Optus cyber-attack: how do you know if your identity has been stolen and what will happen to your data?After a massive data breach potentially exposed the...
Month: September 2022
Optus Falls Victim to Security Breach
Optus Falls Victim to Security BreachAustralian mobile operator Optus is investigating a security breach after they spotted “unauthorized access” to former and current customers’ personal data....
8 mistakes CIOs make and how to avoid them
8 mistakes CIOs make and how to avoid themFrom driving transformative change, to sharing insights into the political nature of the role, IT leaders and advisors...
Standards: The CPSO’s Best Friend
Standards: The CPSO’s Best FriendWorkshop Shines Light on Role of Standards in Cybersecurity for IoT What do Chief Product Security Officers (CPSOs) want to make their...
Morgan Stanley Sanctioned for Exposing Information of 15 Million Customers
Morgan Stanley Sanctioned for Exposing Information of 15 Million CustomersOn Tuesday, September 20, 2022, The Securities and Exchange Commission (SEC) revealed that Morgan Stanley financial services...
Telepathic Declassification
Telepathic DeclassificationFormer President Trump recently suggested that the sitting President simply needs to “think” something is declassified in order to declassify it. Is there a cascade...
Multi-Million Dollar Global Credit Card Scam Exposed
Multi-Million Dollar Global Credit Card Scam ExposedA massive global multi-million dollar scam, operating since 2019, has been uncovered. The number of victims is in the range...
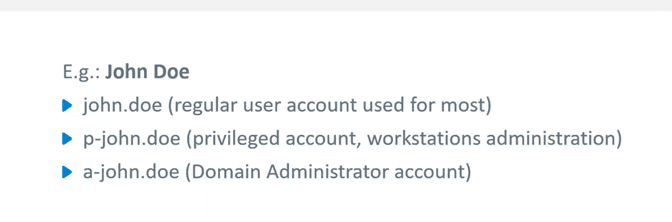
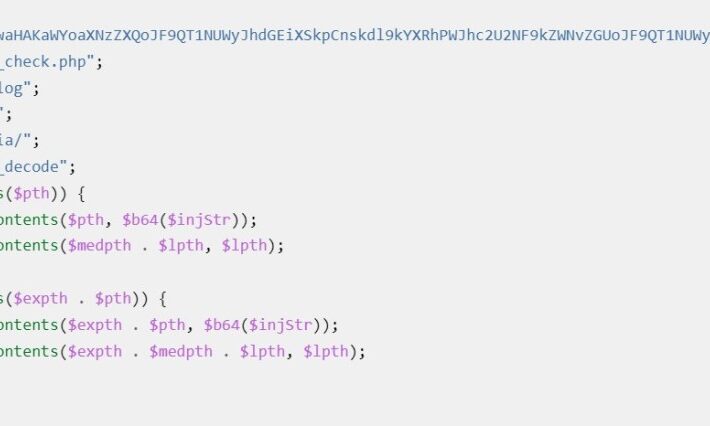
Active Directory Attack Scenarios: The Path from Printer to Domain Admin
Active Directory Attack Scenarios: The Path from Printer to Domain AdminThe post Active Directory Attack Scenarios: The Path from Printer to Domain Admin appeared first on...
How Russians Are Reacting to Putin’s Conscription Gamble
How Russians Are Reacting to Putin’s Conscription GambleReal-time data from Russian social media platforms and related illicit communities is vital to understanding the domestic public response...
WEBINAR: Bundling Up: The Importance of Layering Offensive Security Solutions
WEBINAR: Bundling Up: The Importance of Layering Offensive Security SolutionsThe post WEBINAR: Bundling Up: The Importance of Layering Offensive Security Solutions appeared first on Digital Defense....
Mobile Ransomware: The Next Step for Cybercriminals
Mobile Ransomware: The Next Step for Cybercriminals Targeting smartphones started to be increasingly appealing to cybercriminals as these devices become more and more important in users’...
Seven-Year Mobile Surveillance Campaign Targets Uyghurs
Seven-Year Mobile Surveillance Campaign Targets UyghursScarlet Mimic group uses over 20 Android malware variantsLeer másScarlet Mimic group uses over 20 Android malware variants
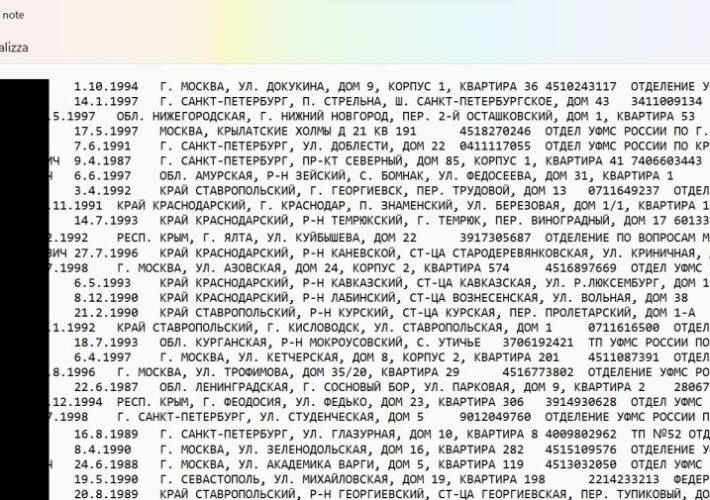
Australian Telecoms company Optus discloses security breach
Australian Telecoms company Optus discloses security breachAustralian telecoms company Optus disclosed a data breach, threat actors gained access to former and current customers. Optus, one of...
