Endpoint Protection is Key When it Comes to Cyber InsuranceWhy is endpoint detection and response (EDR) considered non-negotiable for companies seeking catastrophic coverage for cyber incidents...
Day: November 7, 2022
Live Webinar | Identity Security as a Transformation Accelerant in the Insurance Sector
Live Webinar | Identity Security as a Transformation Accelerant in the Insurance SectorContenido de la entradaLeer másDataBreachToday.com RSS Syndication
Getting Started with NSX Application Platform (NAPP)
Getting Started with NSX Application Platform (NAPP)Introducing the platform The NSX Application Platform (NAPP) is a high-performance security analytics platform that hosts microservices-based applications (Figure 1.1)....
Medibank Says No to Paying Hacker’s Extortion Demand
Medibank Says No to Paying Hacker's Extortion DemandGroup Claiming Affiliation With REvil Threatens to Release DataEmbattled Australian private health insurer Medibank says it won't pay hackers'...
Medibank says it won’t pay ransom for customer data stolen in cyber-attack
Medibank says it won’t pay ransom for customer data stolen in cyber-attack‘Limited chance’ such a move would result in return of data or prevent it being...
SHARED INTEL: The non-stop advance and diversification of ransomware extortion tactics
SHARED INTEL: The non-stop advance and diversification of ransomware extortion tacticsCybercriminals are becoming more creative as cybersecurity analysts adapt quickly to new ransomware strategies. Related: How...
6 ways to reduce your IoT attack surface
6 ways to reduce your IoT attack surfaceAs attackers target the ever-growing IoT attack surface, companies can reduce their risks with these six security best practices....
A Guide to Remove Malware From Your iPhone
A Guide to Remove Malware From Your iPhone Malicious software, or “malware,” refers to any program designed to infect and disrupt computer systems and networks. The...
What Is Encrypted DNS Traffic?
What Is Encrypted DNS Traffic?Encrypted DNS traffic is a type of DNS traffic secured in a way that no third party can intervene during a DNS...
Twitter $8 Fee Exploited by Cybercriminals
Twitter $8 Fee Exploited by CybercriminalsAs Elon Musk took charge of Twitter`s management, there have been some controversial changes implemented, one of them being the $8 a...
RomCom RAT campaigns abuses popular brands like KeePass and SolarWinds NPM
RomCom RAT campaigns abuses popular brands like KeePass and SolarWinds NPMA new campaign spreading RomCom RAT impersonates popular software brands like KeePass, and SolarWinds. The threat...
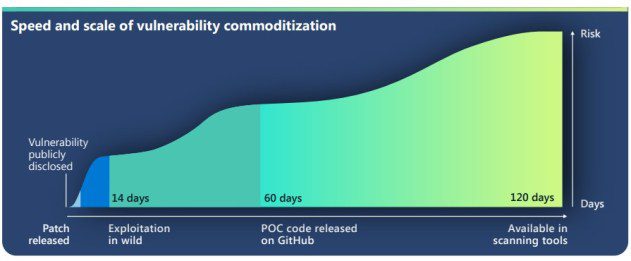
Zero-day are exploited on a massive scale in increasingly shorter timeframes
Zero-day are exploited on a massive scale in increasingly shorter timeframesMicrosoft warns of an uptick among threat actors increasingly using publicly-disclosed zero-day exploits in their attacks....
The Role of Cybersecurity in Accounting
The Role of Cybersecurity in AccountingIt comes as no surprise that cybersecurity is one of the most important topics in this hacker-prone Internet era. A large...
29 malicious PyPI packages spotted delivering the W4SP Stealer
29 malicious PyPI packages spotted delivering the W4SP StealerCybersecurity researchers discovered 29 malicious PyPI packages delivering the W4SP stealer to developers’ systems. Cybersecurity researchers have discovered...
