14 All Day DevOps (ADDO) Sessions You Won’t Want to Miss The post 14 All Day DevOps (ADDO) Sessions You Won’t Want to Miss appeared...
Day: November 2, 2022
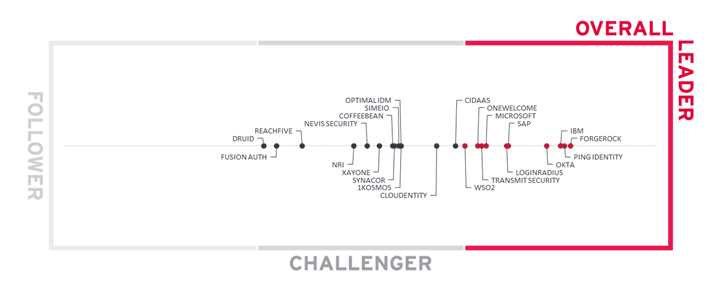
The Road to Passwordless is Paved with Orchestration
The Road to Passwordless is Paved with OrchestrationA new report from KuppingerCole Names ForgeRock an Overall Leader in Passwordless Authentication If passwordless authentication is a destination,...
BSidesLV 2022 Lucky13 I Am The Cavalry (IATC) – Allan Friedman’s, Adam Kojak’s, Katie Bratman’s, Chris Gates’ ‘#SBOM Is Here: Making Progress (Not Excuses)’
BSidesLV 2022 Lucky13 I Am The Cavalry (IATC) – Allan Friedman’s, Adam Kojak’s, Katie Bratman’s, Chris Gates’ ‘#SBOM Is Here: Making Progress (Not Excuses)’Our sincere thanks...
Security Advisory for OpenSSL Vulnerabilities CVE-2022-3602 & CVE-2022-3786
Security Advisory for OpenSSL Vulnerabilities CVE-2022-3602 & CVE-2022-3786Background On 01-Nov-2022, OpenSSL published an advisory about two high-severity security flaws - CVE-2022-3786 (“X.509 Email Address Variable Length...
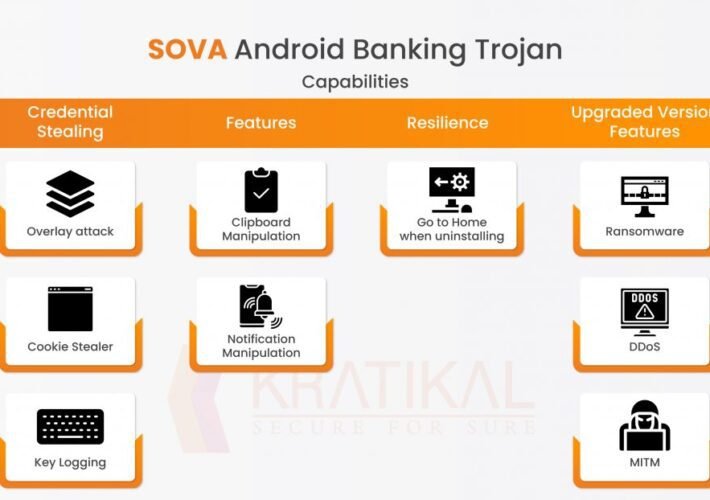
SOVA – A New Android Banking Trojan
SOVA – A New Android Banking TrojanIntroduction How many people are aware of the new mobile banking “Trojan Virus -SOVA” that enables hackers to access legitimate...
OpenSSL Releases Patch for 2 New High-Severity Vulnerabilities
OpenSSL Releases Patch for 2 New High-Severity VulnerabilitiesThe OpenSSL project has rolled out fixes to contain two high-severity flaws in its widely used cryptography library that...
Dropbox admits 130 of its private GitHub repos were copied after phishing attack
Dropbox admits 130 of its private GitHub repos were copied after phishing attackPersonal info and data safe, stolen code not critical, apparently Dropbox has said it...
OpenSSL patches are out – CRITICAL bug downgraded to HIGH, but patch anyway!
OpenSSL patches are out – CRITICAL bug downgraded to HIGH, but patch anyway!That bated-breath OpenSSL update is out! It's no longer rated CRITICAL, but we advise you...
