Business Email Compromise: Low-Tech, High-Impact Threat One of the least technologically sophisticated cyberattacks, business email compromise (BEC), is also one of the most damaging. According to...
Day: November 7, 2022
CISOs, Security Leaders Eyeing Other Job Options
CISOs, Security Leaders Eyeing Other Job Options Nearly a third of CISOs or IT security leaders in the United States and the United Kingdom are considering...
How DevOps Drive Business Growth?
How DevOps Drive Business Growth?The world of information technology is constantly advancing. As time passes, technological tools, trends, and usage behavior change. Integration of DevOps within...
Safely Test Your Malware, Ransomware and Virus Defenses
Safely Test Your Malware, Ransomware and Virus Defenses What’s the best way for a company to test its malware defenses in real-life scenarios? The past few...
Episode 3
Episode 3Cyborg Security is launching a podcast with a twist! Join us for the first fully interactive threat hunting podcast where you can hang out with...
BSidesPDX 2022 – Devin Gaffney’s ‘Reverse Engineering: How WAFs (Fail To) Identify Bots’
BSidesPDX 2022 – Devin Gaffney’s ‘Reverse Engineering: How WAFs (Fail To) Identify Bots’Our sincere thanks to BSidesPDX 2022 for publishing their outstanding conference videos on the...
Medibank Refuses to Pay Ransom After 9.7 Million Customers Exposed in Ransomware Hack
Medibank Refuses to Pay Ransom After 9.7 Million Customers Exposed in Ransomware HackAustralian health insurer Medibank today confirmed that personal data belonging to around 9.7 million...
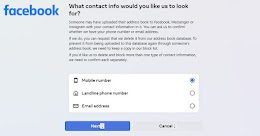
This Hidden Facebook Tool Lets Users Remove Their Email or Phone Number Shared by Others
This Hidden Facebook Tool Lets Users Remove Their Email or Phone Number Shared by OthersFacebook appears to have silently rolled out a tool that allows users...
Ukraine’s Response to Cyber Threats a Model in DDoS Prevention
Ukraine’s Response to Cyber Threats a Model in DDoS PreventionWith the disruption, loss of life and heartbreaking images that the Russia-Ukraine conflict has produced, it is...
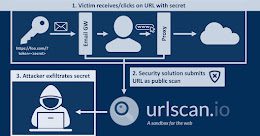
Experts Find URLScan Security Scanner Inadvertently Leaks Sensitive URLs and Data
Experts Find URLScan Security Scanner Inadvertently Leaks Sensitive URLs and DataSecurity researchers are warning of "a trove of sensitive information" leaking through urlscan.io, a website scanner for...
Island-hopping attacks | Brand protection in an era of island hopping | Contrast Security
Island-hopping attacks | Brand protection in an era of island hopping | Contrast Security How many vulnerabilities are lurking, ready to boobytrap your apps and lay...
Public URL scanning tools – when security leads to insecurity
Public URL scanning tools – when security leads to insecurityNever make your users cry/By how you use an APILeer másNaked SecurityNever make your users cry/By how...
Voices from Validate – Simplifying Posture Management
Voices from Validate – Simplifying Posture ManagementLearn from Zscaler how zero trust, MITRE ATT&CK, and BAS can work together to optimize security posture across complex environments....
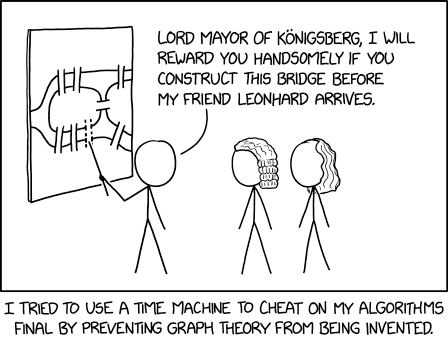
Randall Munroe’s XKCD ‘Königsberg’
Randall Munroe’s XKCD ‘Königsberg’ via the comic artistry and dry wit of Randall Munroe, resident at XKCD! Permalink The post Randall Munroe’s XKCD ‘Königsberg’ appeared first...