All UK Hosted Internet Devices Will be Scanned by the British Government
All UK Hosted Internet Devices Will be Scanned by the British GovernmentThe United Kingdom’s National Cyber Security Centre (NCSC), the government agency leading UK’s cybersecurity mission,...
A cyberattack blocked the trains in Denmark
A cyberattack blocked the trains in DenmarkAt the end of October, a cyber attack caused the trains to stop in Denmark, the attack hit a third-party...
Robin Banks Relocated to a Russian Server
Robin Banks Relocated to a Russian ServerThe cybercriminals behind Robin Bank have relocated the phishing-as-a-service (PhaaS) platform to a Russian hosting service. DDoS-Guard takes over from...
Security Affairs newsletter Round 392
Security Affairs newsletter Round 392A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs free for you in...
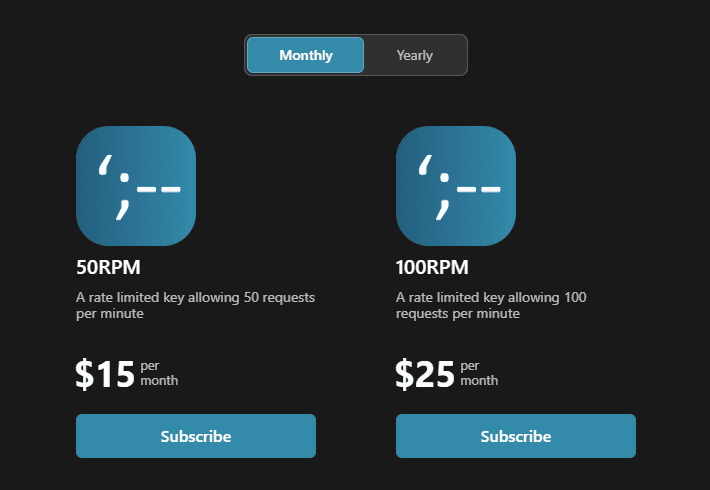
The Have I Been Pwned API Now Has Different Rate Limits and Annual Billing
The Have I Been Pwned API Now Has Different Rate Limits and Annual BillingA couple of weeks ago I wrote about some big changes afoot for...
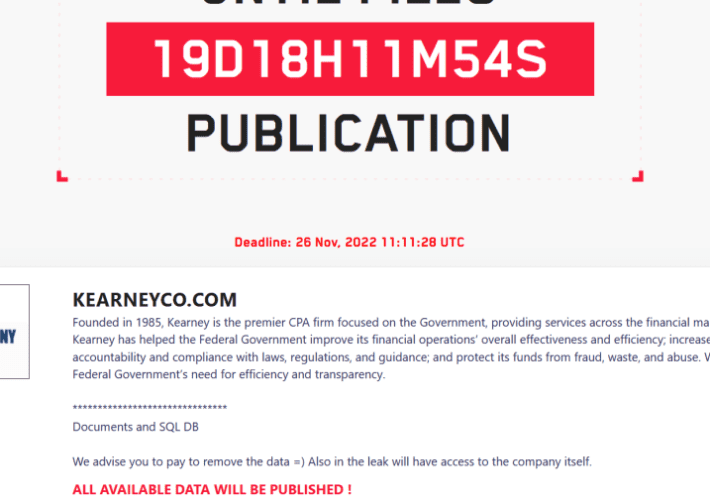
LockBit 3.0 gang claims to have stolen data from Kearney & Company
LockBit 3.0 gang claims to have stolen data from Kearney & CompanyThe ransomware group LockBit claimed to have stolen data from consulting and IT services provider...
