Snatch group claims to have hacked military provider HENSOLDT FranceThe Snatch ransomware group claims to have hacked HENSOLDT France, a company specializing in military and defense electronics. The Snatch ransomware...
Day: November 1, 2022
Detecting Text4Shell (CVE-2022-42889), Critical RCE in Apache Commons Text
Detecting Text4Shell (CVE-2022-42889), Critical RCE in Apache Commons Text Threat actors don’t sleep, and cyber defenders cannot sleep a wink either to keep up with emerging...
RomCom Backdoor Detection: Cyber Attack on Ukrainian State Bodies Attributed to Cuba Ransomware Operators aka Tropical Scorpius (UNC2596) Group
RomCom Backdoor Detection: Cyber Attack on Ukrainian State Bodies Attributed to Cuba Ransomware Operators aka Tropical Scorpius (UNC2596) Group In May 2022, Cuba ransomware maintainers resurfaced...
VMware warns of the public availability of CVE-2021-39144 exploit code
VMware warns of the public availability of CVE-2021-39144 exploit codeVMware warned of the availability of a public exploit for a recently addressed critical remote code execution...
Actively exploited Windows Mark-of-the-Web zero-day received an unofficial patch
Actively exploited Windows Mark-of-the-Web zero-day received an unofficial patchAn unofficial patch for an actively exploited flaw in Microsoft Windows that allows to bypass Mark-of-the-Web (MotW) protections....
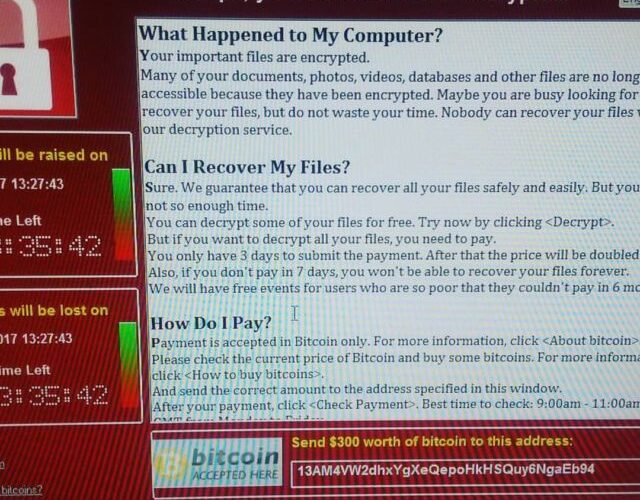
Wannacry, the hybrid malware that brought the world to its knees
Wannacry, the hybrid malware that brought the world to its kneesReflecting on the Wannacry ransomware attack, which is the lesson learnt e why most organizations are...
Five Play Store Droppers Target 200 Banking and Cryptocurrency Wallets Apps
Five Play Store Droppers Target 200 Banking and Cryptocurrency Wallets AppsFive malicious apps that combined have over 130,000 installations on Android devices have been discovered in...
EU Copper Giant Aurubis Hit by Cyberattack
EU Copper Giant Aurubis Hit by CyberattackIT systems belonging to the German copper producer Aurubis have been forcibly shut down after suffering a cyberattack on October 28th. Aurubis is...
What Is a DNS Server? Definition, Purpose, Types of DNS Servers, and Their Safety
What Is a DNS Server? Definition, Purpose, Types of DNS Servers, and Their SafetyA ‘DNS server’, also known as ‘name server’ or ‘domain name system server’...
Who Is Responsible for Developing a Cybersecurity Culture?
Who Is Responsible for Developing a Cybersecurity Culture?Creating a cybersecurity culture starts in the board room. However, this is only half of the answer to the...
German Student Behind One of the Country’s Biggest Dark Web Markets
German Student Behind One of the Country’s Biggest Dark Web MarketsBKA – Germany’s Federal Criminal Police Office announced the detainment of a 22-year-old student in Bavaria,...
Sigma2SaveLives: Equip Yourself with Curated Sigma Rules While Donating to Save Lives in Ukraine
Sigma2SaveLives: Equip Yourself with Curated Sigma Rules While Donating to Save Lives in Ukraine On April 4, 2022, SOC Prime launched Sigma2SaveLives charity subscription with 100%...
SOC Prime Achieves SOC 2 Type II Compliance for the Second Year in a Row
SOC Prime Achieves SOC 2 Type II Compliance for the Second Year in a Row Independent Audit Once Again Verifies SOC Prime’s Compliance with the SOC...