Complete Guide on Comodo Code Signing Certificate
Complete Guide on Comodo Code Signing CertificateComodo is a cybersecurity solutions provider helping businesses and individuals stay protected from all sorts of cyber threats. It provides...
Ritz cracker giant settles bust-up with insurer over $100m+ NotPetya cleanup
Ritz cracker giant settles bust-up with insurer over $100m+ NotPetya cleanupDeal could 'upend the entire cyber-insurance ecosystem and make it almost impossible to get meaningful cyber...
OpenSSL project patches two vulnerabilities but downgrades severity
OpenSSL project patches two vulnerabilities but downgrades severityThe OpenSSL project released a patch for two high severity vulnerabilities in the world’s most widely used cryptographic library....
The spy who rented to me? Throwing the spotlight on hidden cameras in Airbnbs
The spy who rented to me? Throwing the spotlight on hidden cameras in AirbnbsDo you find reports of spy cams found in vacation rentals unsettling? Try...
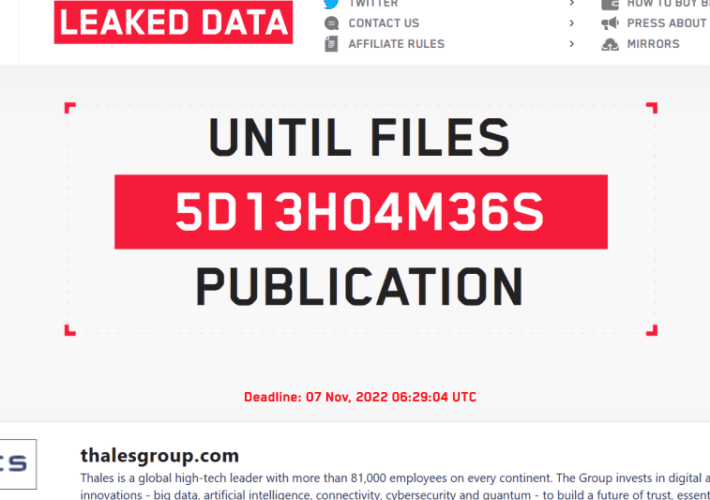
LockBit 3.0 gang claims to have stolen data from Thales
LockBit 3.0 gang claims to have stolen data from ThalesThe ransomware group LockBit 3.0 claimed to have stolen data from the French defence and technology group...
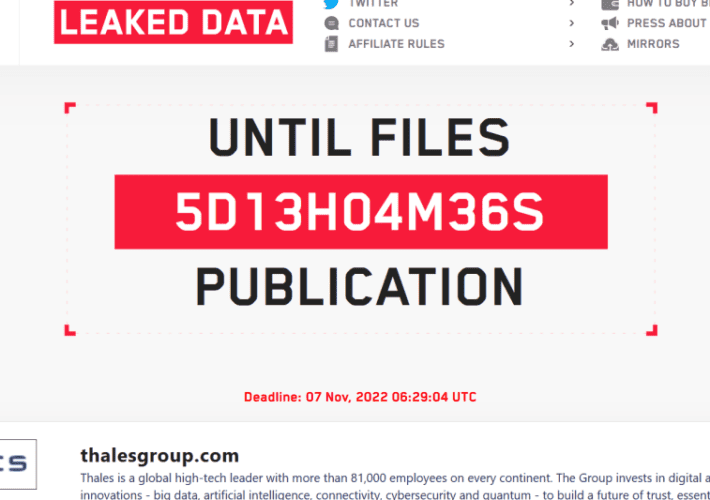
LockBit 3.0 gang claims to have stolen data from Thales
LockBit 3.0 gang claims to have stolen data from ThalesThe ransomware group LockBit 3.0 claimed to have stolen data from the French defence and technology group...
OpenSSL fixed two high-severity vulnerabilities
OpenSSL fixed two high-severity vulnerabilitiesThe OpenSSL project fixed two high-severity flaws in its cryptography library that can trigger a DoS condition or achieve remote code execution....
OpenSSL fixed two high-severity vulnerabilities
OpenSSL fixed two high-severity vulnerabilitiesThe OpenSSL project fixed two high-severity flaws in its cryptography library that can trigger a DoS condition or achieve remote code execution....