AttachMe: a critical flaw affects Oracle Cloud Infrastructure (OCI)
AttachMe: a critical flaw affects Oracle Cloud Infrastructure (OCI)A critical vulnerability in Oracle Cloud Infrastructure (OCI) could be exploited to access the virtual disks of other...
Details of Over 300,000 Russian Reservists Leaked, Anonymous Claims
Details of Over 300,000 Russian Reservists Leaked, Anonymous ClaimsThe group claims the individuals are likely to be mobilized by the Russian government to fight in UkraineLeer...
Surge in Magento 2 template attacks exploiting the CVE-2022-24086 flaw
Surge in Magento 2 template attacks exploiting the CVE-2022-24086 flawSansec researchers warn of a surge in hacking attempts targeting a critical Magento 2 vulnerability tracked as...
5 ways to grow the cybersecurity workforce
5 ways to grow the cybersecurity workforceThe demand for cybersecurity professionals has surged over the past decade. According to (ISC)2’s 2020 Cybersecurity Workforce Study, while the...
CISA adds Zoho ManageEngine flaw to its Known Exploited Vulnerabilities Catalog
CISA adds Zoho ManageEngine flaw to its Known Exploited Vulnerabilities CatalogCISA added a security flaw in Zoho ManageEngine, tracked as CVE-2022-35405, to its Known Exploited Vulnerabilities Catalog. The...
Daniel Stori’s ‘The Ketchup Gun’
Daniel Stori’s ‘The Ketchup Gun’ via Daniel Stori, crafting comics at turnoff.us! Permalink The post Daniel Stori’s ‘The Ketchup Gun’ appeared first on Security Boulevard. Leer...
Cyber Mercenary Group Void Balaur Continues Hack-For-Hire Campaigns
Cyber Mercenary Group Void Balaur Continues Hack-For-Hire CampaignsVoid Balaur campaigns in 2022 targeted various industries across the US, Russia and UkraineLeer másVoid Balaur campaigns in 2022...
Anonymous claims to have hacked the website of the Russian Ministry of Defense
Anonymous claims to have hacked the website of the Russian Ministry of DefenseThe popular collective Anonymous claims to have hacked the website of the Russian Ministry...
Best 10 SIEM Tools to Fuel Up Your Threat-Hunting Grind
Best 10 SIEM Tools to Fuel Up Your Threat-Hunting GrindThreat-hunting has proven to be the most efficient, field-proven countermeasure against cyber threats. Action items based on...
Ransomware operators might be dropping file encryption in favor of corrupting files
Ransomware operators might be dropping file encryption in favor of corrupting filesRansomware started out many years as scams where users were being tricked into paying fictitious...
The Increasing Insider Risk of Emerging Healthcare Technology
The Increasing Insider Risk of Emerging Healthcare TechnologyEarlier this month, the Health Sector Cybersecurity Coordination Center (HC3) issued a grave warning about the security implications of...
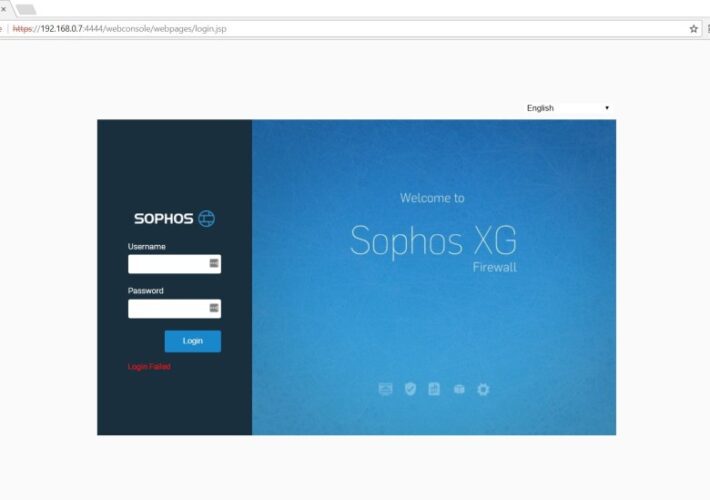
Sophos warns of a new actively exploited flaw in Firewall product
Sophos warns of a new actively exploited flaw in Firewall productSophos warns that a critical code injection security vulnerability in its Firewall product is actively exploited...
Weekly Update 313
Weekly Update 313I came so close to skipping this week's video. I'm surrounded by family, friends and my amazing wife to be in only a couple...
Hackers Deploy Malicious OAuth Apps to Compromise Email Servers, Spread Spam
Hackers Deploy Malicious OAuth Apps to Compromise Email Servers, Spread SpamThe spam emails were sent to trick recipients into signing up for fake paid subscriptionsLeer másThe...
A third of Australian population likely affected in Optus cyberattack
A third of Australian population likely affected in Optus cyberattackAustralia’s second largest telecommunications provider, Optus, revealed it suffered a cyberattack where data from customers have possibly...
Air Force Upgrades Digital Modernization Strategy to “As a Service” Model
Air Force Upgrades Digital Modernization Strategy to "As a Service" ModelThe transition will be carried out through three procurements to be awarded before the end of...
Hey WeLiveSecurity, how does biometric authentication work?
Hey WeLiveSecurity, how does biometric authentication work?Your eyes may be the window to your soul, but they can also be your airplane boarding pass or the...