FBI: Beware of Cyber-Threat from Russian Hacktivists
FBI: Beware of Cyber-Threat from Russian HacktivistsFeds claim DDoS attacks are being aimed at critical infrastructureLeer másFeds claim DDoS attacks are being aimed at critical infrastructure
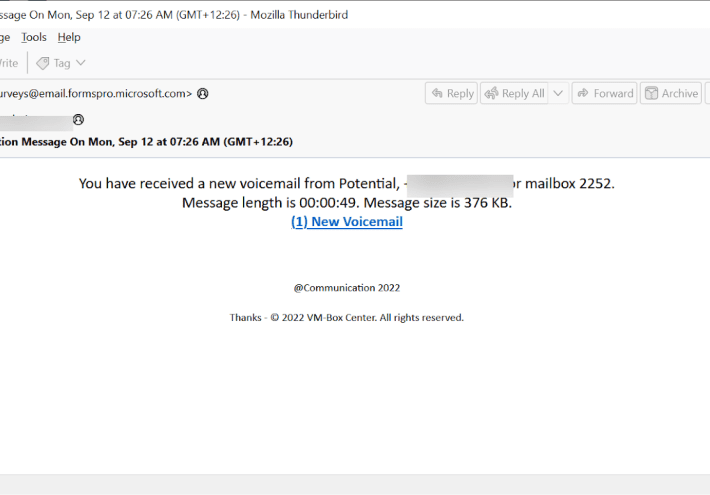
Abusing Microsoft Dynamics 365 Customer Voice in phishing attacks
Abusing Microsoft Dynamics 365 Customer Voice in phishing attacksResearchers uncovered a campaign abusing Microsoft Dynamics 365 customer voice to steal credentials from the victims. Microsoft’s Dynamics...
UK NCSC govt agency is scanning the Internet for flawed devices in the UK
UK NCSC govt agency is scanning the Internet for flawed devices in the UKThe UK National Cyber Security Centre (NCSC) announced that is scanning all Internet-exposed...
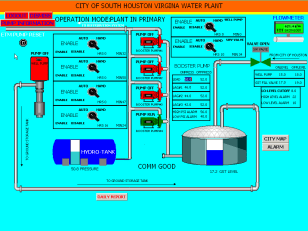
Water sector in the US and Israel still unprepared to defeat cyber attacks
Water sector in the US and Israel still unprepared to defeat cyber attacksExpert warns that the US and Israel are still unprepared to defeat a cyber...
ICO: Department for Education Should Have Been Fined £10m
ICO: Department for Education Should Have Been Fined £10mDfE oversight leads to misuse of data on 28 million childrenLeer másDfE oversight leads to misuse of data...
BSidesPDX 2022 – Ben Kendall’s ‘Breaking Into Infosec Or, How I Hacked My Way Out Of Poverty’
BSidesPDX 2022 – Ben Kendall’s ‘Breaking Into Infosec Or, How I Hacked My Way Out Of Poverty’Our sincere thanks to BSidesPDX 2022 for publishing their outstanding...
BSidesPDX 2022 – Nate Norton’s ‘Live, Laugh, Lyrical Injection: Hacking Karaoke For Fun And Profit’
BSidesPDX 2022 – Nate Norton’s ‘Live, Laugh, Lyrical Injection: Hacking Karaoke For Fun And Profit’BSidesPDX 2022 – Nate Norton’s ‘Live, Laugh, Lyrical Injection: Hacking Karaoke For...
LinkedIn Adds Verified Emails, Profile Creation Dates
LinkedIn Adds Verified Emails, Profile Creation DatesLinkedIn Adds Verified Emails, Profile Creation Dates For whatever reason, the majority of the phony LinkedIn profiles reviewed by this...
Cybersecurity Insights with Contrast SVP of Cyber Strategy Tom Kellermann | 11/4
Cybersecurity Insights with Contrast SVP of Cyber Strategy Tom Kellermann | 11/4Cybersecurity Insights with Contrast SVP of Cyber Strategy Tom Kellermann | 11/4 Insight #1 "...
Tesla and Twitter Should be Banned as Threats to Global Security
Tesla and Twitter Should be Banned as Threats to Global SecurityTesla and Twitter Should be Banned as Threats to Global Security As you may remember, I’ve...