why it’s time to review your Microsoft patch management options
Why it's time to review your Microsoft patch management optionsYou have several options to manage patching on Microsoft networks: let machines independently update or use a...
Rezilion expands SBOM to support Windows environments
Rezilion expands SBOM to support Windows environmentsSoftware security platform Rezilion has expanded its Dynamic Software Bill of Materials (SBOM) capability to support Windows environments. The firm...
Install Latest Windows Update ASAP! Patches Issued for 6 Actively Exploited Zero-Days
Install Latest Windows Update ASAP! Patches Issued for 6 Actively Exploited Zero-DaysMicrosoft's latest round of monthly security updates has been released with fixes for 68 vulnerabilities spanning its...
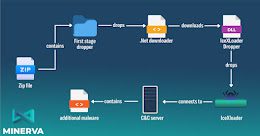
New IceXLoader Malware Loader Variant Infected Thousands of Victims Worldwide
New IceXLoader Malware Loader Variant Infected Thousands of Victims WorldwideAn updated version of a malware loader codenamed IceXLoader is suspected of having compromised thousands of personal and enterprise...
VMware Warns of 3 New Critical Flaws Affecting Workspace ONE Assist Software
VMware Warns of 3 New Critical Flaws Affecting Workspace ONE Assist SoftwareVMware has patched five security flaws affecting its Workspace ONE Assist solution, some of which could be...
Experts Warn of Browser Extensions Spying On Users via Cloud9 Chrome Botnet Network
Experts Warn of Browser Extensions Spying On Users via Cloud9 Chrome Botnet NetworkThe Keksec threat actor has been linked to a previously undocumented malware strain, which...
Top 5 API Security Myths That Are Crushing Your Business
Top 5 API Security Myths That Are Crushing Your BusinessThere are several myths and misconceptions about API security. These myths about securing APIs are crushing your...
GitHub releases new SDLC security features including private vulnerability reporting
GitHub releases new SDLC security features including private vulnerability reportingGitHub has announced new security features across its platform to help protect the software development lifecycle (SDLC)....
APT29 Exploited a Windows Feature to Compromise European Diplomatic Entity Network
APT29 Exploited a Windows Feature to Compromise European Diplomatic Entity NetworkThe Russia-linked APT29 nation-state actor has been found leveraging a "lesser-known" Windows feature called Credential Roaming...
Several Cyber Attacks Observed Leveraging IPFS Decentralized Network
Several Cyber Attacks Observed Leveraging IPFS Decentralized NetworkA number of phishing campaigns are leveraging the decentralized InterPlanetary Filesystem (IPFS) network to host malware, phishing kit infrastructure,...
Re-Focusing Cyber Insurance with Security Validation
Re-Focusing Cyber Insurance with Security ValidationThe rise in the costs of data breaches, ransomware, and other cyber attacks leads to rising cyber insurance premiums and more...
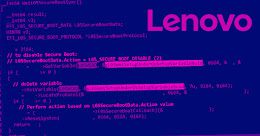
New UEFI Firmware Flaws Reported in Several Lenovo Notebook Models
New UEFI Firmware Flaws Reported in Several Lenovo Notebook ModelsPC maker Lenovo has addressed yet another set of three shortcomings in the Unified Extensible Firmware Interface...
Researchers show techniques for malware persistence on F5 and Citrix load balancers
Researchers show techniques for malware persistence on F5 and Citrix load balancersOver the past several years, hackers have targeted public-facing network devices such as routers, VPN...
High-Severity Flaw Reported in Critical System Used by Oil and Gas Companies
High-Severity Flaw Reported in Critical System Used by Oil and Gas CompaniesCybersecurity researchers have disclosed details of a new vulnerability in a system used across oil...
Malicious Package on PyPI Hides Behind Image Files, Spreads Via GitHub
Malicious Package on PyPI Hides Behind Image Files, Spreads Via GitHubThe findings indicate that PyPI malicious packages and their obfuscation techniques are evolvingLeer másThe findings indicate...
Citrix Issues Patches for Critical Flaw Affecting ADC and Gateway Products
Citrix Issues Patches for Critical Flaw Affecting ADC and Gateway ProductsCitrix has released security updates to address a critical authentication bypass flaw in the application delivery controller (ADC)...
5 Tips to Secure a Windows Environment
5 Tips to Secure a Windows EnvironmentBecause Microsoft Windows is such a key component of so many enterprise and development environments, securing the platform is vital...
Exchange 0-days fixed (at last) – plus 4 brand new Patch Tuesday 0-days!
Exchange 0-days fixed (at last) – plus 4 brand new Patch Tuesday 0-days!In all the excitement, we kind of lost track ourselves. Were there six 0-days,...
High-Risk Vulnerability Found in ABB’s Flow Computers
High-Risk Vulnerability Found in ABB's Flow ComputersAttackers could exploit it by sending a specially crafted message to an affected system nodeLeer másAttackers could exploit it by...
Emergency code execution patch from Apple – but not an 0-day
Emergency code execution patch from Apple – but not an 0-dayNot a zero-day, but important enough for a quick-fire patch to one system library...Leer másNaked SecurityNot...
Space Force CIO Calls for Greater Collaboration, Secure Commercial Software
Space Force CIO Calls for Greater Collaboration, Secure Commercial Software Whether it’s our navigation systems or systems that manage our everyday communications, the modern world is...
Okta streamlines IAM portfolio with consumer identity management cloud
Okta streamlines IAM portfolio with consumer identity management cloudPotential access management customers got a new option from Okta Wednesday, as the identity and access management (IAM)...