Revisiting Cybersecurity’s 2022 IPO PipelineAssessing the impact of the current economic downturn on cybersecurity's IPO candidates. The post Revisiting Cybersecurity’s 2022 IPO Pipeline appeared first on...
Month: September 2022
Defense and Development: Key points from The Complete Guide to Application Security for PCI-DSS
Defense and Development: Key points from The Complete Guide to Application Security for PCI-DSSThe increasing popularity of online payment systems results from the world’s gradual transition...
Microsoft Discover Severe ‘One-Click’ Exploit for TikTok Android App
Microsoft Discover Severe ‘One-Click’ Exploit for TikTok Android AppMicrosoft on Wednesday disclosed details of a now-patched "high severity vulnerability" in the TikTok app for Android that...
Apple Releases iOS Update for Older iPhones to Fix Actively Exploited Vulnerability
Apple Releases iOS Update for Older iPhones to Fix Actively Exploited VulnerabilityApple on Wednesday backported security updates to older iPhones, iPads, and iPod touch devices to...
Over 1,800 Android and iOS Apps Found Leaking Hard-Coded AWS Credentials
Over 1,800 Android and iOS Apps Found Leaking Hard-Coded AWS CredentialsResearchers have identified 1,859 apps across Android and iOS containing hard-coded Amazon Web Services (AWS) credentials,...
How does Identity Verification enhance Remote Onboarding in Telecommunications?
How does Identity Verification enhance Remote Onboarding in Telecommunications?One of the most cutthroat customer-facing sectors is telecommunications. Most customers make their choice of a new supplier...
Infra Used in Cisco Hack Also Targeted Workforce Management Solution
Infra Used in Cisco Hack Also Targeted Workforce Management SolutionThe attack infrastructure used to target Cisco in the May 2022 incident was also employed against an attempted compromise...
URGENT! Apple slips out zero-day update for older iPhones and iPads
URGENT! Apple slips out zero-day update for older iPhones and iPadsPatch as soon as you can - that recent WebKit zero-day affecting new iPhones and iPads...
Complete Guide on Retail & ECommerce Software Development
Complete Guide on Retail & ECommerce Software DevelopmentRetail and eCommerce software is the backbone of any business. It’s where the money is made and where consumers...
UK Imposes Tough New Cybersecurity Rules for Telecom Providers
UK Imposes Tough New Cybersecurity Rules for Telecom ProvidersOfcom will be able to issue fines for non-compliance of up to 10% of turnoverLeer másOfcom will be...
Evil Corp and Conti Linked to Cisco Data Breach, eSentire Suggests
Evil Corp and Conti Linked to Cisco Data Breach, eSentire SuggestsThe firm said the tools used to attack Cisco were also deployed to compromise one of...
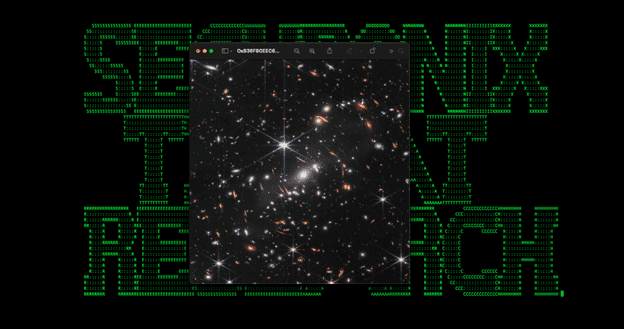
Golang-based Malware Campaign Relies on James Webb Telescope’s Image
Golang-based Malware Campaign Relies on James Webb Telescope's ImageInitial infection begins with a phishing email containing a Microsoft Office attachmentLeer másInitial infection begins with a phishing...
