The Week in Security: OpenSSL danger downgraded but still real, GitHub exposed Welcome to the latest edition of The Week in Security, which brings you the...
Day: November 4, 2022
Security Awareness Needs a New Experience, Not More New Content
Security Awareness Needs a New Experience, Not More New ContentIf you are shopping for a security awareness vendor, you have Netflix-style variety at your fingertips. The...
BSidesPDX 2022 – Ken Westin’s ‘Opening Remarks’
BSidesPDX 2022 – Ken Westin’s ‘Opening Remarks’Our sincere thanks to BSidesPDX 2022 for publishing their outstanding conference videos on the organization's YouTube channel. Permalink The post...
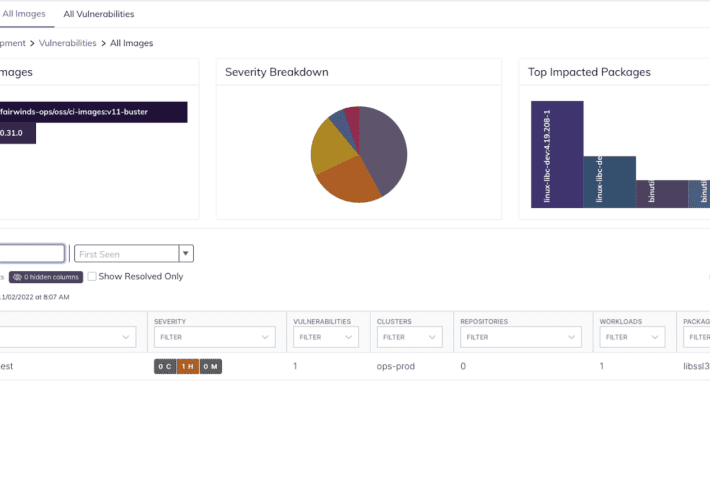
CVE-2022-3602 and CVE-2022-3786 OpenSSL Vulnerabilities: Scanning Container Images
CVE-2022-3602 and CVE-2022-3786 OpenSSL Vulnerabilities: Scanning Container Images On November 1st, 2022, OpenSSL announced a pair of High Severity vulnerabilities in version 3.0.0-3.0.6 of OpenSSL. The...
Analyzing CISA Known Exploited Vulnerabilities with Business Context
Analyzing CISA Known Exploited Vulnerabilities with Business ContextWhat is CISA Directive BOD 22-01? In November 2021, the US Cybersecurity and Infrastructure Security Agency (CISA), an agency...
What You Need to Know About SBOM Generation Tools
What You Need to Know About SBOM Generation ToolsWhen it comes to tools for generating a software bill of materials (SBOM), organizations basically have three options:...
Zurich and Mondelez Reach NotPetya Settlement, but Cyber-Risk May Increase
Zurich and Mondelez Reach NotPetya Settlement, but Cyber-Risk May IncreaseThe parties have mutually resolved the matter, but details of the settlement were not providedLeer másThe parties...
RomCom Weaponized KeePass and SolarWinds Instances to Target Ukraine, Maybe UK
RomCom Weaponized KeePass and SolarWinds Instances to Target Ukraine, Maybe UKThe discovery comes from the BlackBerry Research & Intelligence TeamLeer másThe discovery comes from the BlackBerry...
Five Tips for Low-Friction Authentication
Five Tips for Low-Friction Authentication Authentication processes often introduce unwelcome friction into the user experience. Generally speaking, friction equates to the effort needed from the end...
How can Identity Verification prevent scams in MLM and D2C industries?
How can Identity Verification prevent scams in MLM and D2C industries?In India, there have been several Multi-Level-Marketing (MLM) frauds. Investing in stock shares and commodities, paid...
Researchers Find Links b/w Black Basta Ransomware and FIN7 Hackers
Researchers Find Links b/w Black Basta Ransomware and FIN7 HackersA new analysis of tools put to use by the Black Basta ransomware operation has identified ties...
CISA Warns of Critical Vulnerabilities in 3 Industrial Control System Software
CISA Warns of Critical Vulnerabilities in 3 Industrial Control System SoftwareThe U.S. Cybersecurity and Infrastructure Security Agency (CISA) has published three Industrial Control Systems (ICS) advisories about multiple...
TikTok Confirms Chinese Staff Can Access UK and EU User Data
TikTok Confirms Chinese Staff Can Access UK and EU User DataThe news comes from the social media giant’s head of privacy in Europe, Elaine FoxLeer másThe...
S3 Ep107: Eight months to kick out the crooks and you think that’s GOOD? [Audio + Text]
S3 Ep107: Eight months to kick out the crooks and you think that’s GOOD? [Audio + Text]Listen now - latest episode - audio plus full transcriptLeer...
