US Police Deployed Obscure Smartphone Tracking Tool With No WarrantsIt would allow police to search billions of mobile device-based records, including GPS dataLeer másIt would allow...
Month: September 2022
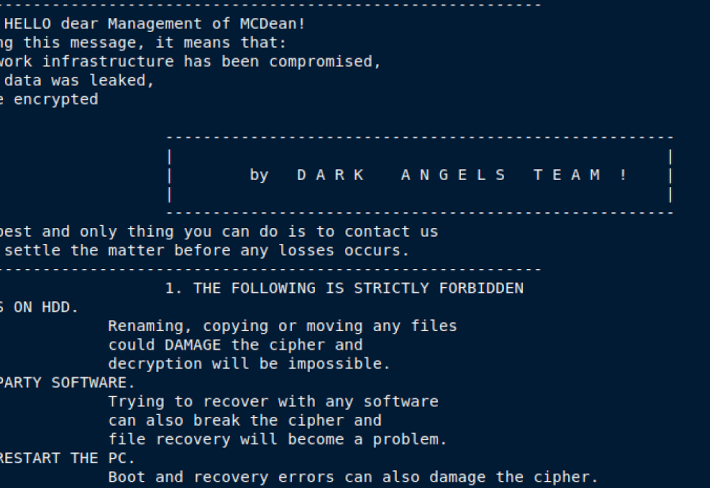
Another Ransomware For Linux Likely In Development
Another Ransomware For Linux Likely In DevelopmentUptycs researchers recently spotted a new Linux ransomware that appears to be under active development. The Uptycs Threat Research team...
Google rolled out emergency fixes to address actively exploited Chrome zero-day
Google rolled out emergency fixes to address actively exploited Chrome zero-dayGoogle rolled out emergency fixes to address a vulnerability in the Chrome web browser that is...
Samsung discloses a second data breach this year
Samsung discloses a second data breach this yearElectronics giant Samsung has confirmed a new data breach after some of its US systems were compromised in July....
Security Affairs newsletter Round 382
Security Affairs newsletter Round 382A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs free for you in...
IRS mistakenly published confidential info for roughly 120K taxpayers
IRS mistakenly published confidential info for roughly 120K taxpayersThe Internal Revenue Service (IRS) mistakenly leaked confidential information for approximately 120,000 taxpayers. Bad news for approximately 120,000...
Alleged Iranian threat actors leak the code of their CodeRAT malware
Alleged Iranian threat actors leak the code of their CodeRAT malwareThe author of the remote access trojan (RAT) CodeRAT has leaked the source code of its...
A New Cyberattack on TAP Air Portugal
A New Cyberattack on TAP Air PortugalOn Thursday night, August 25, TAP Air Portugal was the victim of a cyberattack claimed by the Ragnar Locker ransomware...
Weekly Update 311
Weekly Update 311Well, after a crazy amount of work, a lot of edits, reflection, and feedback cycles, "Pwned" is almost here: This better be a sizzling...
AgentTesla Spyware Massively Distributed in Phishing Campaigns Targeting Ukrainian, Austrian, and German Organizations
AgentTesla Spyware Massively Distributed in Phishing Campaigns Targeting Ukrainian, Austrian, and German Organizations On August 30 and 31, 2022, CERT-UA revealed a burst of adversary activity...
Linux Systems Are a More Common Target as the Attack Surface Expands
Linux Systems Are a More Common Target as the Attack Surface ExpandsOften overlooked by security experts, Linux systems become a more common target for cybercriminals. Aiming...
Anomaly Detection In Cybersecurity For Dummies
Anomaly Detection In Cybersecurity For DummiesThe pandemic has changed the way businesses operate, and one of these changes is that companies across the […] The post...
Source Code Protection Market
Source Code Protection MarketDo we need backup software for DevOps ecosystems? By Marta Przybylska, Marketing Manager, GitProtect.io / Xopero Software […] The post Source Code...