Microsoft Finds Account Takeover Bug in TikTok
Microsoft Finds Account Takeover Bug in TikTokVulnerability impacted social media firm’s Android appLeer másVulnerability impacted social media firm’s Android app
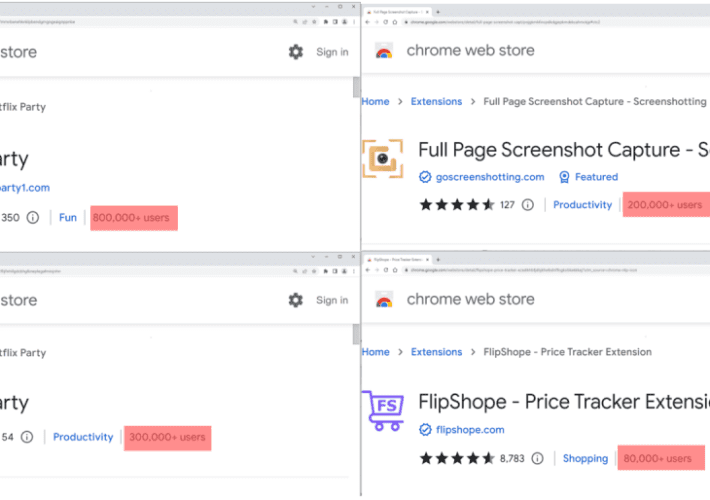
Experts spotted five malicious Google Chrome extensions used by 1.4M users
Experts spotted five malicious Google Chrome extensions used by 1.4M usersResearchers spotted 5 malicious Google Chrome extensions used to track users’ browsing activity and profit of...
Threat actors breached the network of the Italian oil company ENI
Threat actors breached the network of the Italian oil company ENIItalian oil giant Eni was hit by a cyber attack, attackers compromised its computer networks, but...
GO#WEBBFUSCATOR campaign hides malware in NASA’s James Webb Space Telescope image
GO#WEBBFUSCATOR campaign hides malware in NASA’s James Webb Space Telescope imageA malware campaign tracked as GO#WEBBFUSCATOR used an image taken from NASA’s James Webb Space Telescope...
Detected Cyber-Threats Surge 52% in 1H 2022
Detected Cyber-Threats Surge 52% in 1H 2022Trend Micro warns of Linux-based ransomwareLeer másTrend Micro warns of Linux-based ransomware
How to take control over your digital legacy
How to take control over your digital legacyDo you have a plan for what will happen to your digital self when you pass away? Here’s how...
Standards Body Publishes Guidelines for IoT Security Testing
Standards Body Publishes Guidelines for IoT Security TestingDocument will help testers create benchmarks for security productsLeer másDocument will help testers create benchmarks for security products
A flaw in TikTok Android app could have allowed the hijacking of users’ accounts
A flaw in TikTok Android app could have allowed the hijacking of users’ accountsMicrosoft discovered a vulnerability in the TikTok app for Android that could lead...
FBI is helping Montenegro in investigating the ongoing cyberattack
FBI is helping Montenegro in investigating the ongoing cyberattackA team of cybersecurity experts from the US FBI will help the authorities in Montenegro to investigate the...
Apple released patches for recently disclosed WebKit zero-day in older iPhones and iPads
Apple released patches for recently disclosed WebKit zero-day in older iPhones and iPadsApple released new security updates for older iPhone and iPad devices addressing recently fixed WebKit...
START Confirms Data Breach
START Confirms Data BreachSTART (start.ru), a Russian media streaming platform, has confirmed the rumors that emerged on Sunday, August 28, about a data breach. The cybercriminals...
Genshin Impact Ransomware Infection: Adversaries Abuse the Anti-Cheat Driver
Genshin Impact Ransomware Infection: Adversaries Abuse the Anti-Cheat Driver Genshin Impact, a popular open-world action RPG, is leveraged to spread ransomware. Threat actors abuse mhyprot2.sys, a...
Smashing Security podcast #287: Lost in translation, spiders, and slapping tortillas
Smashing Security podcast #287: Lost in translation, spiders, and slapping tortillasWe’re back from our summer break as we ask how did a cryptomining campaign stay unspotted...
Final Thoughts on Ubiquiti
Final Thoughts on UbiquitiLast year, I posted a series of articles about a purported “breach” at Ubiquiti. My sole source for that reporting was the person...
Aussies Fear Snakes, Spiders and Getting Hacked
Aussies Fear Snakes, Spiders and Getting Hacked Fears and phobias. We all have them. But what are your biggest ones? I absolutely detest snakes but spiders...
Our Quest: Advancing Product Labels to Help Consumers Consider Cybersecurity
Our Quest: Advancing Product Labels to Help Consumers Consider CybersecurityFor many decades, consumers have relied on labels to help them make decisions about which products to...
Microsoft found TikTok Android flaw that let hackers hijack accounts
Microsoft found TikTok Android flaw that let hackers hijack accountsMicrosoft found and reported a high severity flaw in the TikTok Android app in February that allowed attackers...
Ragnar Locker ransomware claims attack on Portugal’s flag airline
Ragnar Locker ransomware claims attack on Portugal's flag airlineThe Ragnar Locker ransomware gang has claimed an attack on the flag carrier of Portugal, TAP Air Portugal,...