Cyber Threat Landscape Shaped by Ukraine Conflict, ENISA Report Reveals
Cyber Threat Landscape Shaped by Ukraine Conflict, ENISA Report RevealsThe EU cybersecurity agency released its 10th annual threat landscape report on November 3, 2022Leer másThe EU...
What is an Organization Validation (OV) Code Signing Certificate?
What is an Organization Validation (OV) Code Signing Certificate?An organization must utilize an OV Code Signing Certificate whenever it releases any software. However, many firms are...
Espionage campaign loads VPN spyware on Android devices via social media
Espionage campaign loads VPN spyware on Android devices via social mediaA new espionage campaign, dubbed SandStrike, has been detected using malicious VPN apps to load spyware...
Mondelez and Zurich’s NotPetya cyber-attack insurance settlement leaves behind no legal precedent
Mondelez and Zurich’s NotPetya cyber-attack insurance settlement leaves behind no legal precedentMultinational food and beverage company Mondelez International and Zurich American Insurance have settled their multiyear...
250+ U.S. news sites spotted spreading FakeUpdates malware in a supply-chain attack
250+ U.S. news sites spotted spreading FakeUpdates malware in a supply-chain attackThreat actors compromised a media company to deliver FakeUpdates malware through the websites of hundreds...
World’s Most Expensive Observatory Floored by Cyber-Attack
World's Most Expensive Observatory Floored by Cyber-AttackALMA suspends astronomical observationsLeer másALMA suspends astronomical observations
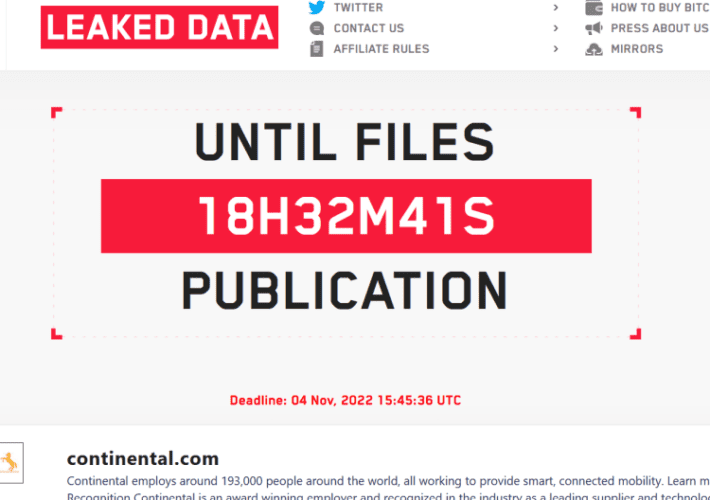
LockBit ransomware gang claims the hack of Continental automotive group
LockBit ransomware gang claims the hack of Continental automotive groupThe LockBit ransomware group claimed to have hacked the multinational automotive group Continental and threatens to leak...
The future starts now: 10 major challenges facing cybersecurity
The future starts now: 10 major challenges facing cybersecurityTo mark Antimalware Day, we’ve rounded up some of the most pressing issues for cybersecurity now and in the...
Phishers Abuse Microsoft Voicemail Service to Trick Users
Phishers Abuse Microsoft Voicemail Service to Trick UsersAvanan spots campaign leveraging Dynamic 365 Customer VoiceLeer másAvanan spots campaign leveraging Dynamic 365 Customer Voice
Cisco addressed several high-severity flaws in its products
Cisco addressed several high-severity flaws in its productsCisco addressed multiple flaws impacting its products, including high-severity issues in identity, email, and web security solutions. Cisco addressed...
Defining Operational Threat Intelligence
Defining Operational Threat IntelligenceWe previously talked about the advantages and implications of strategic threat intelligence, which sheds light on cyberattackers’ goals. This type of intelligence is non-technical,...
Emotet botnet starts blasting malware again after 4 month break
Emotet botnet starts blasting malware again after 4 month breakThe Emotet malware operation is again spamming malicious emails after almost a four-month "vacation" that saw little activity...
Crimson Kingsnake Gang Uses BEC Attacks to Impersonate Law Firms
Crimson Kingsnake Gang Uses BEC Attacks to Impersonate Law FirmsA new group called “Crimson Kingsnake” is on the rise. The group is making use of business...
The 10th edition of the ENISA Threat Landscape (ETL) report is out!
The 10th edition of the ENISA Threat Landscape (ETL) report is out!I’m proud to announce the release of the 10th edition of the ENISA Threat Landscape...
Weekly Update 320
Weekly Update 320I feel like life is finally complete: I have beaches, sunshine and fast internet! (Yes, and of course an amazing wife, but that goes...
Supply-Chain Attack Compromises Hundreds of U.S. News Websites
Supply-Chain Attack Compromises Hundreds of U.S. News WebsitesMore than 250 regional and national US newspaper sites have fallen victim to a supply chain attack and are now...