Russia’s Invasion of Ukraine Lays Ground for a New Era of Cyberwarfare
Russia’s Invasion of Ukraine Lays Ground for a New Era of CyberwarfareRussia is known to be the world’s leading hacking superpower for a reason. The country...
PURPLEURCHIN Campaign Detection: A New Crypto Mining Operation Massively Abuses GitHub Actions and Other Popular Free CI/CD Service Accounts
PURPLEURCHIN Campaign Detection: A New Crypto Mining Operation Massively Abuses GitHub Actions and Other Popular Free CI/CD Service Accounts With crypto mining attacks significantly increasing over...
Scared Of Your Own Shadow IT? Addressing The Top Security Concern Around SaaS Adoption
Scared Of Your Own Shadow IT? Addressing The Top Security Concern Around SaaS AdoptionBy Uri Haramati, Co-Founder and CEO of Torii The pandemic struck, and organizations...
Twilio reveals hackers compromised its systems a month earlier than previously thought
Twilio reveals hackers compromised its systems a month earlier than previously thoughtCloud communications firm Twilio reveals that it fell victim to a voice phishing attack in...
Extortion fears after hacker stole patient files from Dutch mental health clinics
Extortion fears after hacker stole patient files from Dutch mental health clinicsPatients of Dutch mental health clinics are being warned that their personal records have fallen...
Accused ‘Raccoon’ Malware Developer Fled Ukraine After Russian Invasion
Accused ‘Raccoon’ Malware Developer Fled Ukraine After Russian InvasionA 26-year-old Ukrainian man is awaiting extradition from The Netherlands to the United States on charges that he...
Tackling the Growing and Evolving Digital Attack Surface: 2022 Midyear Cybersecurity Report
Tackling the Growing and Evolving Digital Attack Surface: 2022 Midyear Cybersecurity ReportThis blog entry highlights the threats that dominated the first six months of the year,...
Addressing Ransomware in Hospitals & Medical Devices
Addressing Ransomware in Hospitals & Medical DevicesRansomware attacks have been on the rise in recent years, and hospitals are increasingly becoming targets. In many cases, these...
Convergent Evolution: SP 800-213, the Federal Profile, and the IoT Cybersecurity Catalog
Convergent Evolution: SP 800-213, the Federal Profile, and the IoT Cybersecurity CatalogNIST has been engaged for several years in developing guidance for Internet of Things (IoT)...
Threat Actors Target AWS EC2 Workloads to Steal Credentials
Threat Actors Target AWS EC2 Workloads to Steal CredentialsWe found malicious samples attempting to steal Amazon Elastic Compute Cloud (EC2) Workloads' access keys and tokens via...
Utility Metrics for Differential Privacy: No One-Size-Fits-All
Utility Metrics for Differential Privacy: No One-Size-Fits-AllIn previous posts we discussed different ways to implement differential privacy, each of which offers some trade-off between privacy and...
Privacy-Enhancing Cryptography to Complement Differential Privacy
Privacy-Enhancing Cryptography to Complement Differential PrivacyIn previous posts we discussed many aspects of differential privacy: what it is, what it is useful for, and how it...
Hot Topics in Consumer Cybersecurity Labeling – Our December 2021 Workshop
Hot Topics in Consumer Cybersecurity Labeling – Our December 2021 WorkshopOn May 12, 2021 the White House released an Executive Order (EO) on Improving the Nation’s...
How to deploy machine learning with differential privacy
How to deploy machine learning with differential privacyWe are delighted to introduce the final guest authors in our blog series, Nicolas Papernot and Abhradeep Thakurta, research...
From Bounty to Exploit: Observations About Cybercriminal Contests
From Bounty to Exploit: Observations About Cybercriminal ContestsFrom articles to hackathons, cybercriminals are resorting to crowdsourcing to find more ways to exploit systems. In this blog,...
Less Is More: Why One Antivirus Software Is All You Need
Less Is More: Why One Antivirus Software Is All You Need Personal devices and the information they carry are incredibly valuable to their owners. It is...
NIST Launches New International Cybersecurity and Privacy Resources Website
NIST Launches New International Cybersecurity and Privacy Resources WebsiteEvery day, NIST cybersecurity and privacy resources are being used throughout the world to help organizations manage cybersecurity...