EVERYONE is Part of the Security Team and Solution
EVERYONE is Part of the Security Team and SolutionBy Jim Nitterauer, Director of Information Security, Graylog Often, companies approach cybersecurity as a technology problem, forgetting that...
The Future of Cybersecurity in SaaS
The Future of Cybersecurity in SaaSBy Sean Malone, Chief Information Security Officer, Demandbase Security for Software-as-a-Service (SaaS) solutions has been a priority since […] The post...
ModernLoader Bot Detection: Spreads via Bogus Amazon Gift Cards, Compromises Users in Eastern Europe
ModernLoader Bot Detection: Spreads via Bogus Amazon Gift Cards, Compromises Users in Eastern Europe ModernLoader bot, aka Avatar bot, is a .NET remote access trojan with...
Over 900K Kubernetes clusters are misconfigured! Is your cluster a target?
Over 900K Kubernetes clusters are misconfigured! Is your cluster a target?Graham Cluley Security News is sponsored this week by the folks at Teleport. Thanks to the...
FBI issues warning after crypto-crooks steal $1.3 billion in just three months
FBI issues warning after crypto-crooks steal $1.3 billion in just three monthsAmid a wave of hacks which has cost investors billions of dollars worth of cryptocurrency,...
Clever Phishing Scam Uses Legitimate PayPal Messages
Clever Phishing Scam Uses Legitimate PayPal MessagesBrian Krebs is reporting on a clever PayPal phishing scam that uses legitimate PayPal messaging. Basically, the scammers use the...
Montenegro is the Victim of a Cyberattack
Montenegro is the Victim of a CyberattackDetails are few, but Montenegro has suffered a cyberattack: A combination of ransomware and distributed denial-of-service attacks, the onslaught disrupted...
Friday Squid Blogging: Squid Images
Friday Squid Blogging: Squid ImagesiStock has over 13,000 royalty-free images of squid. As usual, you can also use this squid post to talk about the security...
Smartphone Alternatives: Ease Your Way into Your Child’s First Phone
Smartphone Alternatives: Ease Your Way into Your Child’s First Phone “But everyone else has one.” Those are familiar words to a parent, especially if you’re having...
Summertime Blues: TA558 Ramps Up Attacks on Hospitality, Travel Sectors
Summertime Blues: TA558 Ramps Up Attacks on Hospitality, Travel SectorsContenido de la entradaLeer másProofpoint News Feed
New Golang Ransomware Agenda Customizes Attacks
New Golang Ransomware Agenda Customizes AttacksA new piece of ransomware written in the Go language has been targeting healthcare and education enterprises in Asia and Africa....
Buzzing in the Background: BumbleBee, a New Modular Backdoor Evolved From BookWorm
Buzzing in the Background: BumbleBee, a New Modular Backdoor Evolved From BookWormIn March 2021, we investigated a backdoor with a unique modular architecture and called it...
Microsoft Edge 105 won’t start due to old group policy – How to fix
Microsoft Edge 105 won't start due to old group policy - How to fixThe new Microsoft Edge 105 is not starting for many Windows users due...
Researchers Spot Snowballing BianLian Ransomware Gang Activity
Researchers Spot Snowballing BianLian Ransomware Gang ActivityThe operators of the emerging cross-platform ransomware BianLian increased their command and control infrastructure this month, indicating an acceleration in...
‘May the best spy win’: Australia’s intelligence chiefs open up on cyber threats – and feminism
‘May the best spy win’: Australia’s intelligence chiefs open up on cyber threats – and feminismASD boss says cyber environment has become ‘messy’ since Ukraine conflict...
Your Digital User Experience is Great. But Could it Cost You Millions?
Your Digital User Experience is Great. But Could it Cost You Millions? The shift online, with all of its benefits to businesses and consumers, also introduces serious...
LogRhythm Announces More Details of Its In-Person Annual Security User Conference
LogRhythm Announces More Details of Its In-Person Annual Security User ConferenceRhythmWorld 2022 Releases Full Agenda LogRhythm, the company helping busy and lean security operations teams save...