Latest on OpenSSL 3.0.7 Bug & Security-Fix
Latest on OpenSSL 3.0.7 Bug & Security-FixPotential disruptions following vulnerabilities found in OpenSSL.Leer másTrend Micro Research, News, PerspectivesPotential disruptions following vulnerabilities found in OpenSSL.
Malicious Android apps with 1M+ installs found on Google Play
Malicious Android apps with 1M+ installs found on Google PlayA set of four malicious applications currently available in Google Play, the official store for the Android...
Dropbox discloses breach after hacker stole 130 GitHub repositories
Dropbox discloses breach after hacker stole 130 GitHub repositoriesDropbox disclosed a security breach after threat actors stole 130 code repositories after gaining access to one of...
Kioxia warns Uncle Sam: Be careful what you wish for with China sanctions
Kioxia warns Uncle Sam: Be careful what you wish for with China sanctionsNice NAND industry you have there, would be a shame if something happened to...
Kioxia warns Uncle Sam: Be careful what you wish for with China sanctions
Kioxia warns Uncle Sam: Be careful what you wish for with China sanctionsNice NAND industry you have there, would be a shame if something happened to...
Government by Gmail catches up with UK minister… who is reappointed anyway
Government by Gmail catches up with UK minister... who is reappointed anywayHome Secretary 'nominally in charge' of nation's security apologizes for breach of tech protocols The...
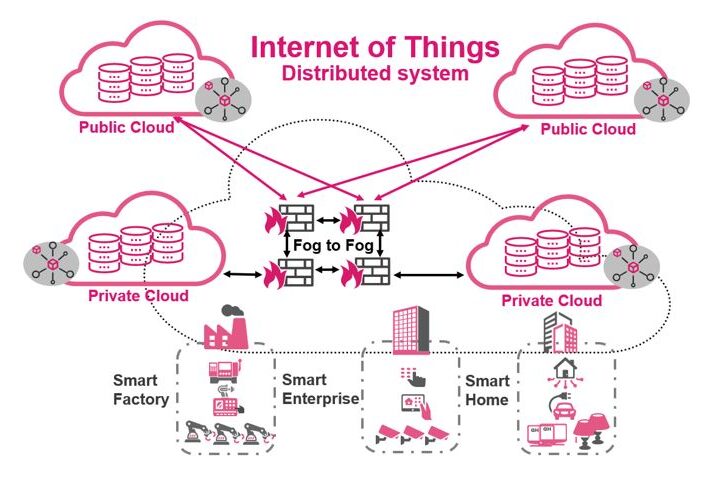
Challenges of the monolithic and distributed IoT realms
Challenges of the monolithic and distributed IoT realmsAntoinette Hodes is a Check Point Solutions Architect for the EMEA region and an Evangelist with the Check Point...
Government by Gmail catches up with UK minister… who is reappointed anyway
Government by Gmail catches up with UK minister... who is reappointed anywayHome Secretary 'nominally in charge' of nation's security apologizes for breach of tech protocols The...
OpenSSL downgrades horror bug after week of panic, hype
OpenSSL downgrades horror bug after week of panic, hypeRelax, there's more chance of Babbage coming back to life to hack your system than this flaw being...
OpenSSL downgrades horror bug after week of panic, hype
OpenSSL downgrades horror bug after week of panic, hypeRelax, there's more chance of Babbage coming back to life to hack your system than this flaw being...
Dropbox admits 130 of its private GitHub repos were copied after phishing attack
Dropbox admits 130 of its private GitHub repos were copied after phishing attackPersonal info and data safe, stolen code not critical, apparently Dropbox has said it...
Dropbox admits 130 of its private GitHub repos were copied after phishing attack
Dropbox admits 130 of its private GitHub repos were copied after phishing attackPersonal info and data safe, stolen code not critical, apparently Dropbox has said it...
Ritz cracker giant settles bust-up with insurer over $100m+ NotPetya cleanup
Ritz cracker giant settles bust-up with insurer over $100m+ NotPetya cleanupDeal could 'upend the entire cyber-insurance ecosystem and make it almost impossible to get meaningful cyber...
Ritz cracker giant settles bust-up with insurer over $100m+ NotPetya cleanup
Ritz cracker giant settles bust-up with insurer over $100m+ NotPetya cleanupDeal could 'upend the entire cyber-insurance ecosystem and make it almost impossible to get meaningful cyber...