Cyber Insurance Market Stabilizing as Security Awareness Improves
Cyber Insurance Market Stabilizing as Security Awareness ImprovesThe cyber insurance market is beginning to stabilize following several years of steep rate increases, according to a recent...
Android RAT Group Targets Indian Defense Personnel
Android RAT Group Targets Indian Defense PersonnelThe app asked for several permissions, including camera, microphone, internet and storageLeer másThe app asked for several permissions, including camera,...
Medibank Refuses to Pay Ransom After Data Breach
Medibank Refuses to Pay Ransom After Data BreachMedibank believes there is a limited chance paying a ransom would return customers' dataLeer másMedibank believes there is a...
Continental, the Newest Victim of LockBit Ransomware
Continental, the Newest Victim of LockBit RansomwareLockBit, one of the most notorious ransomware gangs around, is claiming responsibility for a cyberattack that hit the German auto...
Robin Banks phishing-as-a-service platform continues to evolve
Robin Banks phishing-as-a-service platform continues to evolveThe phishing-as-a-service (PhaaS) platform Robin Banks migrated its infrastructure to DDoS-Guard, a Russian bulletproof hosting service. The phishing-as-a-service (PhaaS) platform Robin...
American and Israeli Water Sectors Are Unprepared for Cyber Attacks
American and Israeli Water Sectors Are Unprepared for Cyber AttacksFormer Israeli Air Force captain Ariel Stern warns that the US and Israel are currently unprepared to...
Black Basta Ransomware Attack Detection: Recent Malicious Campaigns Using New Custom Tools Attributed to the FIN7 Group
Black Basta Ransomware Attack Detection: Recent Malicious Campaigns Using New Custom Tools Attributed to the FIN7 Group The Black Basta ransomware group emerged in the cyber...
Medibank refuses to pay ransom after 9.7 million health insurance customers have their data stolen
Medibank refuses to pay ransom after 9.7 million health insurance customers have their data stolenEmbattled Australian health insurer Medibank says that it will not pay a...
The Conviction of Uber’s Chief Security Officer
The Conviction of Uber’s Chief Security OfficerI have been meaning to write about Joe Sullivan, Uber’s former Chief Security Officer. He was convicted of crimes related...
Mastodon now has over 1 million users amid Twitter tensions
Mastodon now has over 1 million users amid Twitter tensionsMastodon, the free, open-source, decentralized micro-blogging social media platform, has surpassed a million monthly active users for...
How Cyberbullying Looks In Australia in 2022
How Cyberbullying Looks In Australia in 2022 There’s no doubt that cyber bullying ranks towards the top of most parents ‘worry list’. As a mum of...
Ransomware gang threatens to release stolen Medibank data
Ransomware gang threatens to release stolen Medibank dataA ransomware gang that some believe is a relaunch of REvil and others track as BlogXX has claimed responsibility...
Massive Phishing Campaigns Target India Banks’ Clients
Massive Phishing Campaigns Target India Banks’ ClientsWe found five banking malware families targeting customers of seven banks in India to steal personal and credit card information...
Maple Leaf Foods suffers outage following weekend cyberattack
Maple Leaf Foods suffers outage following weekend cyberattackMaple Leaf Foods confirmed on Sunday that it experienced a cybersecurity incident causing a system outage and disruption of...
Microsoft WinGet package manager failing due to CDN issues
Microsoft WinGet package manager failing due to CDN issuesMicrosoft's WinGet package manager is currently having problems installing or upgrading packages due to the Azure Content Delivery Network...
Key challenges of shift-left tactics
Key challenges of shift-left tacticsBy Musa Nadir Sani. Software development has continued to evolve over the years, with developers pushing to release applications in the shortest...